Firmware Vulnerability Management
Contents
- Overview
- Viewing Firmware Vulnerabilities in your network
- Viewing CVE ID details and taking remediation measures
- How Network Configuration Manager categorizes firmware vulnerabilities
- Firmware Vulnerability DB sync
- Vulnerability DB sync for closed networks
- Firmware Vulnerability Reports and advanced CVE search
Note: For firmware vulnerability sync, we get data from Network Configuration Manager's ManageEngine database: https://ncm.nimbuspop.com. Customers must allow access to the domains "https://ncm.nimbuspop.com" and "https://www.manageengine.com" from NCM installed server in order to retrieve the data.
Overview
Firmware vulnerabilities can put your business and your customers’ sensitive data at risk, leading to easy entry to hackers, diminished sales, reputation loss and penalties. In order to avoid these mishaps, it is important to identify firmware vulnerabilities and take corrective measures regularly.
With Network Configuration Manager, you can manage firmware vulnerability by identifying potential vulnerabilities in your network devices and upgrade device firmware remotely. Network Configuration Manager works in accordance with NIST (National Institute of Standards and Technology) by fetching firmware vulnerability data and correlating it with the network devices which are currently managed in your infrastructure. At present, Network Configuration Manager helps to manage firmware vulnerability for vendors in the table below.
| Vendor | Version support |
|---|---|
| Citrix |
Supports from 126130 |
| Mikrotik | |
| Checkpoint | |
| F5 | |
| Bluecoat | |
| InfoBlox | |
| RiverBed | |
| Huawei | |
| Netgear | |
| Hpe | |
| Netscreen | |
| Cisco |
Supports from 124098 |
| Juniper | |
| Palo Alto | |
| HP | |
| Aruba | |
| Arista | |
| Fortinet | |
| Dell |
Viewing Firmware Vulnerabilities in your network
In Firmware Vulnerabilities page, Network Configuration Manager lists out all the vulnerabilities in your network and the number of devices affected by those vulnerabilities. You can view the details of that vulnerability associated to a particular CVE ID and immediately carry out the remediation methods.
Follow the instructions in order to see the severity of vulnerabilities and the devices which are vulnerable:
- Click on the the "Firmware Vulnerability" tab.
- Under "Firmware Vulnerabilities", you will be able to see all the vulnerabilities in your network.
- Right next to all vulnerabilities, you will be able to see the categorization of those vulnerabilities based on their severity level.
- NCM groups vulnerabilities as Critical, Important, Moderate, Low and Unrated.
- If you wish to view the devices belonging to a particular category of severity, click on the severity to view all the vulnerabilities and the devices associated with it.
- Network Configuration Manager categorizes the severity of vulnerabilities based on the "Base score" given by the person who reports the vulnerability.
- Further drilling down, you can see the CVE ID, devices having that vulnerability and the reference URLs to resolve the vulnerability.
Viewing CVE ID details and taking remediation measures
By clicking on the CVE ID, you can you can get in-depth information about the firmware vulnerability. Follow the instructions to see the CVE details in Network Configuration Manager:
- Click on Firmware Vulnerability tab and choose "All Vulnerabilities"
- You will be able to see all the vulnerabilities listed along with the CVE id.
- Click on the CVE id to view the details of the vulnerability.
- On clicking the CVE id, you will be able to able to view the CVE details.
- In the CVE details page, you can see the date the CVE id was published and last modified.
- You can also see the summary which shows information about what the vulnerability is and on which device the vulnerability was reported first.
- You can also see reference URLs, which provides the optimal resolution measures for the vulnerability and a comment section which allows users to add a required statement.
- Also, you can see a status bar with options to mark the status of the vulnerability. You can also edit the status anytime and save the status by clicking the save icon.
How Network Configuration Manager categorizes firmware vulnerabilities
Network Configuration Manager categorizes the severity of vulnerabilities based on the "Base score" which is calculated based on a few metrics like Exploitability Metrics(Attack, Complexity, Authentication) and Impact Metrics(Confidentiality, Integrity, Availability). Here is the split up of how the severity is categorized:
- Base score 9.0 - 10 - Critical
- Base score 7.0 - 8.9 - Important
- Base score 4.0 - 6.9 - Moderate
- Base score 0 - 3.9 - Low
Firmware Vulnerability DB sync
Vulnerability data from NIST can be synced with the DB of Network Configuration Manager. Users can set a time of schedule in order to sync data on a daily basis. When a schedule time is set, the synchronization of vulnerability data happens automatically at the exact time of schedule. Network Configuration Manager also allows you to edit/change the time of schedule as per your convenience. If no schedule time is set, sync happens every night at 2 a.m by default.
The data is received from Network Configuration Manager's ManageEngine database: https://ncm.nimbuspop.com, which needs to be allowed by users to get data of vulnerabilities.
If you wish to update the Vulnerability data in the NCM UI immediately instead of the scheduled time, you can give the "Update Now" option. When "Update Now" is given, the latest vulnerability data will be updated in the NCM DB.
Follow the instructions in order to run a daily schedule for synchronizing vulnerability data:
- Click on "Firmware Vulnerability" tab and select "Sync Vulnerability DB" option.
- In the tab that opens, you will be able to see when the DB was last updated with the vulnerability data and also the next schedule time.
- You will also be able to see the whether the vulnerability sync was a success/failure.
- ext to "Daily Scheduled Run" you will be allowed to enter a schedule time or change the existing schedule time.
- Once the schedule time is given, click on the save icon.
- If you wish to immediately update the vulnerability data in NCM, you can select "Update Now" option.
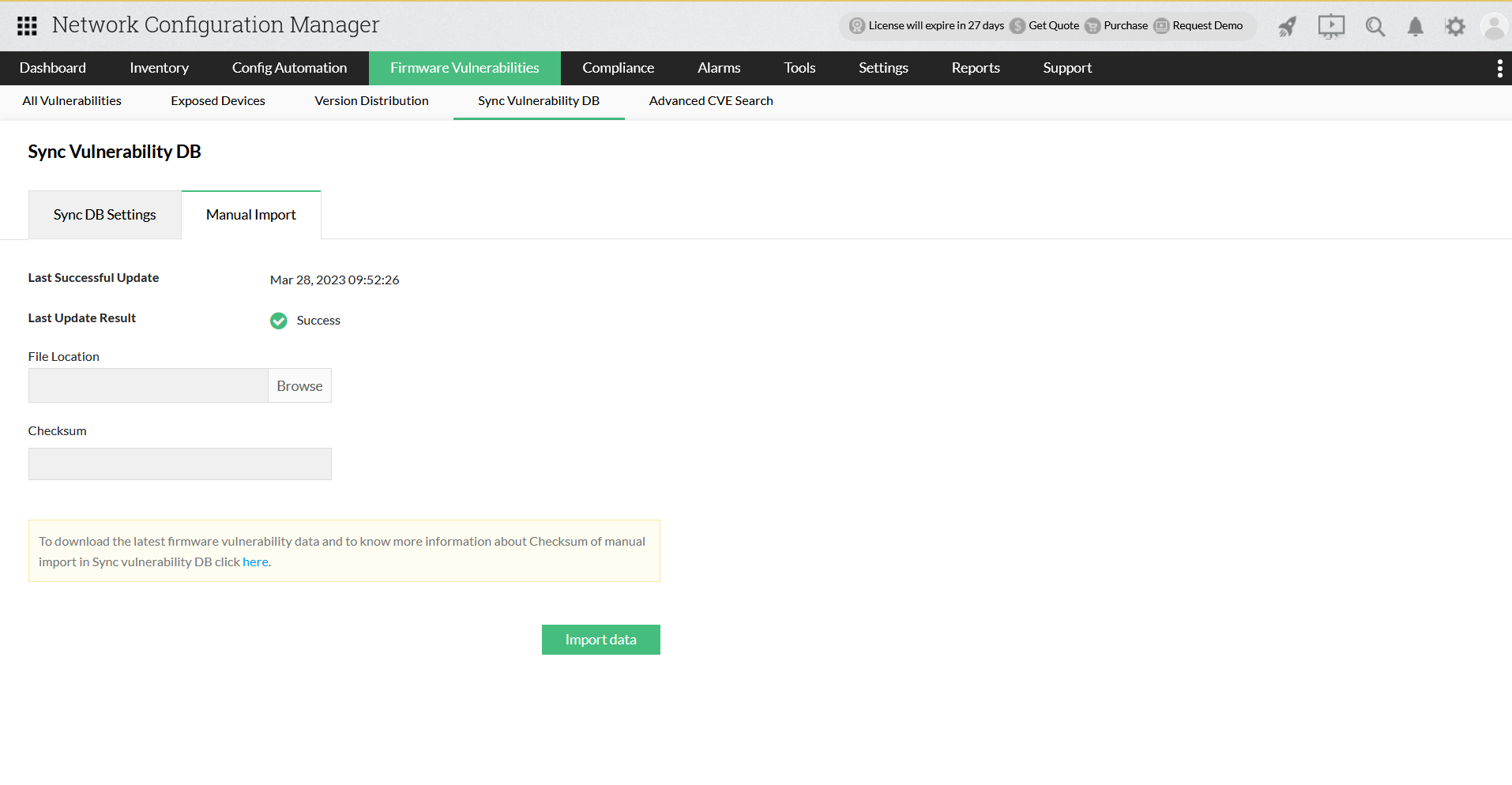
Vulnerability DB sync for closed networks
If your network is closed, you will not be able to update vulnerability database automatically using firmware vulnerability scanning with data from NIST vulnerability management. In that case, you can go for a manual import of vulnerability data.
- A "Checksum" feature has been developed to verify the file's authenticity and integrity. Please enter the checksum given below in the input box provided in Network Configuration Manager's UI.
- Import the downloaded file in Network Configuration Manager UI. Once you import the new file, the previous dump will be deleted and replaced with the latest data.
Note: Modification of the imported dump by the customer may lead to corruption of vulnerability dump present in Network Configuration Manager.
Firmware Vulnerability Reports and advanced CVE search
Network Configuration Manager provides reports on firmware vulnerability to help you gain clarity into the affected devices, its status and the remediation for the vulnerability. You can export the report as a PDF, CSV file or get the report via Email.
With "Advanced CVE search" you can globally search for all the vulnerabilities by searching using the vendor name, CVE ID, device OS number, version or a model. For eg: If you search "Cisco IOS 7000", all the vulnerabilities present in that particular model will be listed. On further clicking it, you will be able to see all the details of the vulnerability corresponding to a particular CVE ID. Follow the instructions to perform advanced CVE search in Network Configuration Manager:
- To perform an advanced CVE search, click on "Firmware Vulnerability" tab and select "Advanced CVE Search".
- In the tab that opens, you will be able to see a search bar.
- In the search bar, you can search for all the vulnerabilities by searching using the vendor name, CVE id, device OS number, version or a model.
- After a particular search term is given, click on "search" button.
- NCM will display the vulnerabilities associated to a particular vendor or a CVE id, globally.
- By clicking on a particular CVE id, you can view the details of the vulnerability linked to a particular CVE id.
Thus, Network Configuration Manager helps you achieve in-depth firmware vulnerability management of all the vulnerabilities in your network. Click here to know about firmware upgrade and firmware vulnerability widgets. Try out Network Configuration Manager using the 30-day free trial and see how you can manage vulnerabilities in your network!
Thank you for your feedback!