PAM360 Reports
Reports in PAM360 are a crucial component in ensuring the security, compliance, and efficiency of password and privileged access management within an enterprise. These reports provide IT administrators and security teams with comprehensive insights into various activities, including password inventory, policy compliance, user activity, and more, aiding in better decision-making and risk mitigation. The reporting capabilities within PAM360 are designed to provide essential data through tables and graphs, making it easier for administrators to analyze information and maintain a robust security posture.
PAM360 offers pre-configured reports, categorized into different types, along with the flexibility to create custom reports to suit specific needs. These reports cover all aspects of privileged access management, ensuring that organizations can stay compliant, detect vulnerabilities, and maintain transparency.
1. Importance of Reports in PAM360 Application
- Security Auditing and Compliance - As the PAM360 application manages highly sensitive access, regular reporting is vital for ensuring compliance with regulations such as GDPR, PCI DSS, and ISO/IEC 27001. Reports offer a detailed record of privileged access activities, helping auditors and stakeholders demonstrate compliance and detect any potential policy violations.
- Accountability and Transparency - Reports in PAM360 provide a clear log of who accessed what, when, and for how long. This ensures transparency and accountability within the organization by creating a trail of privileged access. Suspicious activities or unauthorized access attempts can be flagged for further investigation, helping to enhance security.
- Monitoring and Oversight - Regular reporting allows IT and security teams to monitor access patterns and behaviors. For instance, anomalies such as employees accessing sensitive systems outside of regular working hours can be detected, helping prevent insider threats and unauthorized breaches.
- Risk Mitigation - Detailed reports help organizations identify high-risk accounts or vulnerabilities. If a privileged account has excessive access, reports can highlight this, allowing administrators to revoke or reduce access and mitigate risks before they become security incidents.
- Incident Response - In the event of a security breach or policy violation, reports serve as crucial evidence for post-incident investigations. They provide a clear trail of user activities, helping security teams identify the root cause, contain the damage, and implement preventive measures for the future.
- Optimization and Efficiency - Reports enable organizations to optimize workflows and access control policies. For example, administrators can determine how often privileged accounts are used, identify unnecessary resource access, and adjust access levels to improve overall efficiency.
- User Behavior Analytics - PAM360 can generate reports with insights into user behavior. This allows security teams to distinguish between normal and abnormal behavior, identify compromised accounts, and detect insider threats based on deviations from regular patterns.
- Regulatory and Management Reporting - High-level reports provide summaries and insights into security operations, helping management understand the effectiveness of PAM policies. Executives and board members can use these reports to make informed decisions to enhance the organization's overall security posture.
2. Report Categories in PAM360
Including robust reporting features within PAM360 helps organizations enforce security policies, maintain operational transparency, and meet compliance requirements. The wide range of available pre-configured, custom, and query reports ensures that all aspects of privileged access management, from password security to user activity monitoring, are covered, making PAM360 an essential tool for maintaining a secure and efficient IT environment. The report categories available in the PAM360 application are: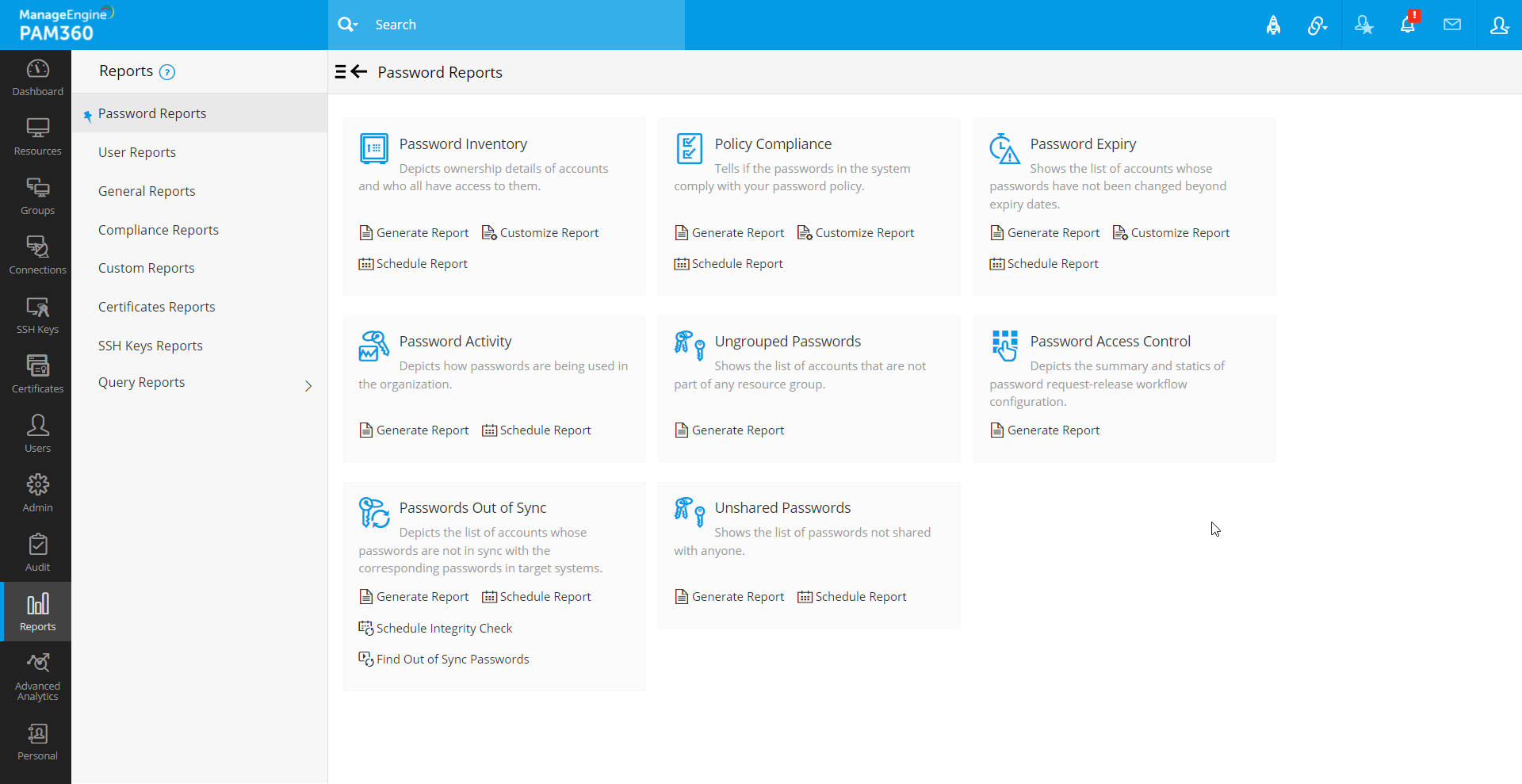
- Password Reports - These reports offer insights into password inventory, password expiry, and policy compliance, helping administrators manage passwords efficiently and securely.
- User Reports - Track user activity and access behavior, providing a detailed view of user-specific actions, which is crucial for monitoring privileged access.
- General Reports - Provide a high-level overview of password activities, allowing continuous monitoring of privileged access and system events.
- Compliance Reports- Ensure adherence to regulatory requirements by tracking compliance with internal and external policies like GDPR, PCI DSS, ISO/IEC 27001, etc.
- Custom Reports - Allow administrators to generate tailored reports using various filters and parameters to meet specific organizational needs.
- Certificates Reports - Monitor the status of digital certificates, helping organizations stay ahead of certificate expiration and renewal processes.
- SSH Keys Reports - Provide insights into SSH key usage, helping administrators manage and audit SSH keys for secure access.
- Query Reports - These flexible reports allow users to run custom SQL queries on the PAM360 database for more granular and specific data reporting.
Click on the respective report categories to learn more about them in detail.
3. Scheduling Report Generation
All PAM360 reports can be generated at a periodic interval or specific period based on the organization's requirements. This can be attained using the Schedule Report option provided by PAM360. The generated scheduled reports can be sent via email with the desired format to the required recipients.
To create a schedule for any PAM360 report, follow the below steps:
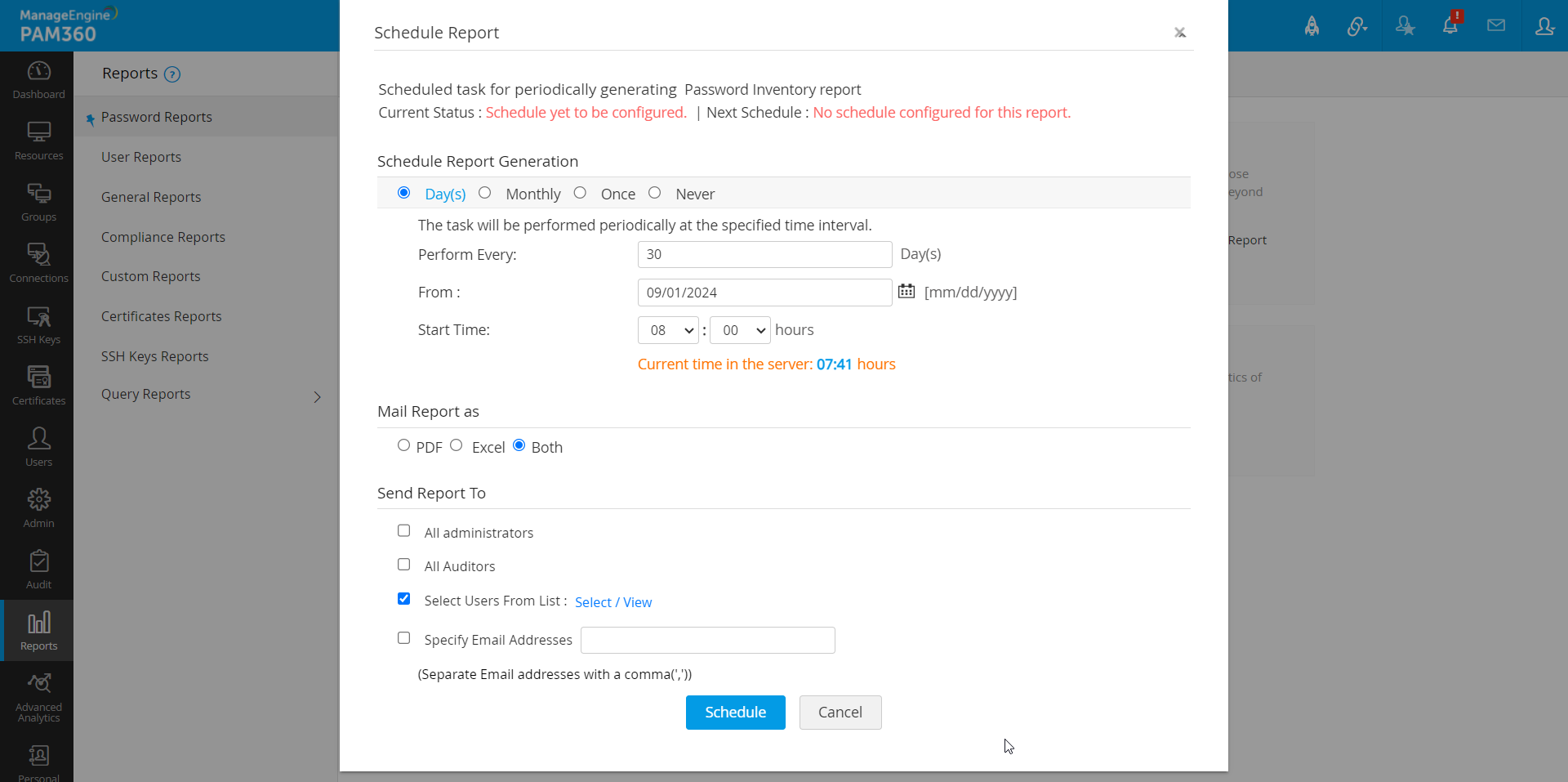
- Navigate to the desired report in the Reports tab and click Schedule Report available under the name of the report.
- In the pop-up form that opens, select the required schedule from the provided terms - Days / Monthly / Once / Never.
- Next, enter the date / time at which the schedule has to commence.
- Choose the format in which the report has to be mailed to the recipients, PDF or XLS or Both.
- Select the recipients to whom the report should be mailed to, from the given options. You can also enter the list of email IDs to which the report has to be emailed.
- Click Schedule to confirm the schedule task.
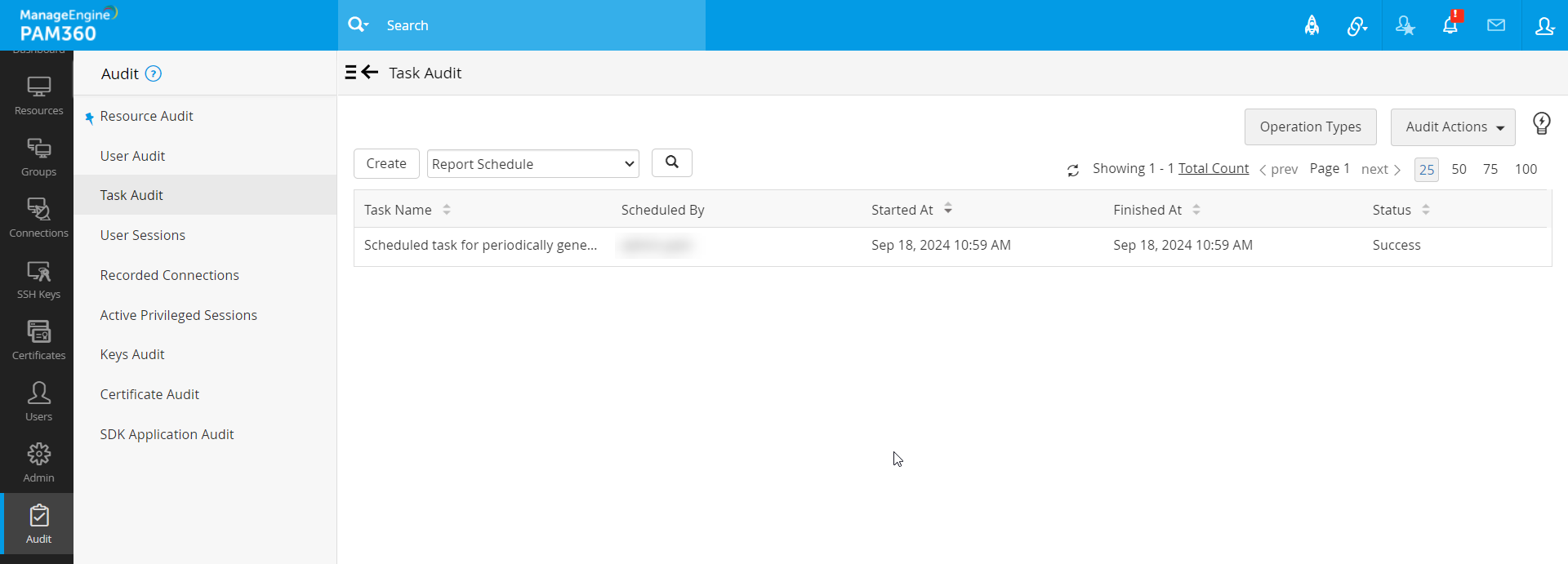
The scheduled tasks will be listed under the User Created Schedules section in Admin >> Manage >> Schedule Tasks. Whenever a schedule gets executed, the result of the scheduled task will be audited and can be viewed from the Task Audit section.
To terminate an existing schedule, simply follow the below steps:
- Click Schedule Report available under the name of report for which the schedule has to be terminated.
- In the dialog box that opens, select the option Never and click Schedule to terminate a schedule.