Adding Users Manually into PAM360
For procedures prior to build 6700, refer to this help document.
In PAM360, administrators have the capability to create user accounts manually and assign specific roles to them, tailoring access levels and preferences according to organizational needs. This guide outlines the process of adding users manually by allowing administrators to customize user roles, access scopes, and individual settings.
Creating a User Account Manually in PAM360
Below are the steps to create a user account in PAM360 with comprehensive access, including Web, REST API, and SDK functionalities. For more granular access control, administrators can enable or disable specific access as needed for the user. For example, a user can be provided with Web/REST API/SDK access, a combination of Web and REST API, Web and SDK, or REST and SDK access, or with all access.
Navigate to Users >> Add User and click Add User.
Caution
Either access to the Web or REST and Application is required to create a PAM360 user account.
a. User Details
In this section of the add user page, provide basic user information and define the user's role and scope within PAM360.
- First Name | Last Name: Enter here the user's first name and last name.
- Username: Enter here a unique name that the user uses to log into the PAM360 application.
- Email: Enter the user's email address where the user will be notified for updates. Login credentials for PAM360 will be emailed to this address once the user account is created.
- Role: Select an appropriate role for the user from the drop-down; this will determine the type of role and privilege this user will have in PAM360. Refer to this section to learn more about the user roles available in PAM360.
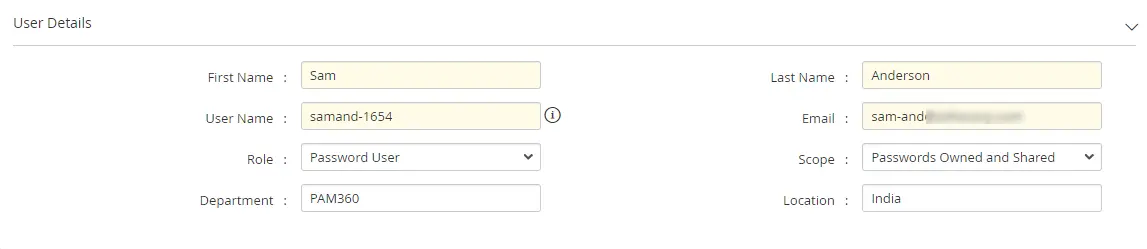
- Scope: By default, users created in PAM360 are assigned the scope of Passwords Owned and Shared. This means they can access passwords owned by them or shared with them by other PAM360 users. However, selecting the All Passwords option grants the user Super Administrator privileges. With this privilege, the user gains unrestricted access to all passwords within the PAM360 application. Click here for more information on super administrators in PAM360.
Caution
- Users with the End-User Type Role cannot be provided with the All Passwords scope.
- Users provided with the All Passwords Scope cannot be provided with the REST and Application Access in PAM360.
- Department | Location: Enter the department and the location where the user belongs to. These fields are not mandatory. However, populating valid data in these fields with the correct values will be helpful while searching or grouping the users.
b. Web Access
Enabling the Web Access grants the user account access to the PAM360 web application, along with access via the PAM360 mobile application and browser extension as provided.
- Password Setup: Choose one method for creating the user account password:
- Generate a Password - This option generates a password randomly based on the selected Password Policy.
- Username as Password - The password will match the username provided.
- Enter a Password - Manually enter a password in the text field.
- Password Policy: Select a password policy from the drop-down menu for the account. The password created/modified for this user account should adhere to the policy selected here.
- Mobile Access: Enable this option to allow the user to access the PAM360 interface via the mobile application.
- Browser Extension Access: Enable this option to allow the user to access PAM360 resources via the browser extension.
- Remote Connect Access: Enable this option to permit the user to launch remote sessions via the PAM360 Remote Connect desktop client using their PAM360 login credentials.
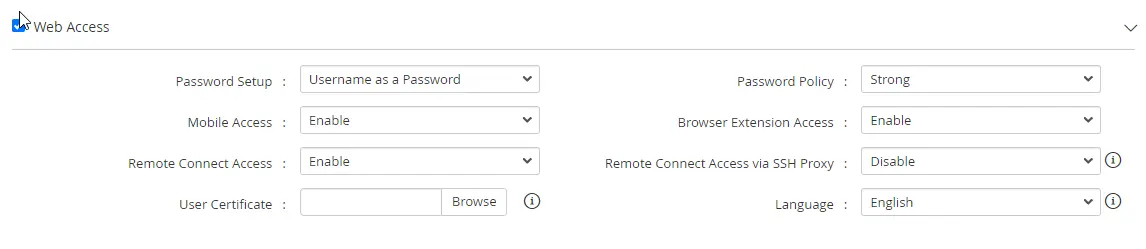
- Remote Connect Access via SSH Proxy: Enable this option to allow user remote sessions in the PAM360 Remote Connect application only via the configured SSH proxy.
- User Certificate: Upload the user certificate here for any smart card/PKI-based authentication. Click here for more information.
- Language: Select the desired web GUI language for the user upon login.
- Two-Factor Authentication: Enable or disable Two-Factor Authentication (2FA) for the user, if 2FA has been set up on the Admin page.
Caution
For a few specific 2FA providers, ensure that the username provided in the 2FA provider portal matches the username in PAM360. In cases where there's a discrepancy (E.g., if a user imported from Active Directory has the username ADVENTNET\rob in PAM360 but recorded as rob in the 2FA provider's portal), you can perform username mapping from here instead of modifying the name in 2FA provider's portal.
c. REST and Application Access
Enabling REST and Application Access grants the user account access to the PAM360 APIs, providing a user Authentication Token for further API access from desired applications or services.
- REST API Access: Enable this option if the user account requires access to the PAM360 REST API.
- SDK Access: Enable this option if the user account requires access to the PAM360 API via the PAM360 SDK.
- Authentication Token: Generate an Authentication Token from here if providing any of the above access. This token serves as a user validation key for API calls received from other applications or services.
Caution
After creating a user account, the user must regenerate their authentication token before accessing PAM360 APIs. This can be done using the authentication token regeneration API or from the My Profile dropdown in the PAM360 user interface. Additionally, whenever the authentication token is regenerated by an administrator, the user is required to regenerate it again before making any API requests in PAM360.
- Access Validity: Select a date until which the Authentication Token will remain valid. Exceeding the provided date will invalidate the Authentication Token, requiring the generation of a new token to extend validity for further use of PAM360 REST APIs.
Caution
Starting from build 7200, access validity for authentication tokens must be specified in terms of days. For instance, if the administrator sets the validity period to 90 days, users are required to regenerate their authentication tokens periodically every 90 days to maintain access. Failure to do so will result in token expiration, after which only the administrator can regenerate the tokens on behalf of the user.
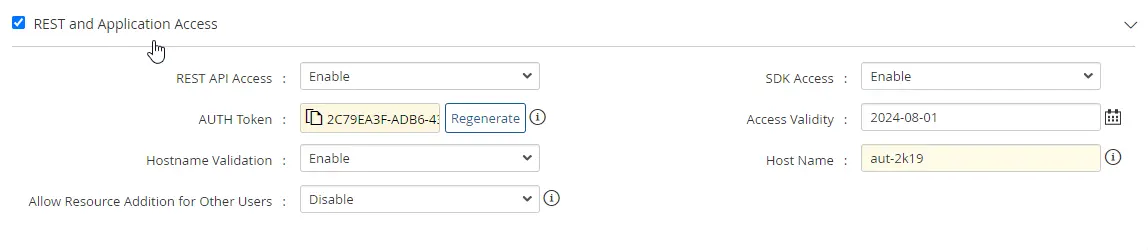
- Hostname Validation: Enable this validation to verify user machines from which API calls are invoked. Enabling this feature restricts API invocation from the machines that are not predefined in the Host Name field.
- Hostname: Enter the Host Name of the machine from which the user is allowed to perform REST and Application operations.
- Allow Resource Addition for Other Users: Enabling this option permits users to create resources via the API and assign them to other users.
Click Save to add the user account to the PAM360 repository. By following this, administrators can manually add users to PAM360, customizing their roles, access levels, and preferences to suit organizational requirements.
Additional Detail
PAM360 users with web access will be forced to reset their local login password when logging in for the first time.