Integrating Kubernetes with PAM360
PAM360, a unified Privileged Access Management product from ManageEngine, integrates with Kubernetes, an open-source container orchestration tool that facilitates automation of software deployment, helps to scale and manage applications effectively.
This integration helps you to fetch secrets stored in the Kubernetes clusters and manage them from the PAM360 interface — you can fetch, manage, and periodically rotate secrets obtained from multiple Kubernetes clusters. Through the integration, you can achieve collaborative management of the Kubernetes secrets used in your enterprise. Once the fetched secrets are added to the PAM360 repository, you can perform a variety of operations to manage them, such as updating the secrets through cluster sync, rotating the secret keys, and enforcing access control on the Kubernetes resources to provide controlled access to the sensitive secrets. PAM360 records extensive audit trails for all operations performed on the Secrets that are stored in the repository.
At the end of this document, you will have learned the following:
- Glossary of Terminologies
- How does the Integration Work?
- Configuring Kubernetes Integration in PAM360
- Fetching and Managing Secrets
- Mapping Secrets to Resources
- Limitations
1. Glossary of Terminologies
| Term | Description |
|---|---|
Container | A portable, executable image that contains software and all of its dependencies. |
Secret | An object that contains sensitive data such as a password, a token, or a key. |
Cluster | A set of worker machines called nodes that run containerized applications. Every cluster has at least one worker node. |
Kubectl | Command line tool used to communicate with a Kubernetes cluster's control plane using the Kubernetes API. |
Namespace | A Namespace is an abstract concept that is used to isolate a group of resources residing within a single Kubernetes cluster. |
2. How does the Integration Work?
The Kubernetes-PAM360 integration utilizes API responses to fetch secrets from the Kubernetes server and bring them into the PAM360 repository as resources, where they can be managed and shared. Secrets from multiple Namespace clusters can be fetched and managed from PAM360.
PAM360 functions like a repository, where secrets from various Kubernetes clusters, invoked for different tasks, can be discovered and stored. The Kubernetes secrets fetched from their respective Namespaces are added as accounts within the resources and stored under the resource type 'Kubernetes'. The accounts are available as downloadable .json files. The below represent a sample Kubernetes Secret.
apiVersion: v1 kind: Secret metadata: name: pam-win8-32-0ex097 namespace: pam360-com type: Opaque data: admin: dXNlcm5hbWU= sysadmin: dXNlcm5hbWU= user-5841: dXNlcm5hbWU= automation: dXNlcm5hbWU= service-acc: dXNlcm5hbWU= local-admin: dXNlcm5hbWU=
Caution
The secret file (.json) may contain single or multiple keys depending on your Kubernetes configuration.
3. Configuring Kubernetes Integration in PAM360
Caution
PAM360 supports only HTTPS connections. Therefore, a valid SSL certificate is required to securely connect with the Kubernetes server. To import the SSL certificate of the host running Kubernetes into the PAM360 certificate store, follow the steps outlined in Question 11 under the Certificates module. While importing the SSL certificate, ensure that the SSL certificate includes the Subject Alternative Name (SAN) field.
3.1 Downloading YAML File from PAM360
- Navigate to Admin >> DevSecOps >> Container Platforms.
- In the integration page, click Configure on the Kubernetes option.
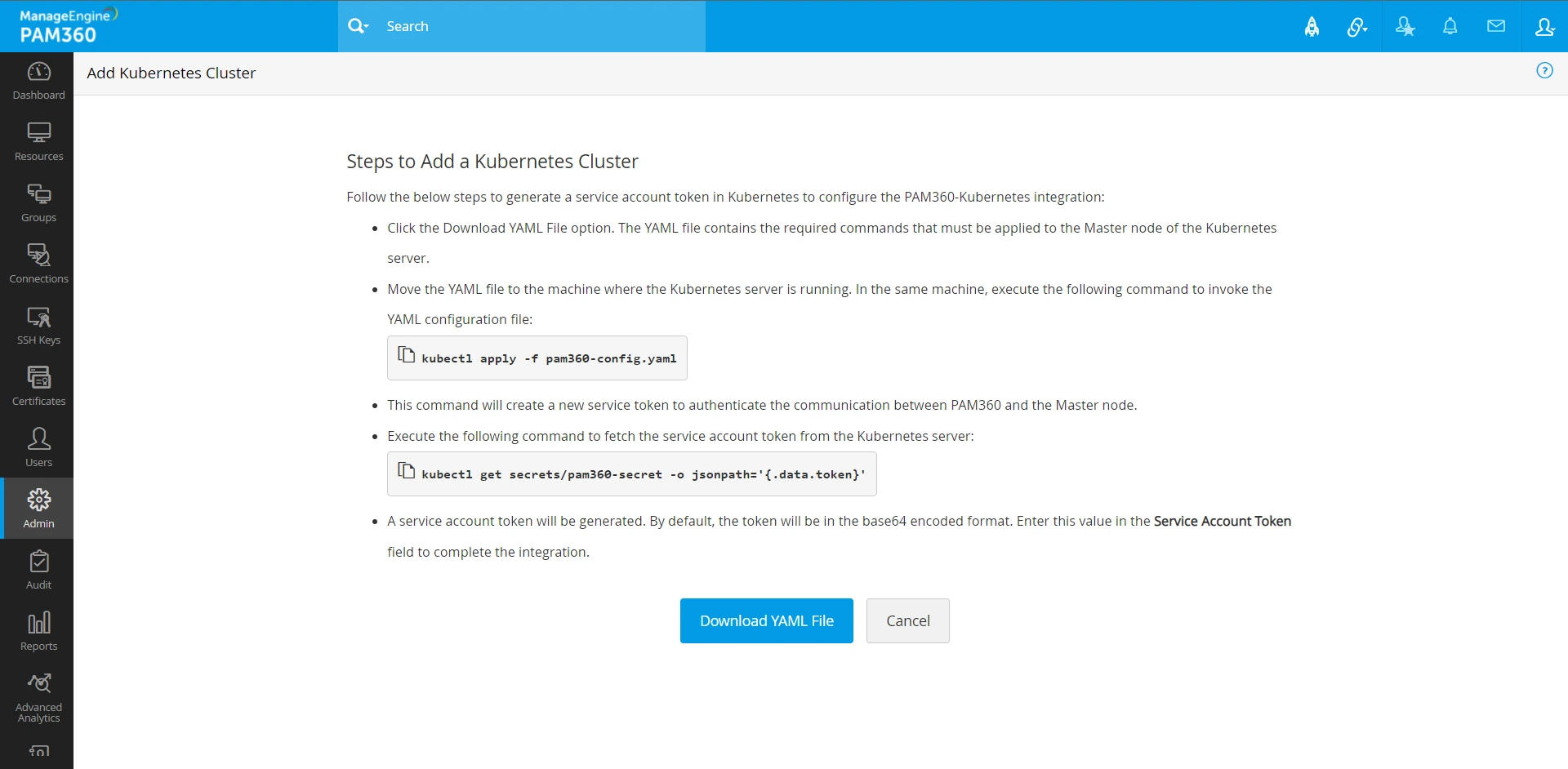
- To begin the configuration process, you must first download the YAML file from the PAM360 interface. The YAML file contains the necessary commands that must be applied to the Master node of the Kubernetes server. In this window, click Download YAML File to proceed.
3.2 Generating the Service Account Token in the Kubernetes Server
- Move the YAML file to the machine where Kubernetes server is running. Execute the following command to invoke the YAML configuration file. This command will create a new service token to authenticate the communication between PAM360 and the Master node.
kubectl apply -f pam360-config.yaml
- Now, execute the following command to fetch the service account token from the Kubernetes server:
kubectl get secrets/pam360-secret -o jsonpath='{.data.token}' - A service account token will be generated. By default, the token will be in the base64 encoded format. Copy this service account token to configure the integration in PAM360.
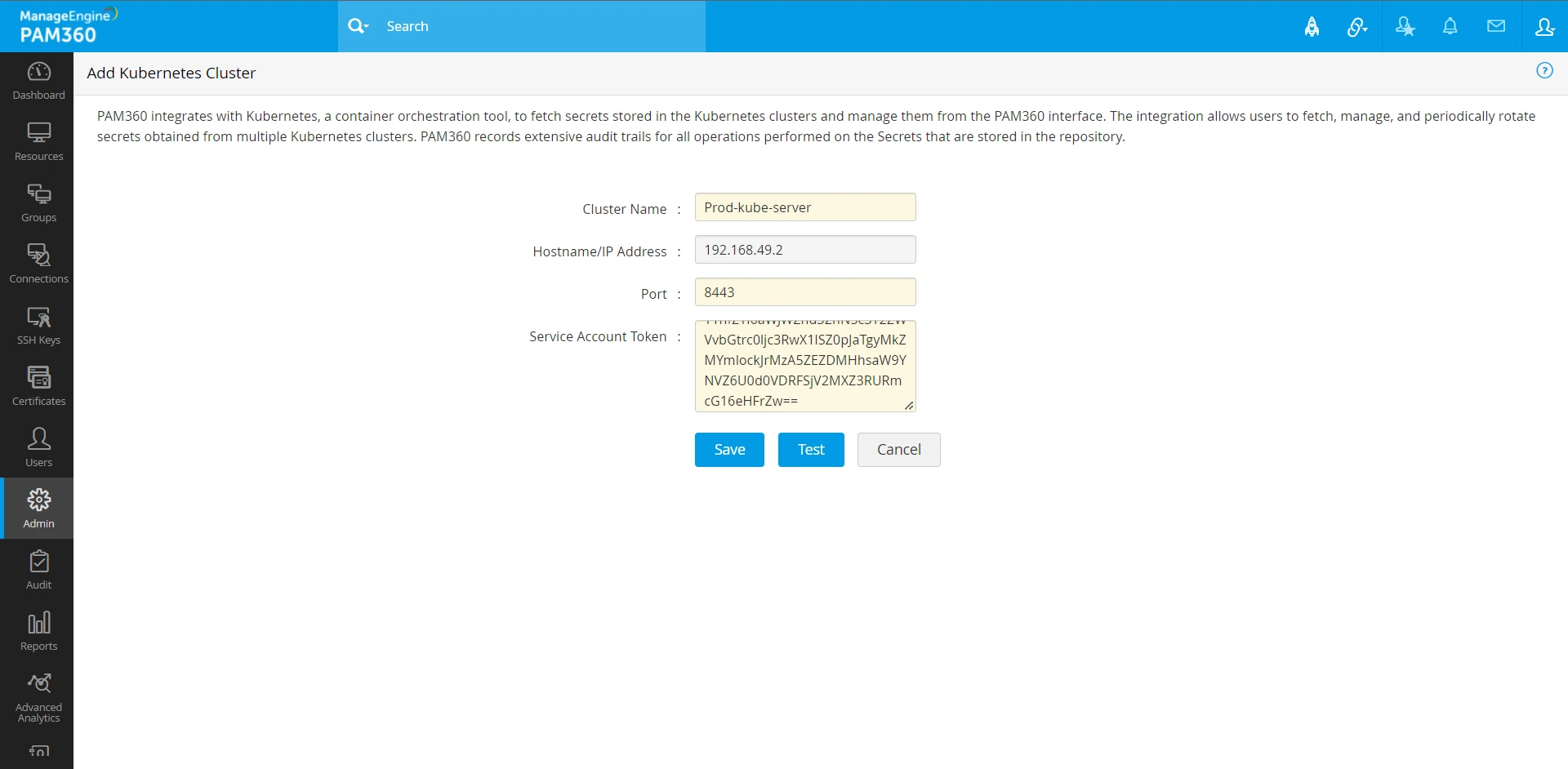
3.3 Configuring the Integration in the PAM360 Interface
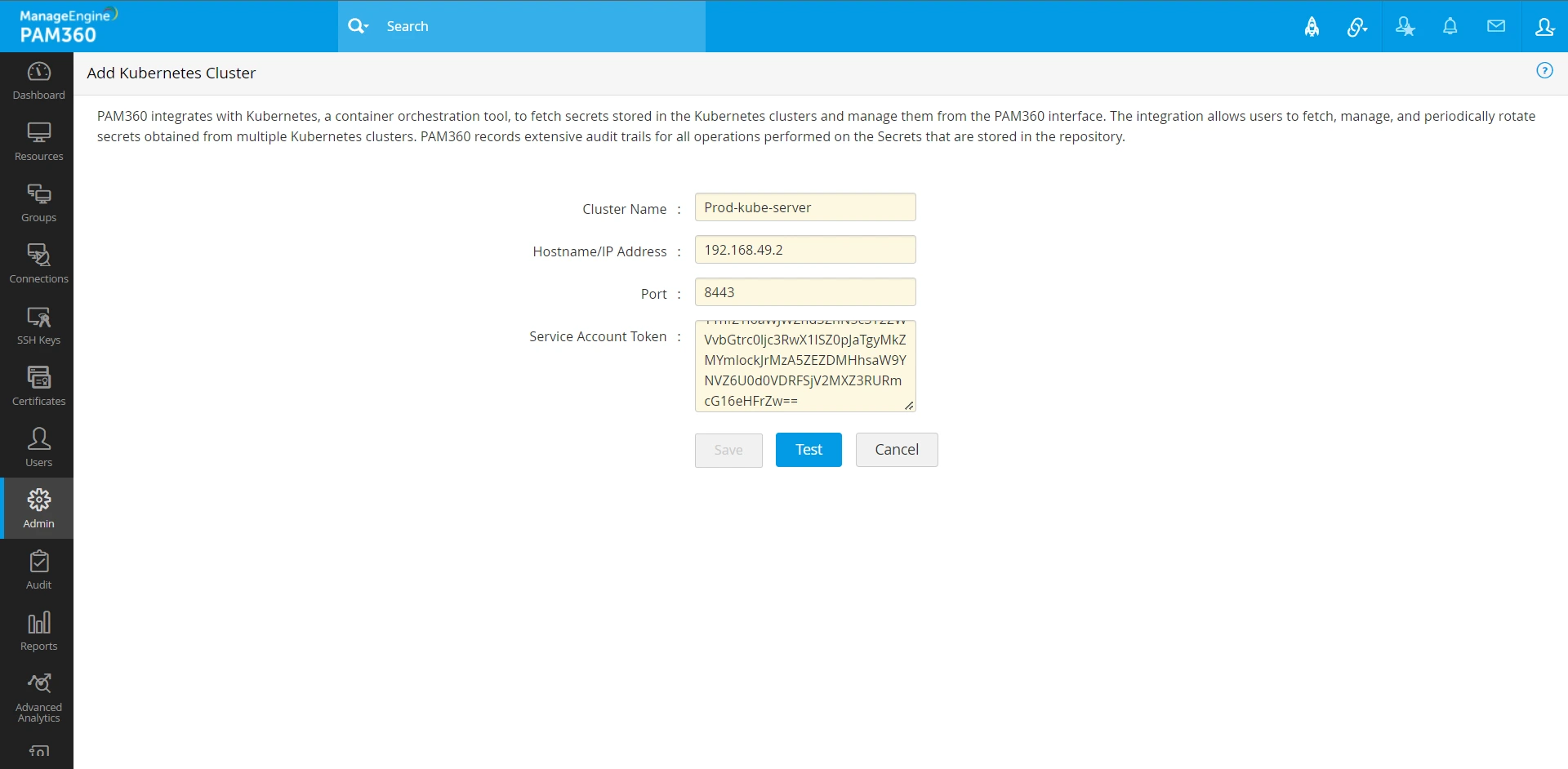
- Now, open the PAM360 interface once again and navigate to Admin >> DevSecOps >> Container Platforms and click Kubernetes.
- In this window, add the following attributes to create a new Kubernetes cluster in PAM360:
- Cluster Name
- Hostname of the machine where the Kubernetes server is running
- Service account token generated from the previous step
- Click Test. This operation will test the cluster configuration and ensure that communication between PAM360 and Kubernetes can be established. PAM360 performs three checks before establishing the connection:
- Verifies if it can communicate with the host machine where Kubernetes server is running.
- Verifies if it can communicate with the Kubernetes cluster.
- Authenticates the service account token.
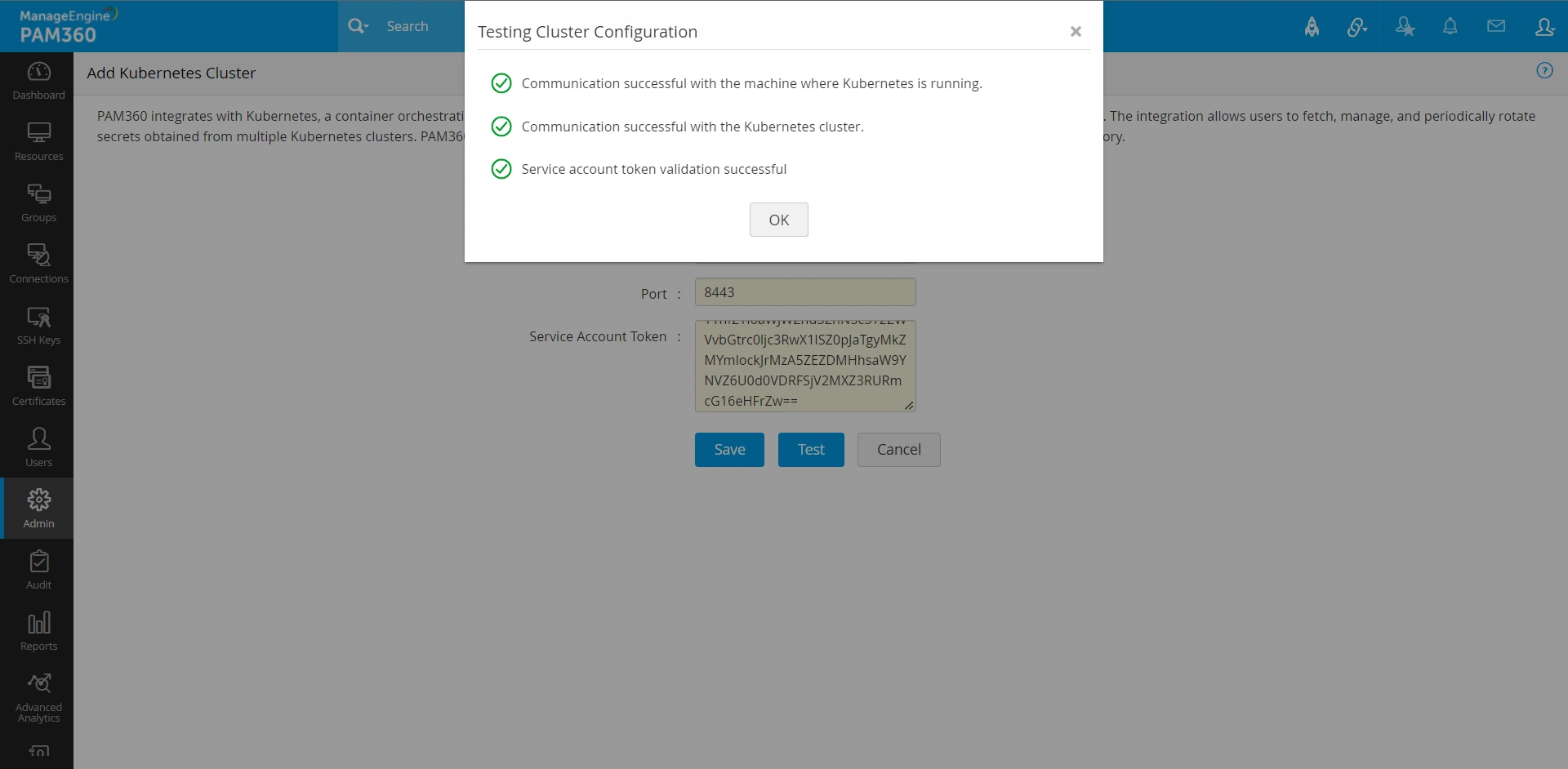
- Click Save to complete the configuration. You can save the configuration details only if the test is successful.
4. Fetching and Managing Secrets
Once you have saved the configuration details, the next step is to fetch secrets from the Kubernetes cluster. Follow the below steps:
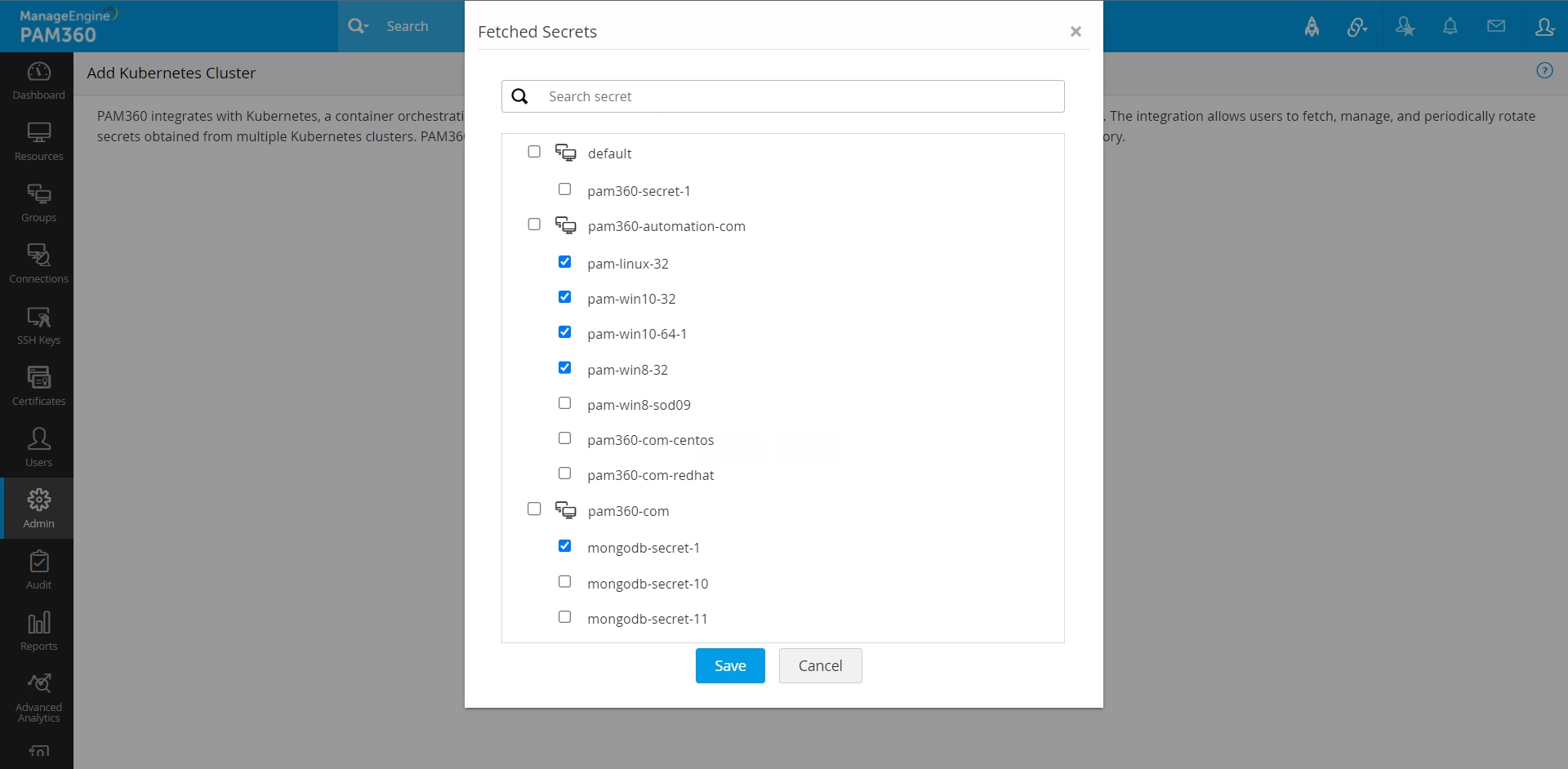
- In the Fetched Secrets window that appears, a list of Namespaces and their corresponding secrets are displayed. Select the required Namespaces or individual secrets and Click Save to start fetching the secrets.
- In the Kubernetes Cluster page, click the cluster name to display all the details related to the Namespace and the cluster in the Namespace and Secrets window.
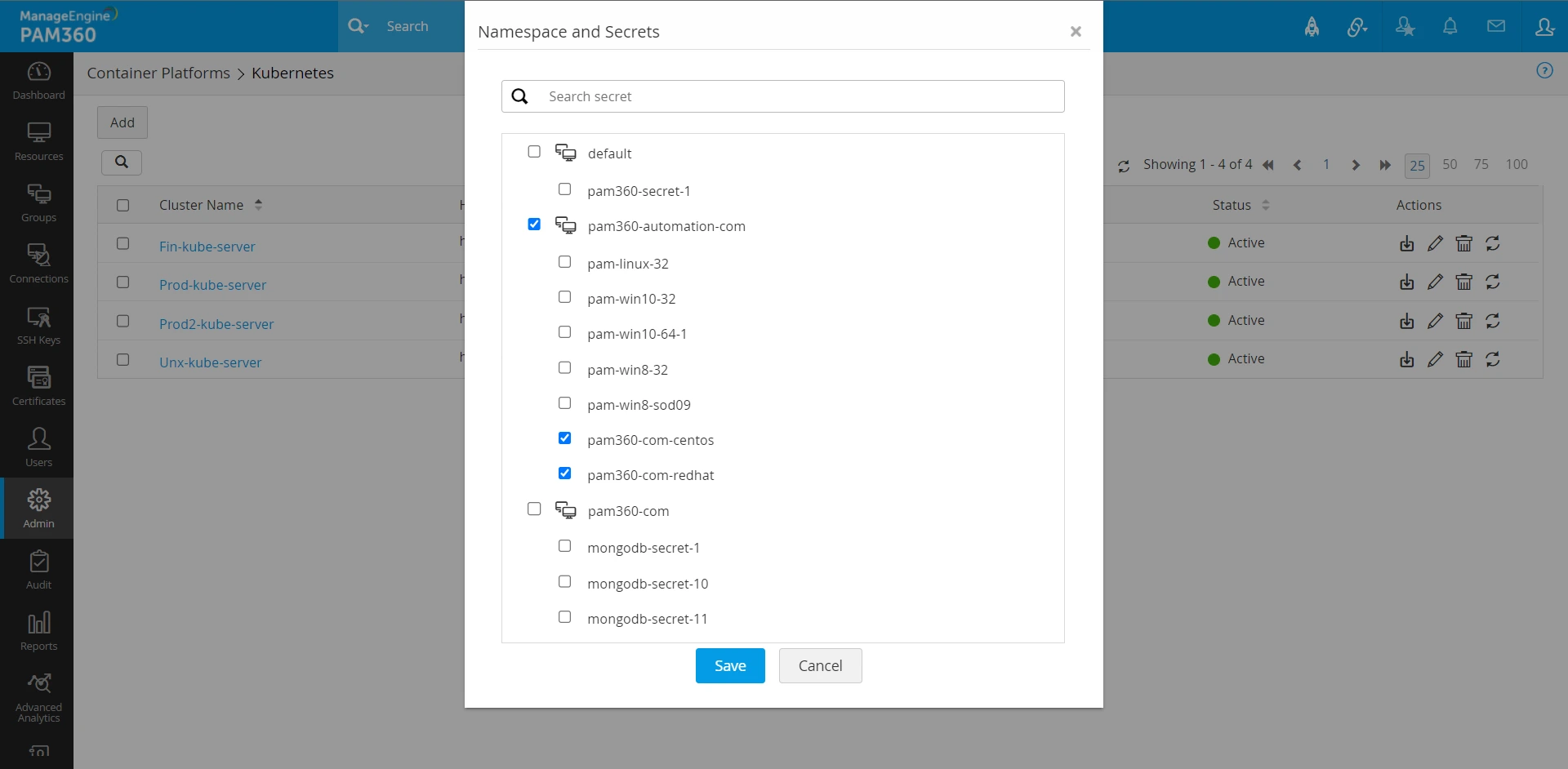
- A new cluster with the Kubernetes server details you provided will be displayed on this page, along with the status of the Kubernetes server and the operations to be performed. There are four main operations you can perform on the cluster:
- Fetch: Click the Fetch icon to fetch Namespaces from the Kubernetes server. The cluster will be named in the format Namespace name - Cluster Name you specified while creating the cluster.
- Edit: Click the Edit icon to change the Kubernetes configuration details.
- Delete: Click Delete to remove the cluster. To add it back, you must follow step 3 and reconfigure it. Please note that the Delete operation will remove only the secret association and not the resources created via this cluster, which will still be available under the Resources tab. We recommend you delete the resources manually to avoid possible conflicts.
- Sync Secrets: Use this option to update the list of secrets fetched from the Kubernetes cluster already added to PAM360. In other words, if a new set of secrets is added to a cluster in the Kubernetes server, the sync option will fetch all the additional secrets added after the initial fetch operation in PAM360 and keep the cluster information in sync with the Kubernetes server.
4.1 Real-Time Use-Case Scenario
John is an IT admin who manages a critical database. The database key required for authentication is a critical entity that needs to be stored away securely. For this purpose, John saves the database key within multiple Kubernetes secrets. Now, he needs a secure repository to store the Kubernetes secrets and manage them from a single interface.
Here comes the PAM360-Kubernetes integration into play. The integration allows John to choose and fetch secrets stored in Kubernetes clusters as needed. During the operation, PAM360 fetches the JSON file that contains the critical secret keys and stores them in a file store within the repository. PAM360 encodes the secret keys contained within the secret files. The product is capable of fetching and storing secrets from multiple Kubernetes clusters. Kubernetes secrets contain machine identities that the system uses to interact with other systems outside the Kubernetes server. Through this integration, PAM360 automates the process of secrets management.
John can also rotate the Kubernetes secrets through a password reset operation from the PAM360 interface. To achieve this, he can map the Kubernetes secrets to existing resources in PAM360 and change the passwords of the resources. This operation will rotate the secret keys stored within the JSON files fetched from Kubernetes. However, the secret keys will not be automatically updated directly in the Kubernetes server.
5. Mapping Secrets to Resources
To begin managing the secrets you have fetched, map them to resources in the PAM360 repository.
- Once the secrets are fetched, PAM360 creates individual resources with the following naming convention: Namespace-Cluster Name. Navigate to the Resources tab to view all Kubernetes resources created by PAM360.
- The secrets are categorized under the resources based on the Namespace and the Kubernetes Cluster from which they were fetched.
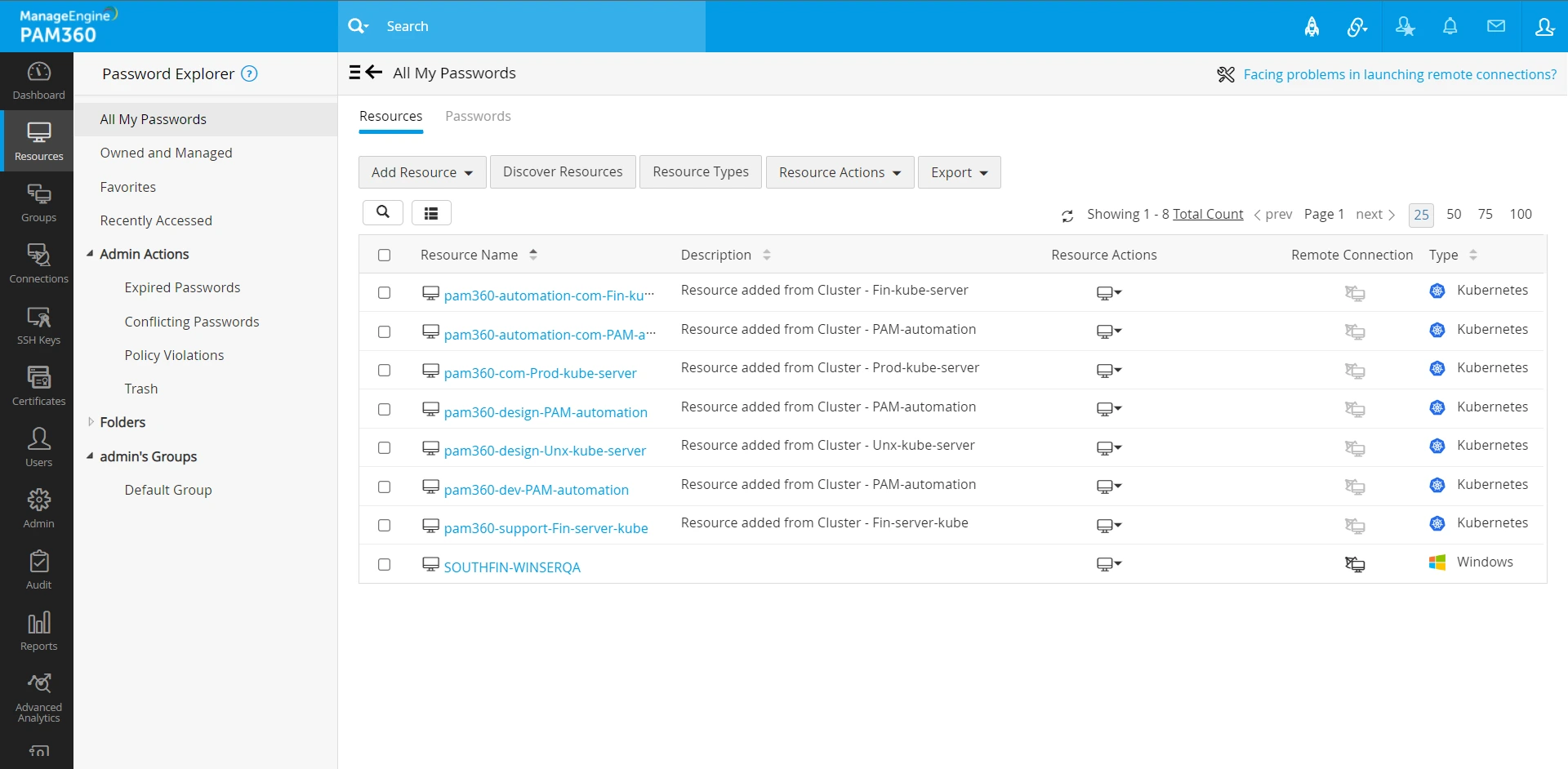
- You can associate Kubernetes secrets with any resource of any resource type owned by you or shared with you.
- Select a resource, go to Account Actions >> Associate Secrets
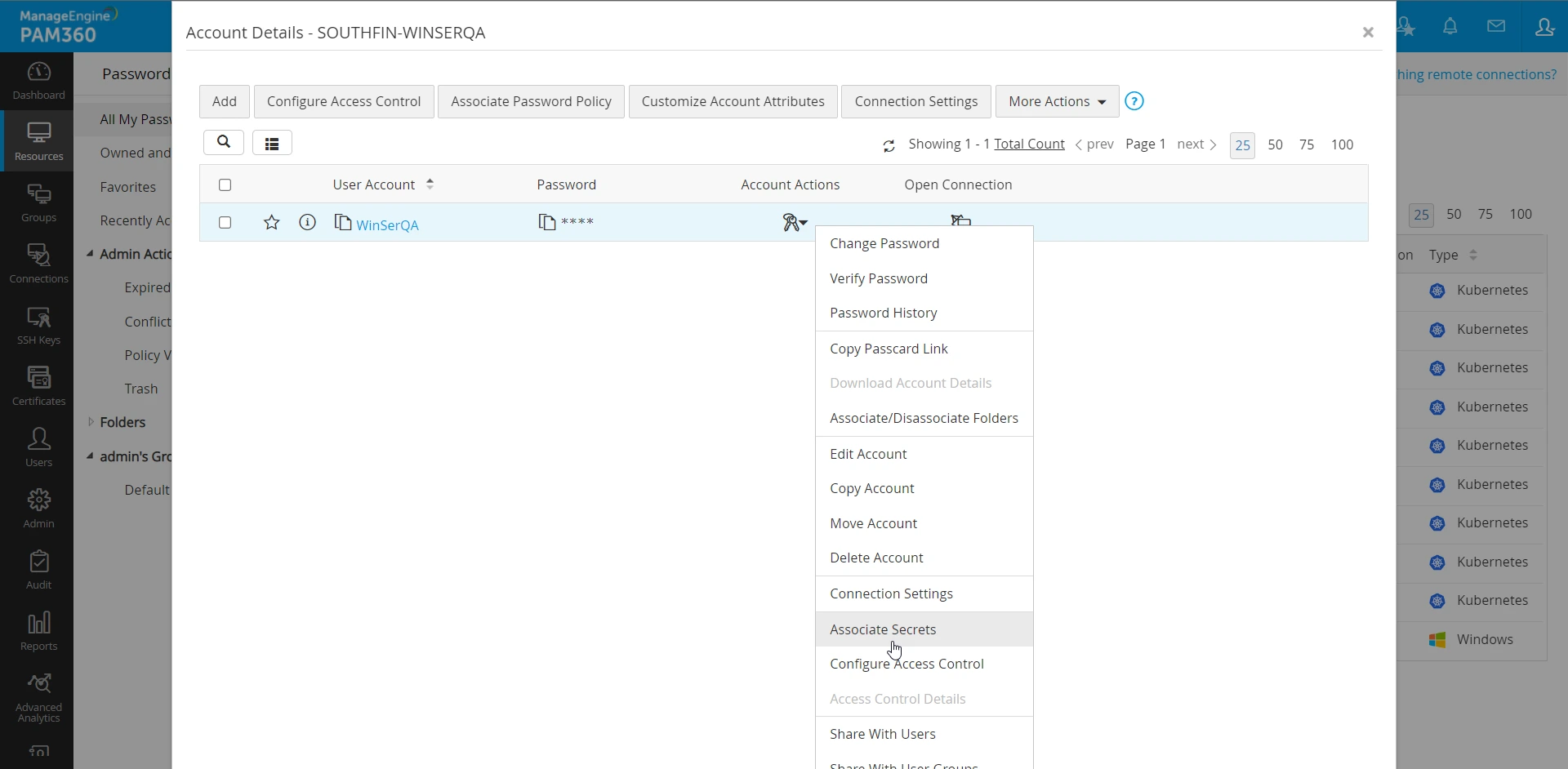
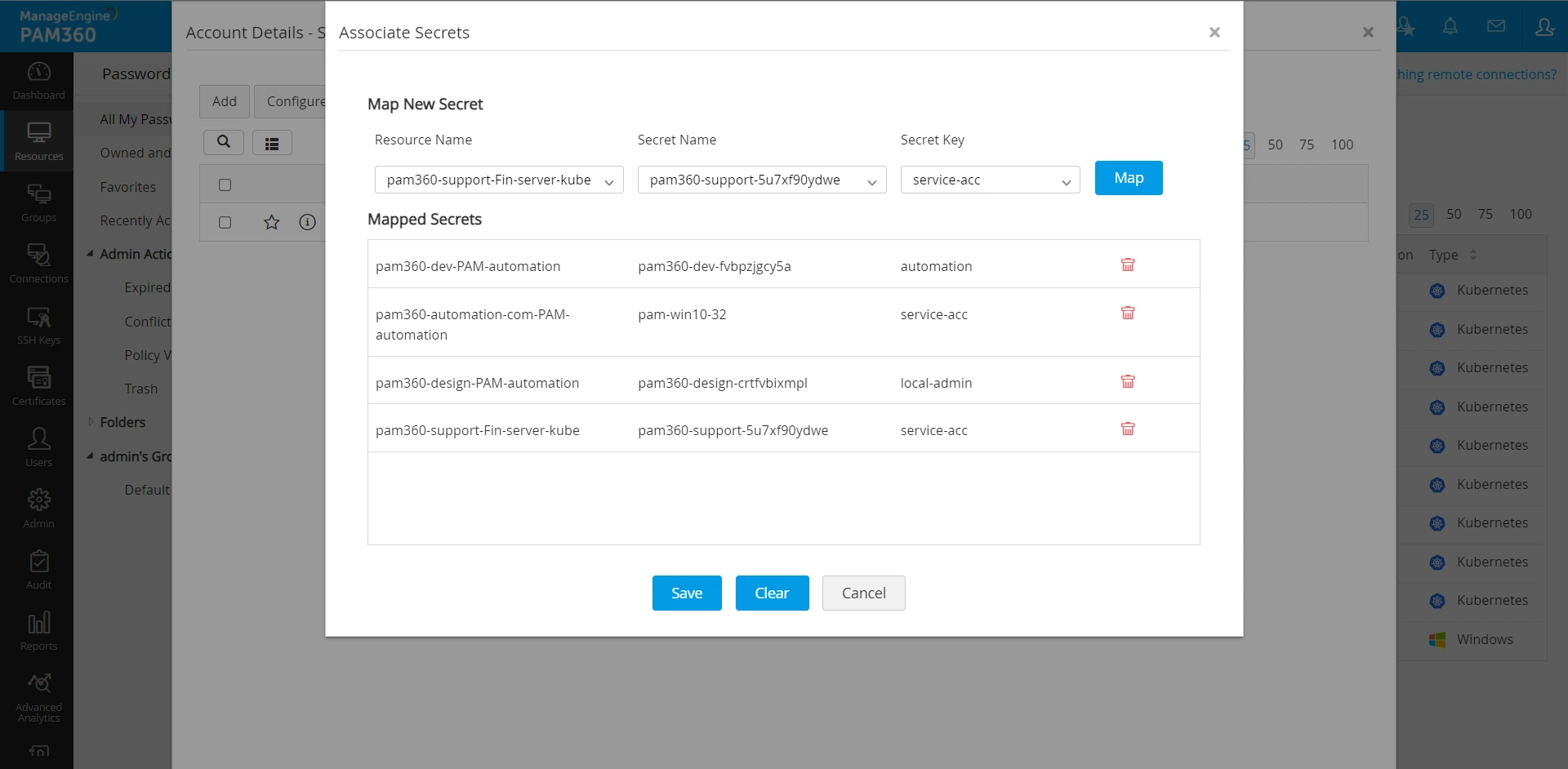
- In the Associate Secrets window, select a resource name from the drop-down, a secret name and a secret key belonging to the secret. Click Map and save. You have successfully associated the selected secrets and secret keys with the account. You may map multiple secrets to a resource.
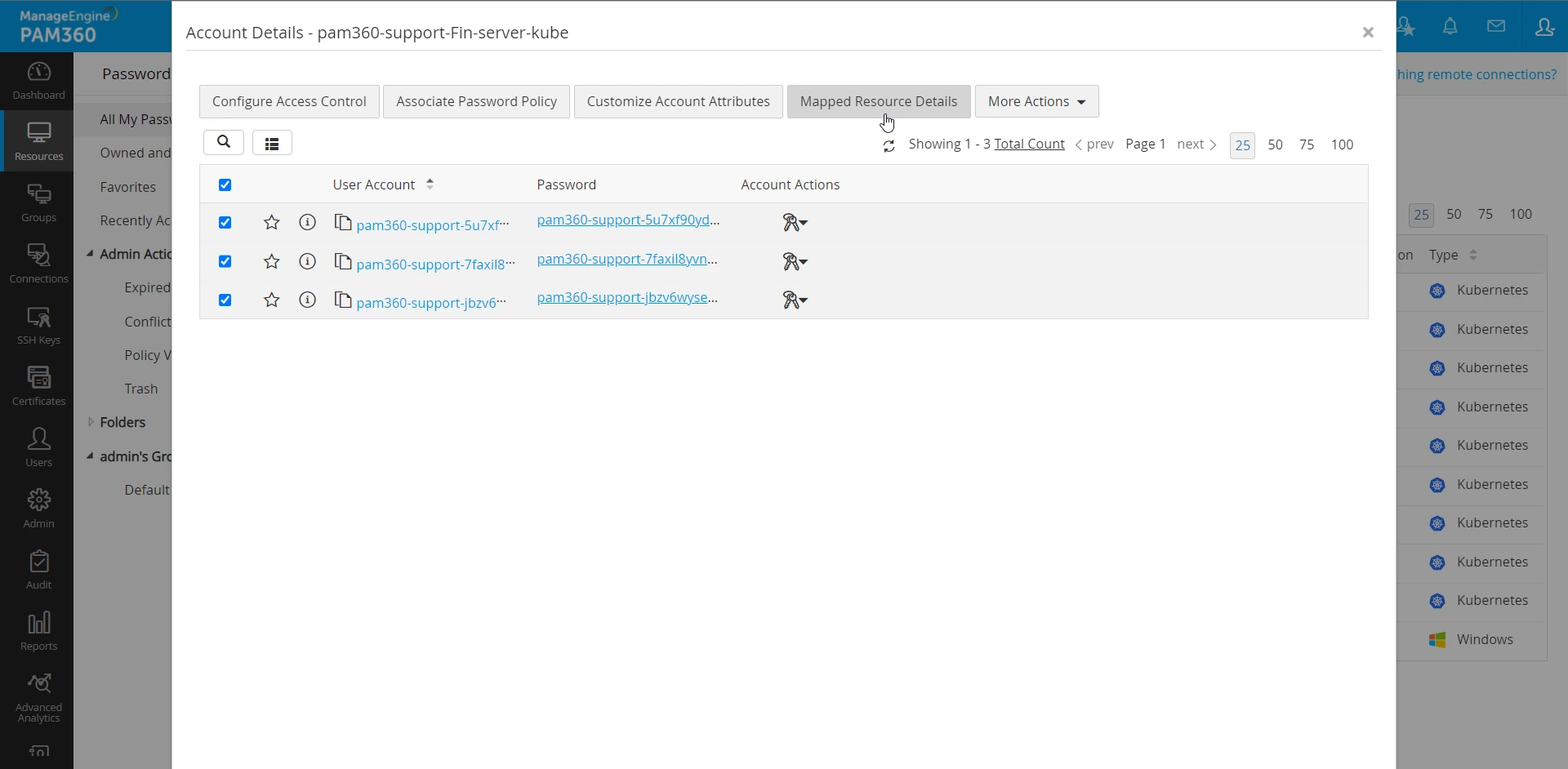
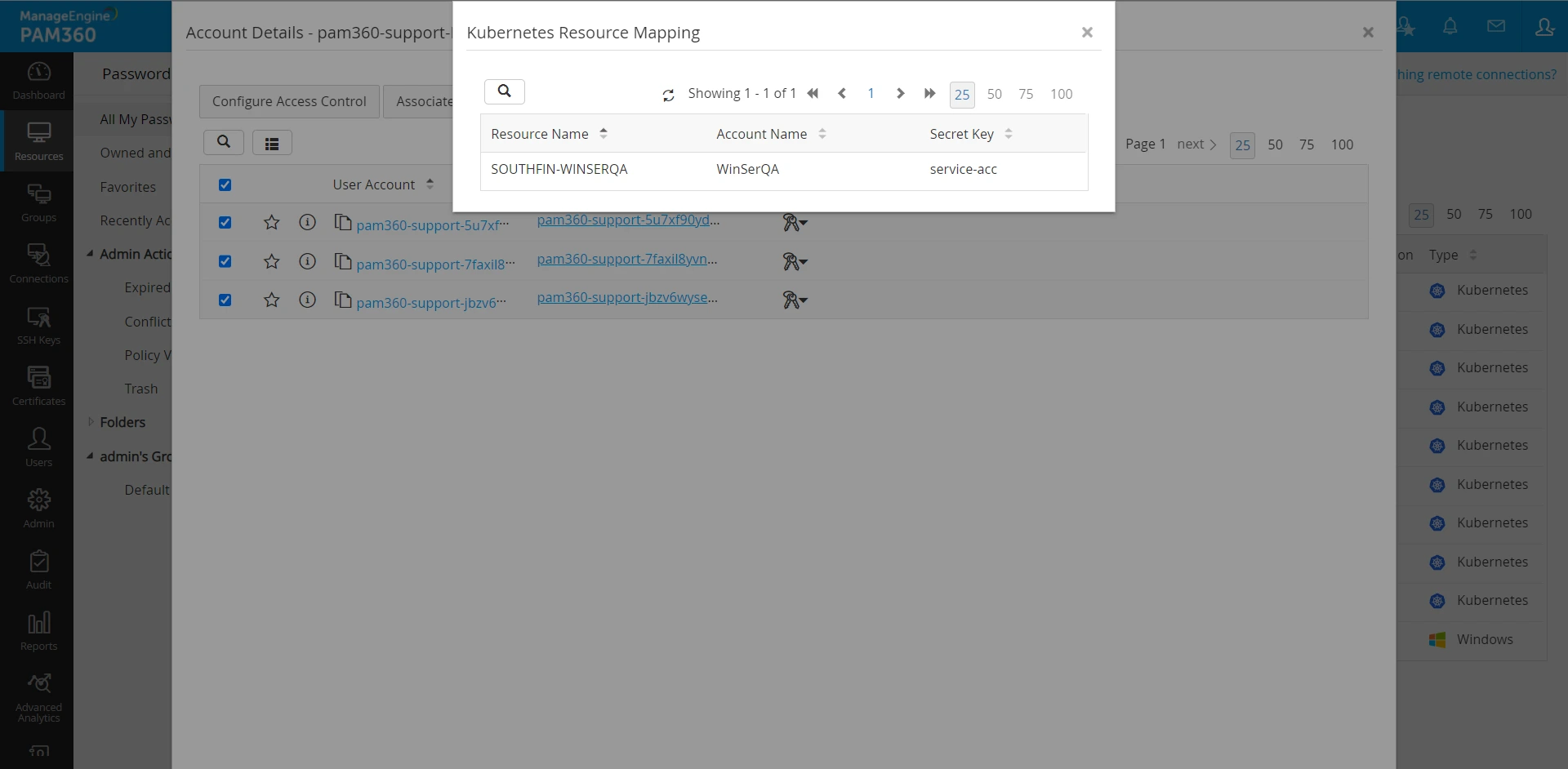
- Once mapping is complete, you are ready to manage the secrets through the resource. To view mapping details, open any Kubernetes resource and click Mapped Resource Details. This window will display all the list of secrets belonging to this Kubernetes cluster and the resource to which they are mapped.
Caution
Please note that any password reset operation triggered through the mapped resource will change all of the secret keys mapped to it and the changes will reflect in the Kubernetes server. However, PAM360 will not reset the passwords of the services running inside the Kubernetes clusters.
6. Limitations
- You must manually map each secret to a resource to manage them from the PAM360 repository. Whenever new secrets are synced from the Kubernetes server through an on-demand fetch, the secrets must be manually mapped to a resource from the Resources tab.
- PAM360's remote password reset support does not extend to the services running inside the Kubernetes server.
- The integration offers only a one-way sync—PAM360 can fetch the additional secrets added to the Kubernetes cluster, but it cannot remove the secrets already deleted from the Kubernetes server.
- PAM360 does not have an automated sync schedule to fetch secrets from the Kubernetes server automatically.