Remediating Cloud Entitlements' Risks from PAM360
With the Cloud Entitlements feature in PAM360, you can identify and address identity-related risks within your AWS account directly from the interface with ease. Any detected risks can be mitigated through a streamlined remediation process, and previously remediated risks can be effortlessly restored using the Revert functionality if needed. Refer to the section below for detailed steps on how to remediate or revert PAM360-defined risks within your AWS account identities.
By the end of this document, you will have a clear understanding of the steps involved in effectively remediating identity risks in your AWS account.
Additional Detail
Excessive Privileges and Shadow Admins risks in your AWS account can be remediated or reverted directly from the PAM360 interface. Whereas the remaining pre-defined risks can be remediated from the AWS interface using the detailed steps provided below.
1. Remediating Cloud Entitlements' Risks
The risk remediation options for identity - such as Users, User Groups, and Roles - are accessible in two main ways: through the respective identity tab or the Risks tab.
- Navigate to the Risks tab. On the displayed page, select any predefined risk that requires remediation. On the subsequent page, choose the relevant identity to remediate the associated risk.
- Alternatively, go directly to the respective identity tab (Users, User Groups, or Roles), use the filter dropdown to choose the specific risk, and select the identity needing remediation.
Once you have accessed the identity details in PAM360, remediation actions for the selected risk are available under the Risks & Remediation tab.
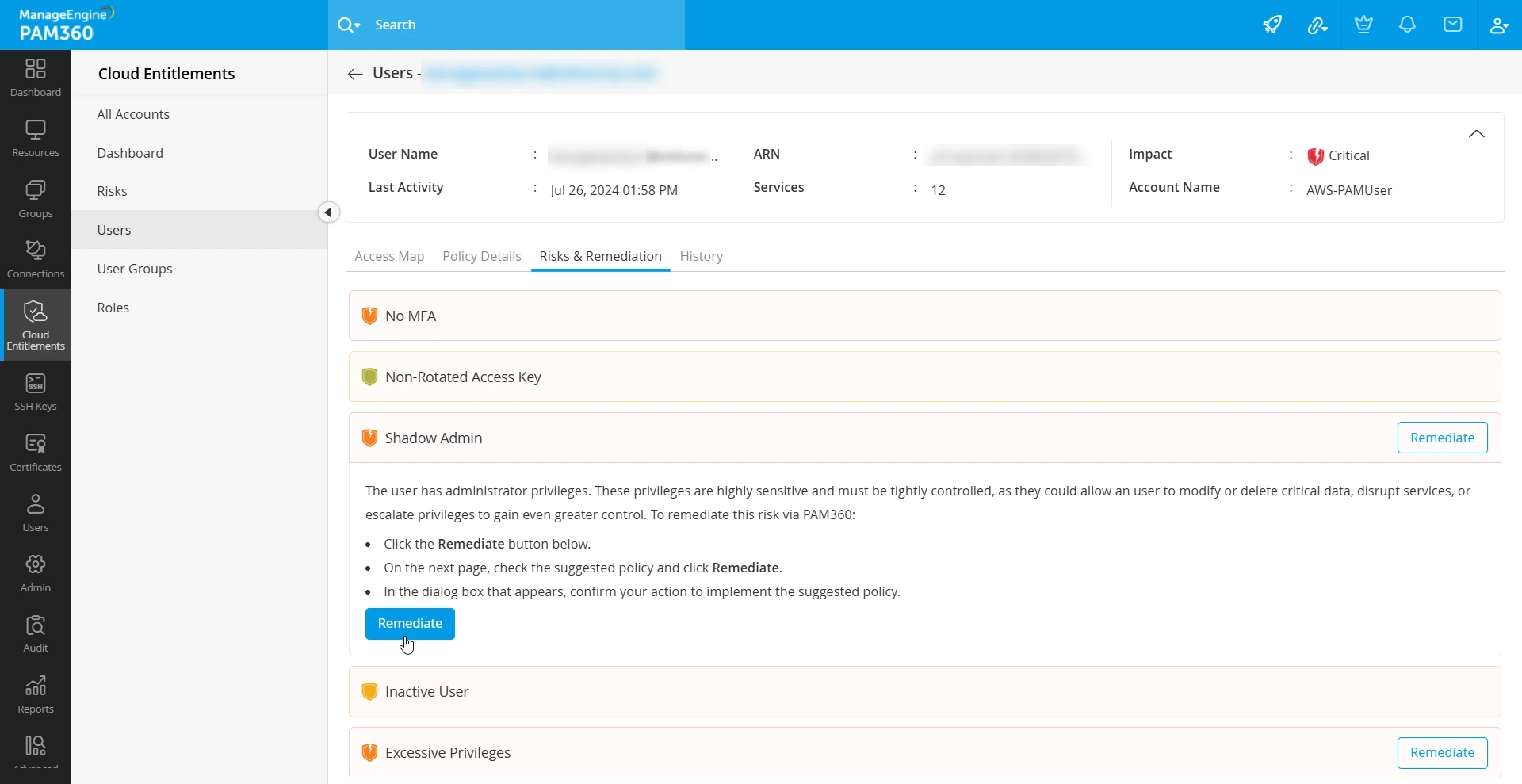
The following sections provide step-by-step instructions for remediating specific risks.
1.1 Remediating the Excessive Privileges Risk
The identities (IAM users and roles) possessing unused permissions are grouped under Excessive Privileges. Holding excess permissions will increase the risk of data exposure when an unauthorized identity gains access to the account. Refer to the section below for the remediation information for the excessive privileges risk.
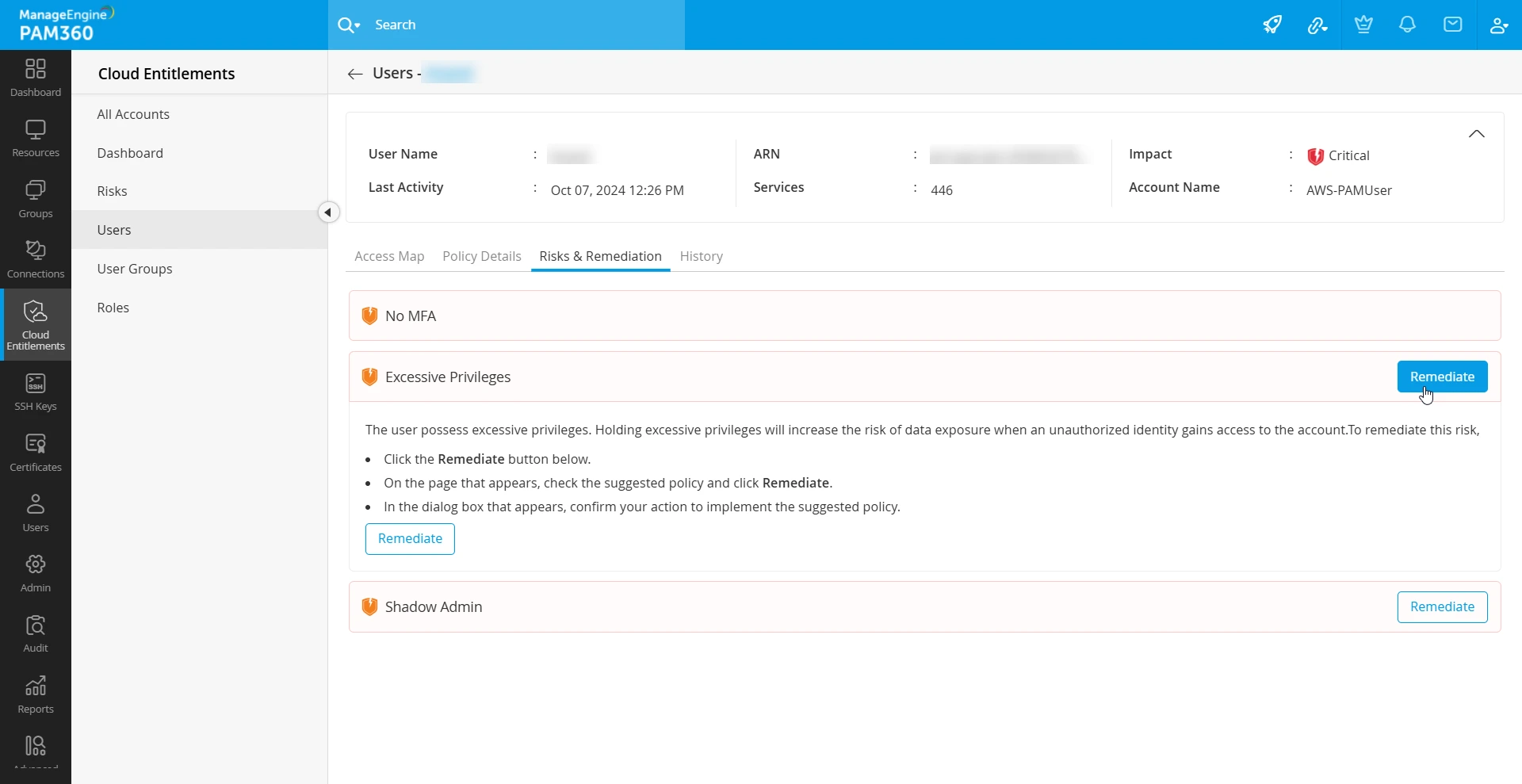
To automatically remediate the excessive privileges risk from PAM360 for the IAM users or roles in your AWS account, perform the following steps:
- From the Risks & Remediation tab, select the Excessive Privileges risk and click the Remediate button.
- On the next page, you will find a comparison between the identity's currently attached IAM policy and the PAM360 recommended inline policy. This suggested inline policy retains only essential permissions, removing excessive or unused permissions based on activities tracked during the designated CloudTrail Event Retrieval period.
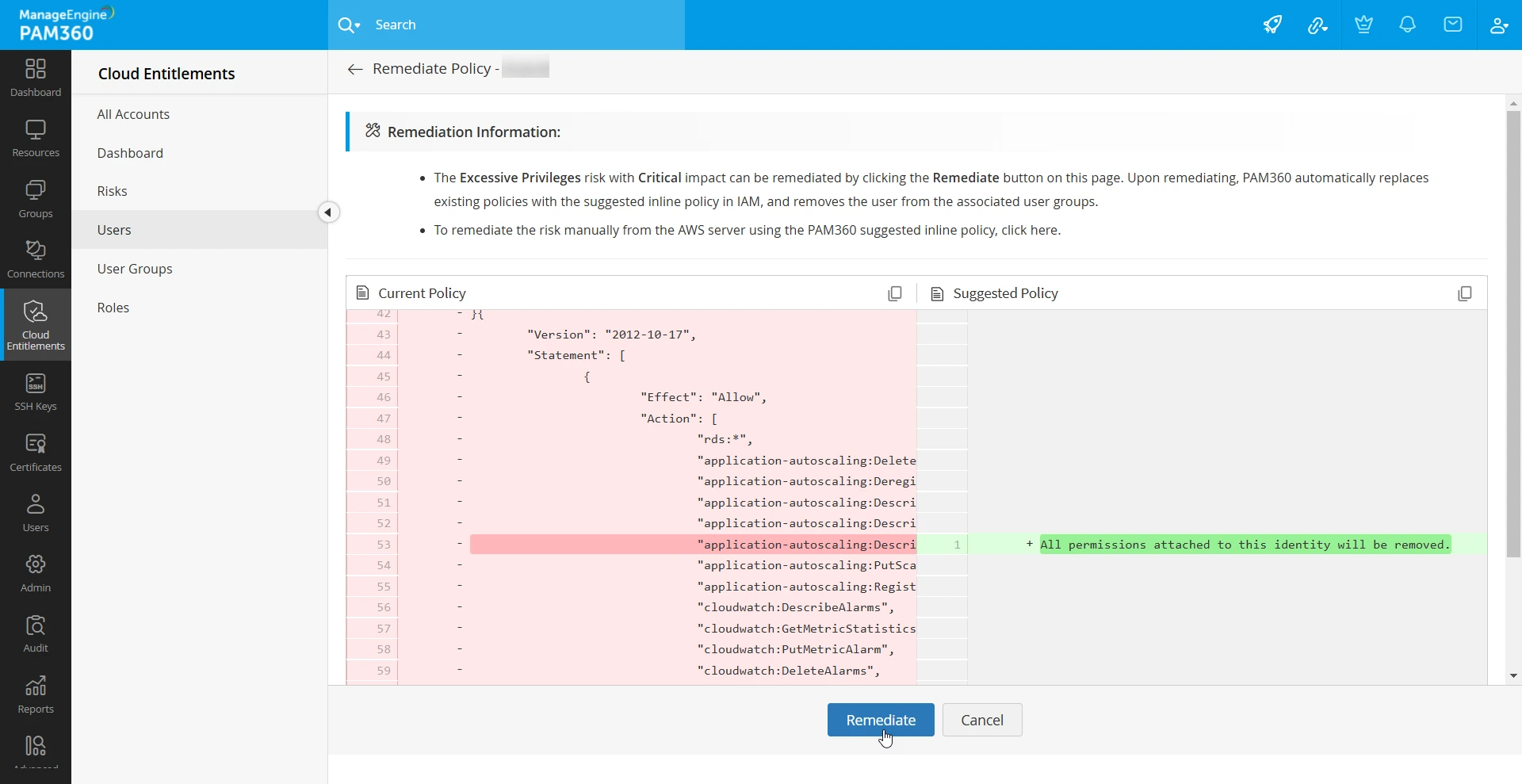
- Click the Remediate button at the bottom of the page.
- In the dialog box that appears, confirm your action to remediate the risk and click the Remediate button.
Upon remediation, PAM360 automatically replaces the existing policies with the suggested inline policy in IAM, adhering to the Principle of Least Privilege (PoLP).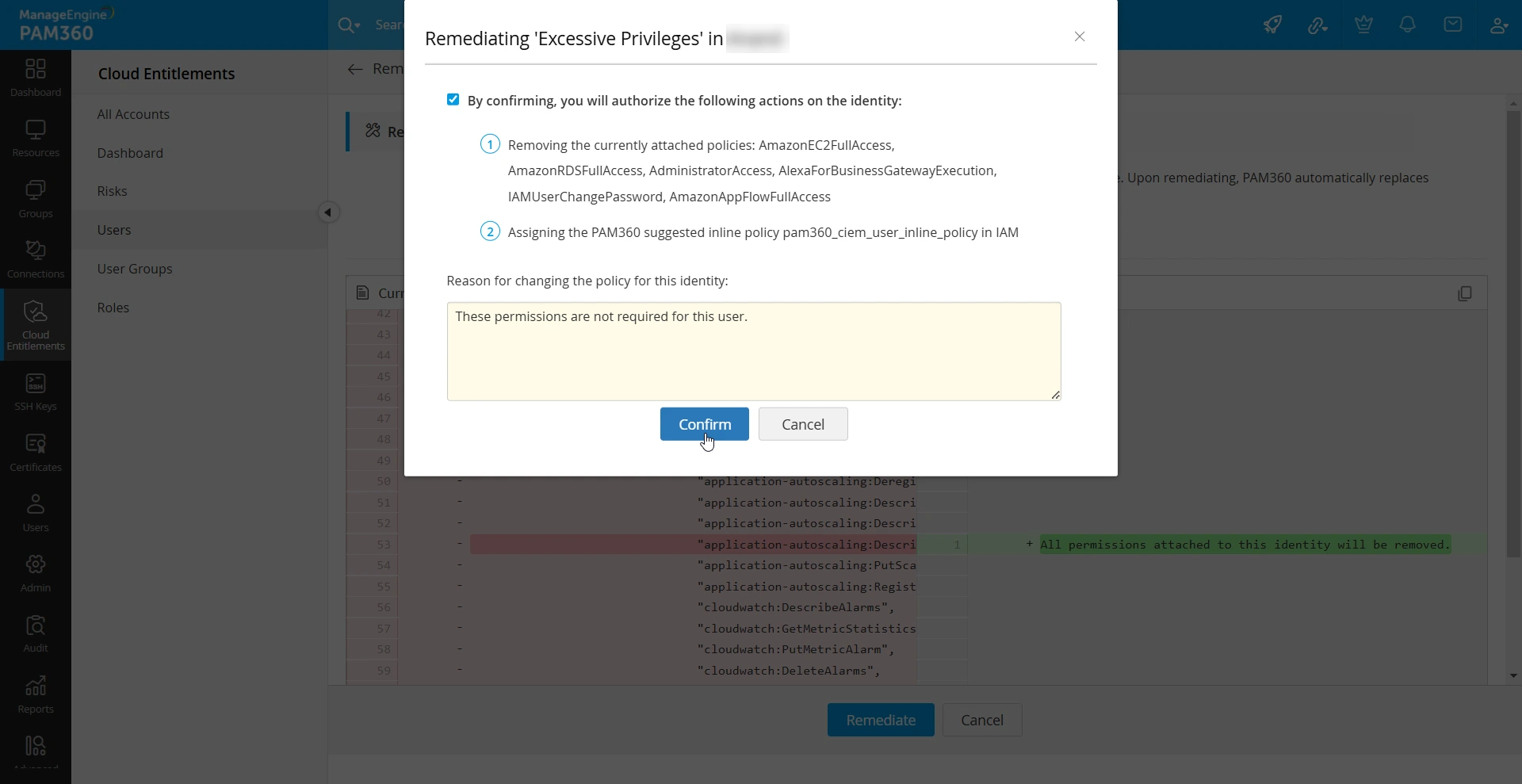
To remediate the risk manually from the AWS server using the PAM360 recommended inline policy, perform the following actions:
- Copy the PAM360 suggested inline policy from the remediation page.
Caution
Due to AWS inline policy constraints, the inline policy suggested by PAM360 includes policy delimiters (marked as <POLICY_DELIMITER> within the policy displayed in PAM360). When manually remediating the risk, separate the permissions in the copied policy and assign them as individual custom policies in AWS.
- Log in to your AWS console using administrator credentials.
- Navigate to the IAM dashboard and open the Permissions page for the identity.
- Detach all the existing policies and permissions for the IAM user or role.
- Select the option to create a new inline policy.
- Paste the copied PAM360 suggested inline policy in the JSON editor.
- Attach the newly created custom policy to the identity to complete the remediation process.
1.1.a Remediating Excessive Privileges Risk using AI-Powered Insights
Caution
To utilize the integrated AI platform to generate a policy suggestion for an excessive privilege risk associated with an identity, Cloud Entitlements Policy Suggestion should be enabled under the respective integration in the AI-Powered Insights. Explore this link for the detailed steps.
You can use the AI model integrated in your PAM360 environment to generate policy suggestions for the Excessive Privileges risk associated with an identity and generate a policy remediation summary that highlights how the suggested inline-AI policy revokes excessive privileges, ensuring that only just enough permissions are granted to the identity. Follow these steps to generate an AI-based IAM policy suggestion:
- From the Risks & Remediation tab, select the Excessive Privileges risk and click the Remediate button.
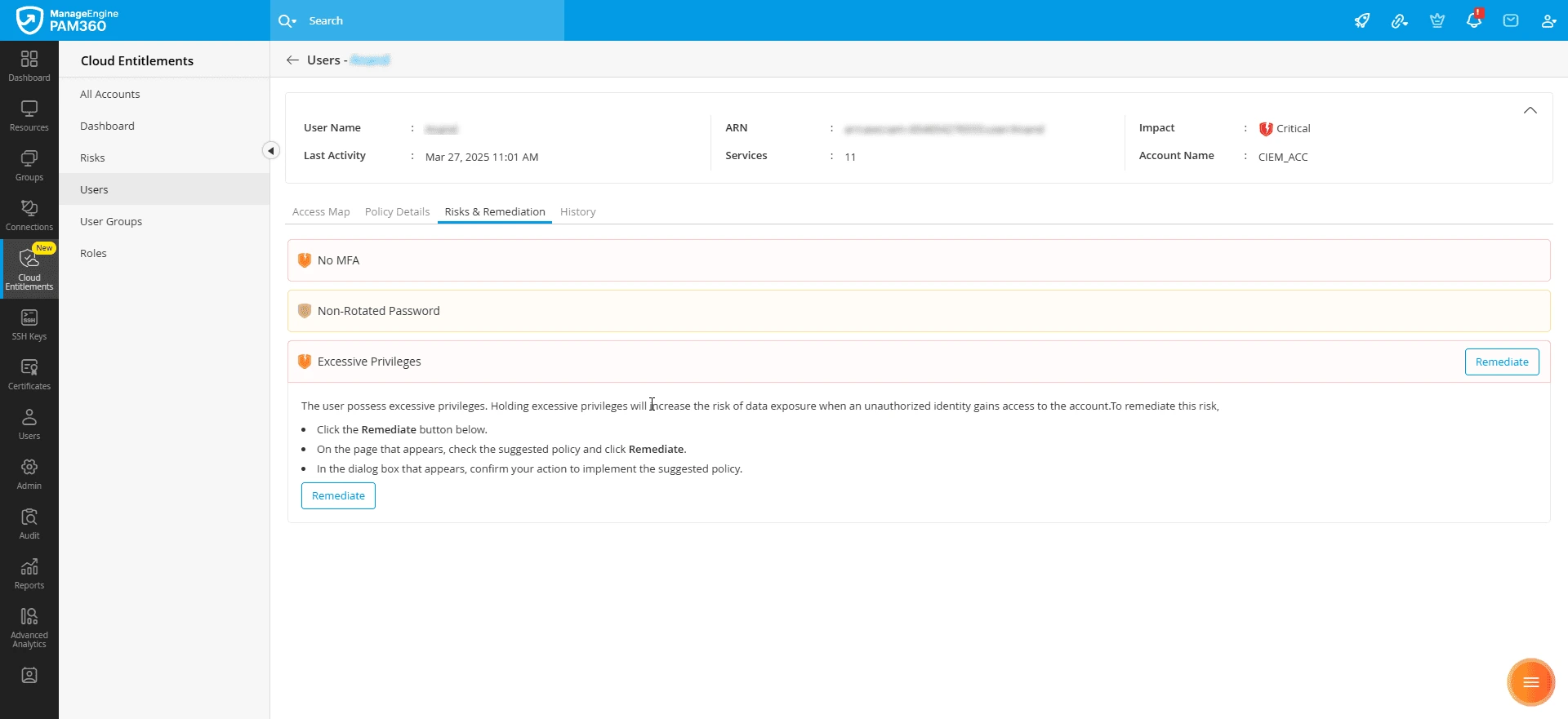
- On the Remediate Policy window, click the PAM360 drop-down button within the Suggested Policy section, and select OpenAI from the displayed options to generate an IAM policy suggestion using the integrated AI model.
Additional Detail
Only the users with the Generate AI Insights privilege can generate a recommended IAM policy for the excessive privileges risk associated with an identity using OpenAI.
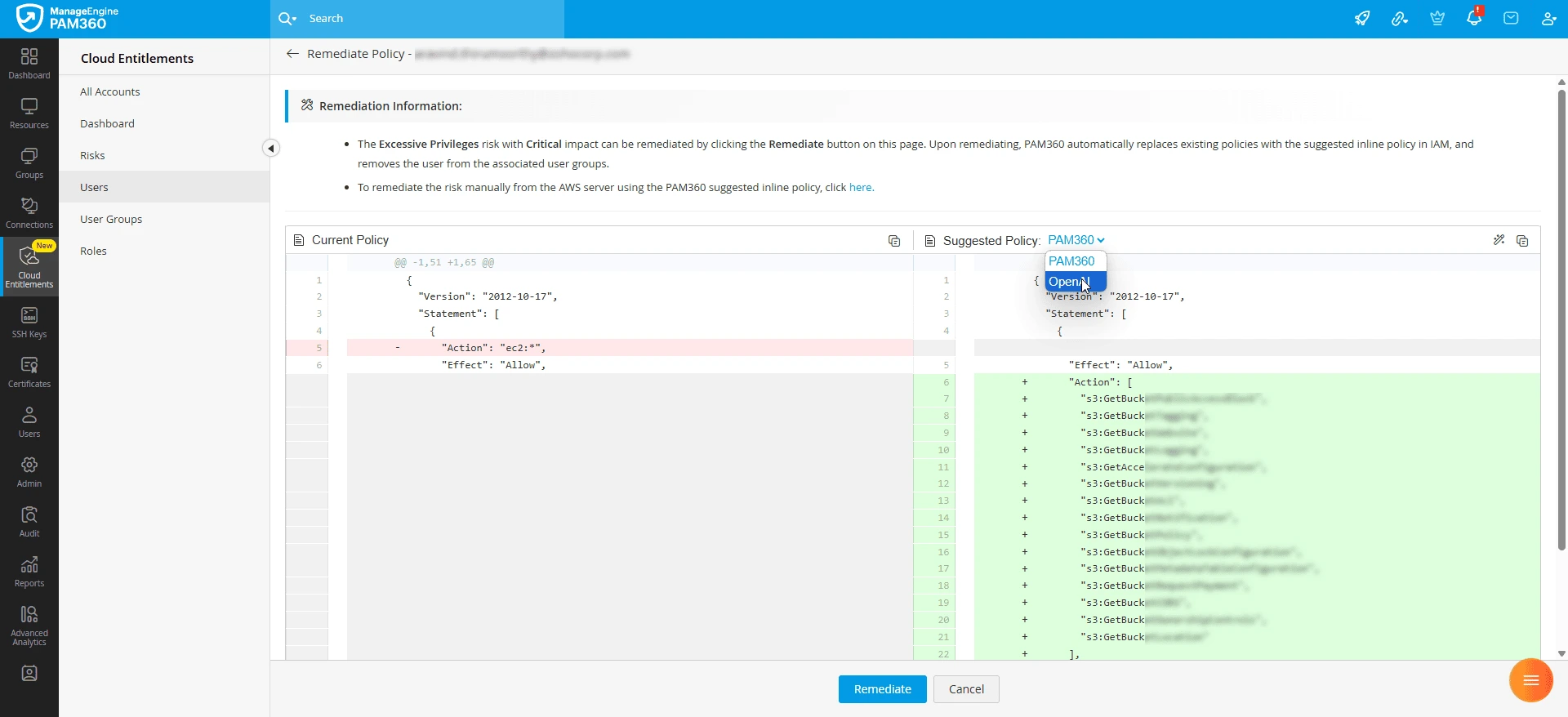
- Currently, PAM360 supports direct risk remediation from the Remediate Policy window only for the inline policies suggested by PAM360. If you choose to use an AI-suggested policy, the remediation must be performed manually from the AWS console.
- To remediate a risk using an AI-suggested policy, click the Copy button on the top pane of the Suggested Policy section to copy the inline-AI policy suggested by OpenAI and follow the procedure provided in this section starting from Step 2.
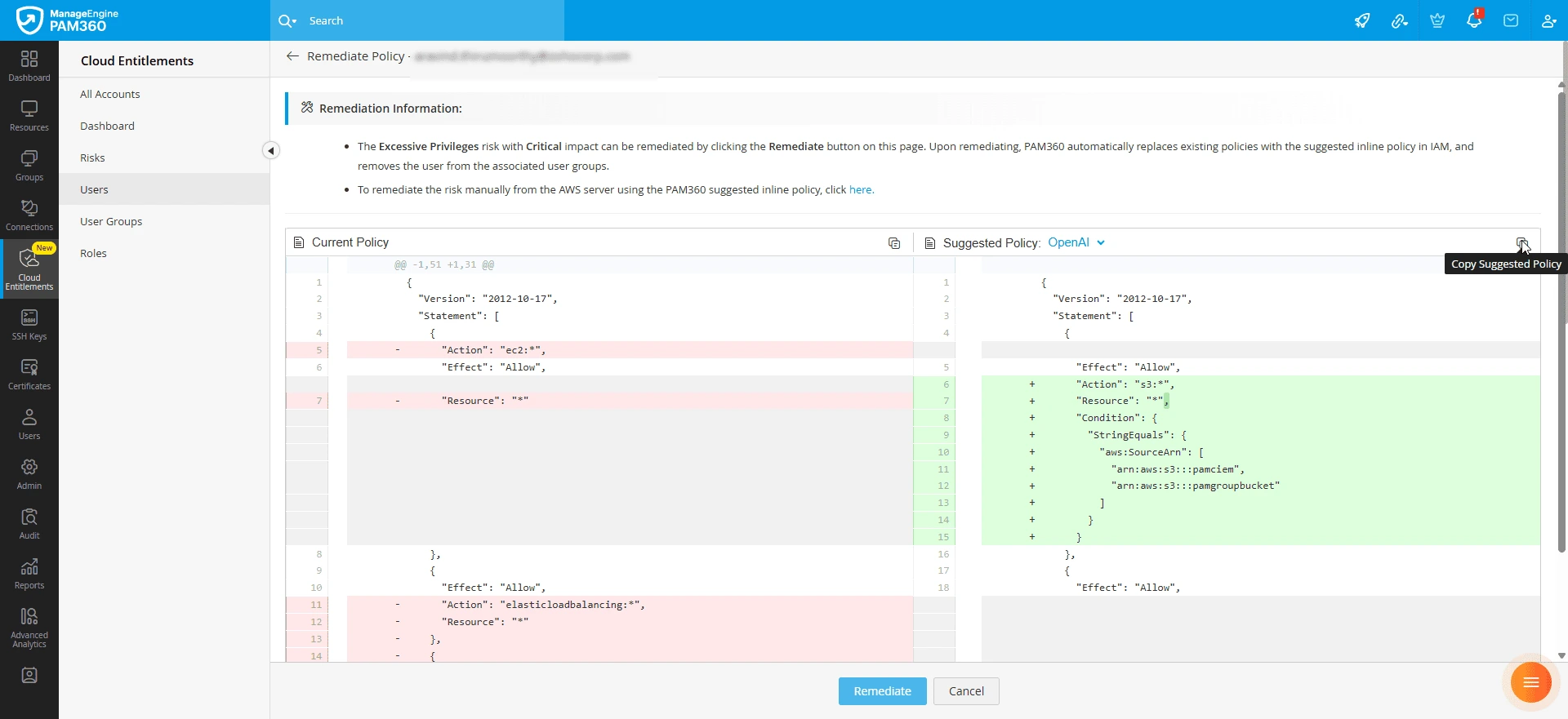
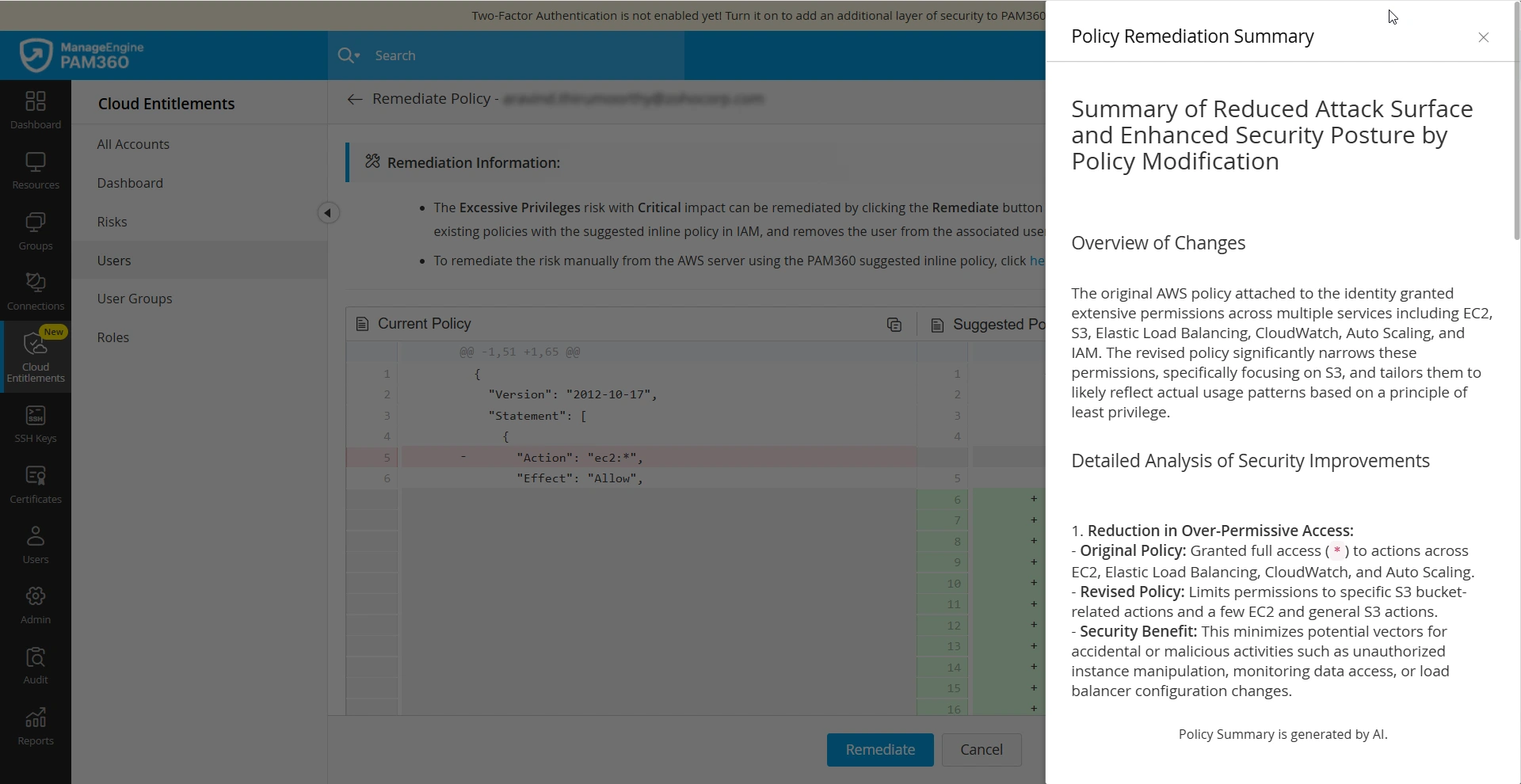
Additionally, PAM360 allows administrators to generate policy remediation summaries for IAM policies recommended by PAM360. Follow these steps to generate a policy remediation summary:
- Navigate to the Remediate Policy window and click the Policy Remediation Summary icon from the top pane of the Suggested Policy section.
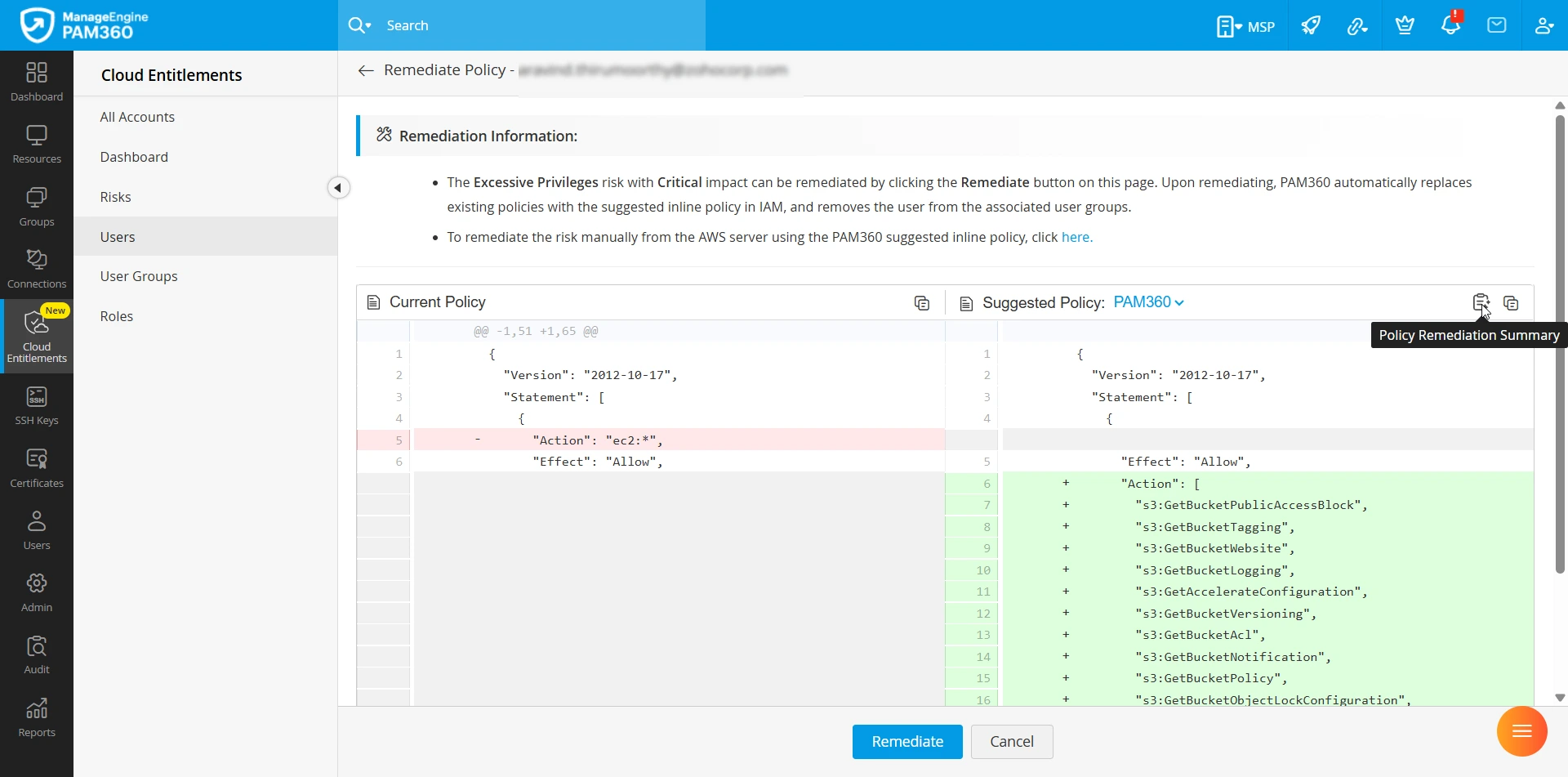
- After analyzing the currently attached IAM policy and the suggested IAM policy for the selected risk, the integrated AI model will provide a summary that highlights the differences between the current and suggested policies and how the suggested policy ensures that the identity contains only the just enough permissions, remediating the associated risk.
Caution
- Only the users with the Generate AI Insights privilege can generate a Policy Remediation Summary for the excessive privileges risk associated with an identity.
- The integrated AI platform may fail to generate policy summaries or policy suggestions if the input exceeds the token limit of the selected AI model.
1.2 Remediating the Shadow Admin Risk
To remediate the Shadow Admin risk from PAM360 for the IAM users, user groups or roles in your AWS account, perform the following steps:
- From the Risks & Remediation tab, select the Shadow Admin risk and click the Remediate button.

- On the page that appears, you can view the list of toxic permissions that grant administrative privileges to the identity and the PAM360 recommended inline policy to remediate the risk. The toxic permissions that are responsible for the Shadow Admin risk are classified into Individual Toxic Permissions, Toxic Permission Pairs, and Toxic Permission Triads. Refer to the table below for detailed information:
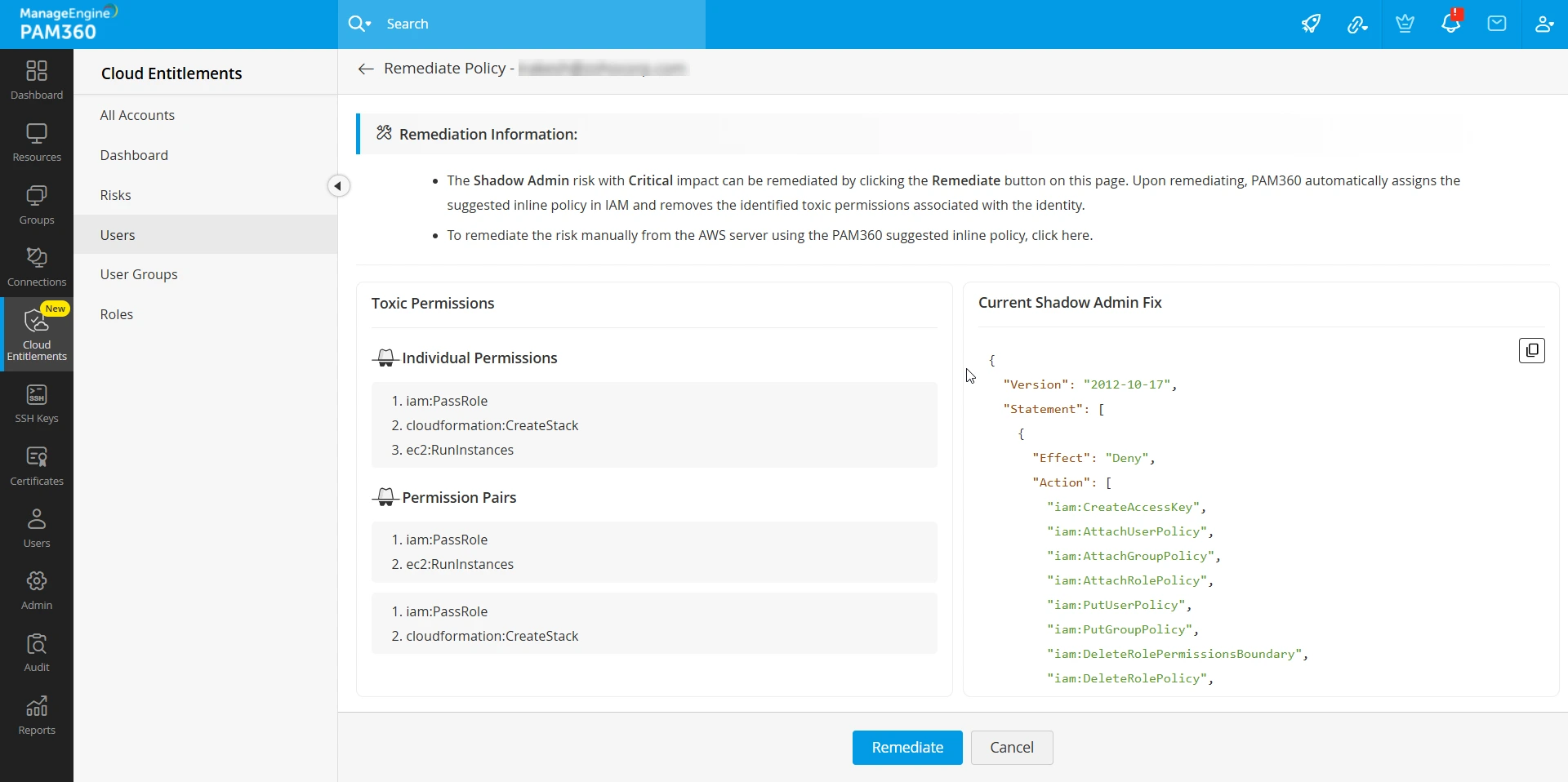
- iam:CreatePolicyVersion
- iam:SetDefaultPolicyVersion
- iam:CreateAccessKey
- iam:CreateLoginProfile
- iam:UpdateLoginProfile
- iam:AttachUserPolicy
- iam:AttachGroupPolicy
- iam:AttachRolePolicy
- iam:PutUserPolicy
- iam:PutGroupPolicy
- iam:PutRolePolicy
- iam:AddUserToGroup
- iam:UpdateFunctionCode
- iam:CreatePolicy
- iam:DeleteRolePermissionsBoundary
- iam:DeleteRolePolicy
- iam:DeleteUserPermissionsBoundary
- iam:DeleteUserPolicy
- iam:DetachRolePolicy
- iam:DetachUserPolicy
- iam:UpdateAssumeRolePolicy
sts:AssumeRole - iam:PassRole
glue:CreateDevEndpoint - glue:UpdateDevEndpoint
glue:GetDevEndpoint(s) - iam:PassRole
cloudformation:CreateStack - iam:PassRole
ec2:AssociateIamInstanceProfile - iam:PassRole
lambda:CreateFunction
lambda:InvokeFunction - iam:PassRole
lambda:CreateFunction
lambda:CreateEventSourceMapping - iam:PassRole
datapipeline:CreatePipeline
datapipeline:PutPipelineDefinition - iam:PassRole
iam:CreateInstanceProfile
iam:AddRoleToInstanceProfile - iam-PassRole
iam-RemoveRoleFromInstanceProfile
iam-AddRoleToInstanceProfile - Click the Remediate button at the bottom of the page.
- In the dialog box that appears, confirm your action and click the Remediate button.
| Terms | Toxic Permissions |
|---|---|
Individual Toxic Permissions | |
Toxic Permission Pairs | |
Toxic Permission Triads |
Upon remediation, the toxic permissions that grant the administrator privileges to the identity will get removed.
To remediate the Shadow Admin risk manually from the AWS server using the PAM360 recommended inline policy, perform the following actions:
- Copy the PAM360 suggested inline policy from the remediation page.
- Log in to your AWS console using administrator credentials.
- Navigate to the IAM dashboard and open the Permissions page for the identity (user, group, or role).
- Select the option to create a new custom policy.
- Paste the copied PAM360 suggested inline policy in the JSON editor.
- Attach the new custom policy to the identity to complete the remediation process.
1.3 Remediating the Non-Rotated Passwords Risk
After identifying the IAM users with non-rotated passwords in your AWS account using PAM360's Cloud Entitlements, you can remediate the risk by resetting password or enforcing password rotation on the next immediate login in AWS. This can be done either from the AWS console or AWS CLI. Refer to the sections below to remediate the risk.
To remediate the risk from the AWS console, perform the following steps:
- Log in to your AWS console using administrator credentials.
- Navigate to the IAM dashboard and select Users from the left pane.
- Select the IAM user from the list to whom you want to enforce password rotation on the next login.
- On the page that appears, click the Security credentials tab and navigate to the Console sign-in section.
- Click the Manage console access button. In the dialog box that appears, click Reset password.
- Under Console password, select either Autogenerated password or Custom password as required and click the Reset password button to reset the password.
- To enforce a policy for password rotation, tick the User must create new password at next sign-in checkbox instead of selecting an option beneath the Console password section and click the Reset password button.
To remediate the risk from the AWS CLI, update the user's password settings and mark the password as requires a reset upon the user's next login. To do so, execute the following command:
aws iam update-login-profile --user-name USERNAME --password-reset-required
1.4 Remediating the Non-MFA Users Risk
After identifying the users without MFA in your AWS account using PAM360's Cloud Entitlements, perform the following actions to enable MFA in the AWS server.
- Log in to your AWS console using a root user account or IAM user with administrative privileges.
- Click Services at the top pane and select IAM from the list.
- Select Users from the left pane and click the user account for which you want to enable MFA.
- Click the Security credentials tab and select Assign MFA device under the Multi-factor authentication (MFA) section.
- On the page that appears, enter a device name and select the authenticator app. Click Add MFA and complete the MFA setup for the IAM user.
For detailed instructions, refer to this document.
1.5 Remediating the Non-Rotated Access Keys Risk
To mitigate the risk posed by non-rotated access keys identified in AWS via PAM360 Cloud Entitlements, it is essential to rotate them. The key rotation process involves generating a new access key, associating it with the IAM user, and then securely deactivating and deleting the old, unrotated key. This process can be done directly via the AWS console or the AWS CLI, ensuring that access keys are regularly updated, thus enhancing security and reducing potential vulnerabilities associated with stale or compromised access keys.
To remediate the risk from the AWS console, perform the following steps:
- Log in to your AWS console and navigate to the IAM dashboard.
- Click the Users tab from the left pane and select the IAM user from the list.
- On the page that appears, switch to the Security credentials tab and click the Create access key button from the Access keys section.
- On the next page, select Other and click Next.
- Enter any description tag value and click the Create access key button.
- Click the Download .csv file button to save the new credentials.
- Update all application instances to use the newly created access key. Ensure this key is distributed across all systems that require access, reducing any risk of service disruption during rotation.
- Ensure that applications are functioning as expected with the new access key before deleting the old access key.
- Now, return to the user configuration page and navigate to Security credentials >> Access keys.
- Click the Actions dropdown beside the old access key and select Deactivate.
- Click the Actions dropdown again and select Delete.
- In the dialog box that appears, enter the access key ID to confirm the deletion and click the Delete button.
Now, you have rotated the access key for the IAM user. Remember to store the access key in a secure location.
To remediate the risk from the AWS CLI, execute the following commands:
- Execute the following command to generate a new access key for the user. This will provide a new access key ID and secret access key, which should be securely stored.Replace USERNAME with the actual IAM username.
aws iam create-access-key --user-name USERNAME
- Update all the application instances to use the newly created access key. Ensure this key is distributed across all systems that require access, reducing any risk of service disruption during rotation.
- Execute the following command to list the access keys associated with the user. This command will display all keys for the user, with each key's status as active or inactive.
aws iam list-access-keys --user-name USERNAME
- Once the new key is in use, disable the old access key by executing the following command.Replace <OLD_ACCESS_KEY_ID> with the actual key ID of the non-rotated access key.
aws iam update-access-key --access-key-id <OLD_ACCESS_KEY_ID> --status Inactive --user-name USERNAME
- Re-run the list-access-keys command to confirm that the old key is now inactive and the new key remains active.
aws iam list-access-keys --user-name USERNAME
- Ensure that applications are functioning as expected with the new access key before deleting the old access key.
- Once validated, permanently delete the inactive access key using the following command.
aws iam delete-access-key --access-key-id <OLD_ACCESS_KEY_ID> --user-name USERNAME
Refer to this AWS documentation for more detailed information.
Following any of the access key rotation methods ensures the security and integrity of AWS resources.
Additional Detail
PAM360 allows you to secure the access key sharing by following these steps,
- Import the IAM users into PAM360.
- Create a File Store and import the new access key as a file.
- Share the resource with the IAM users.
1.6 Remediating the Inactive Users Risk
To remediate the risk posed by inactive users identified in your AWS account, begin by disabling console access for these users from the AWS console. Assess whether the user’s inactivity requires complete access removal; if yes, proceed by deleting their console access to prevent AWS Management Console access.
To remove console access, delete the user’s login profile using the following command:
aws iam delete-login-profile --user-name USERNAME
For detailed instructions, refer to this document.
1.7 Remediating the Inactive Roles Risk
After identifying the inactive roles in your AWS account using PAM360's Cloud Entitlements, remediate the risk by deleting the IAM role from your AWS server.
To remediate the risk from the AWS console, perform the following steps:
- Log in to your AWS console with administrator credentials.
- Navigate to the IAM dashboard and select Roles from the left pane.
- On the page that appears, select the IAM role that is to be deleted.
- Under the Permissions tab, detach/remove all the policies attached to the role.
- Above the Summary section, click the Delete button and confirm your action to delete the IAM role.
To remediate the risk from the AWS CLI, execute the following commands:
- Execute the following command to list all IAM roles associated with your AWS account. This will help you identify the specific inactive IAM role that is to be deleted.
aws iam list-roles
- Once you have identified the IAM role, execute the following command to list all policies currently attached to it.
aws iam list-attached-role-policies --role-name ROLE_NAME
- Detach each attached policy from the role using the following command. You will need the ARN of each policy to successfully detach it.Replace ROLE_NAME with the role name and POLICY_ARN with the ARN of each policy to be detached. Repeat for all policies associated with the role.
aws iam detach-role-policy --role-name ROLE_NAME --policy-arn POLICY_ARN
- After all policies have been detached, delete the IAM role by executing the following command:Ensure that ROLE_NAME is the correct IAM role name. This action permanently deletes the role from your AWS account.
aws iam delete-role --role-name ROLE_NAME
Following any of the remediation methods for inactive roles, ensures the security and integrity of AWS resources.
Caution
- If an IAM role is actively used by an AWS service (such as an EC2 instance or Lambda function), it may need to be disassociated from the service for a successful deletion process.
- Exercise caution when deleting roles in your AWS account in IAM, as this action could impact your AWS resources.
2. Reverting the Cloud Entitlements' Risks
PAM360 provides an easy-to-use interface for reviewing and reverting remediated actions, ensuring permissions are always aligned with your organization’s requirements. Reverting a previously remediated risk can be especially valuable in instances where unexpected issues arise due to changes in permissions.
For example, if remediation actions unintentionally remove necessary permissions, they can disrupt ongoing AWS processes or cause applications to stop functioning. Additionally, permissions may need to be reverted due to human error, such as misidentifying critical privileges during the remediation process. The ability to revert mitigated risks quickly in PAM360 helps maintain uninterrupted operations while adjusting permissions as needed.
To revert a remediated risk in PAM360 Cloud Entitlements, follow these steps:
- Navigate to the Cloud Entitlements tab and select your AWS account.
- Go to the Users, User Groups, or Roles tab and choose the identity for which the remediated risk to be reverted.
- From the History tab, select the remediated risk that is to be reverted.
Additional Detail
From the History section, you can view the details of a remediated risk, such as remediation time, reason for remediation, removed policies, attached policies, dissociated user groups, and more.
- Click the Revert button next to the risk.

- Review the policies or permissions that will be restored to the identity and click the Revert button.
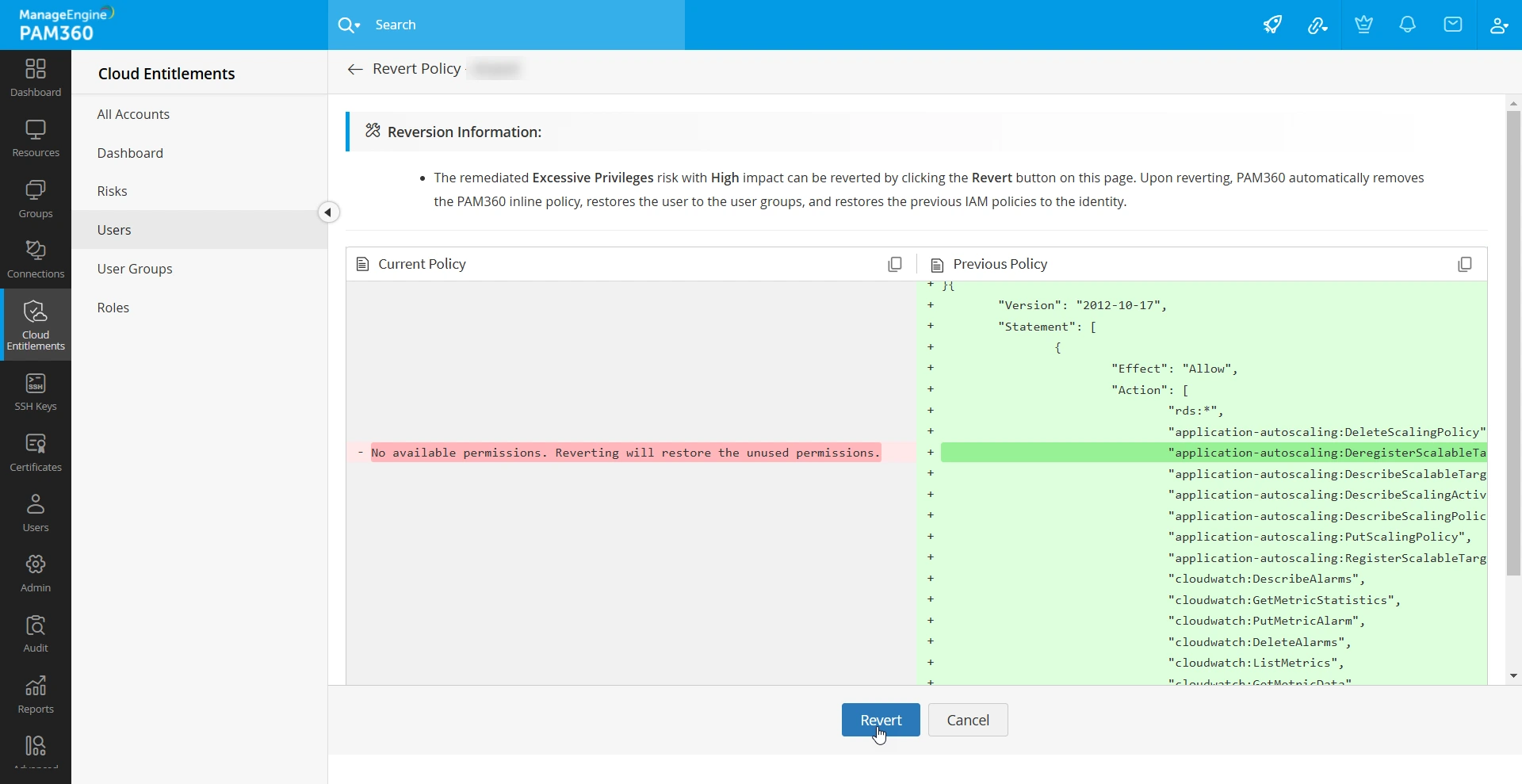
- In the window that appears, confirm your action to revert the risk.
Caution
Please exercise caution while reverting a risk, as the toxic permissions or policies remediated/removed could be restored to the identity and may trigger the PAM360-defined risks again.
3. Audits and Reports of Cloud Entitlements
PAM360 records all actions performed under Cloud Entitlements management as audits, providing comprehensive tracking. Customizable auditing options and notifications are available for specific operations. Access audits via Audit >> Cloud Entitlements and reports via Reports >> Query Reports >> Cloud Entitlements.
Below is the list of reports that can be generated in PAM360 while managing the cloud entitlements.
- Critical-Risk Identities - The list of identities with critical risk.
- Identities with Non-MFA User Risks - The list of identities with Non-MFA users.
- Identities with Non-Rotated Passwords - The list of identities with non-rotated passwords in the last 90 days.
- Identities with Shadow Admin Risks - The list of identities with Shadow Admin risks.
- High-Risk Identities - The list of identities with high risks.
- Inactive Identities - The list of inactive identities (IAM users and roles) in the AWS account for the past 90 days.
- Low-Risk Identities - The list of identities with low risks.
- Medium-Risk Identities - The list of identities with medium risks.
- Non-Retrieved Accounts - The list of accounts that failed during CloudTrail event retrieval.
- Roles with Active Risks - The list of roles with active risks.
- Event Retrieval Paused Accounts - The list of CloudTrail event retrieval paused accounts with the last data retrieval details.
- User Groups with Active Risks - The list of user groups with active risks.
- Users with Active Risks - The list of users with active risks.