Practical Implementation Scenario and Use Cases
Zero Trust security is a security model that assumes that all users, user devices, and resources are untrusted by default. This approach requires organizations to verify the identity of all users, devices, and resources before granting users access to resources with the organization's data, thus resulting in safeguarding the organization's data from threats and anomalies.
Implementing Zero Trust can seem daunting, but it is crucial for organizations to adopt a Zero Trust model to protect their sensitive data from external breaches and cyberattacks. From this document, you will explore a practical Zero Trust implementation scenario in an organization and examine case studies that led to the result of successful Zero Trust implementations.
1. Zero Trust Implementation Scenario in an Organization
Imagine an organization with the below hierarchical scenario and strength: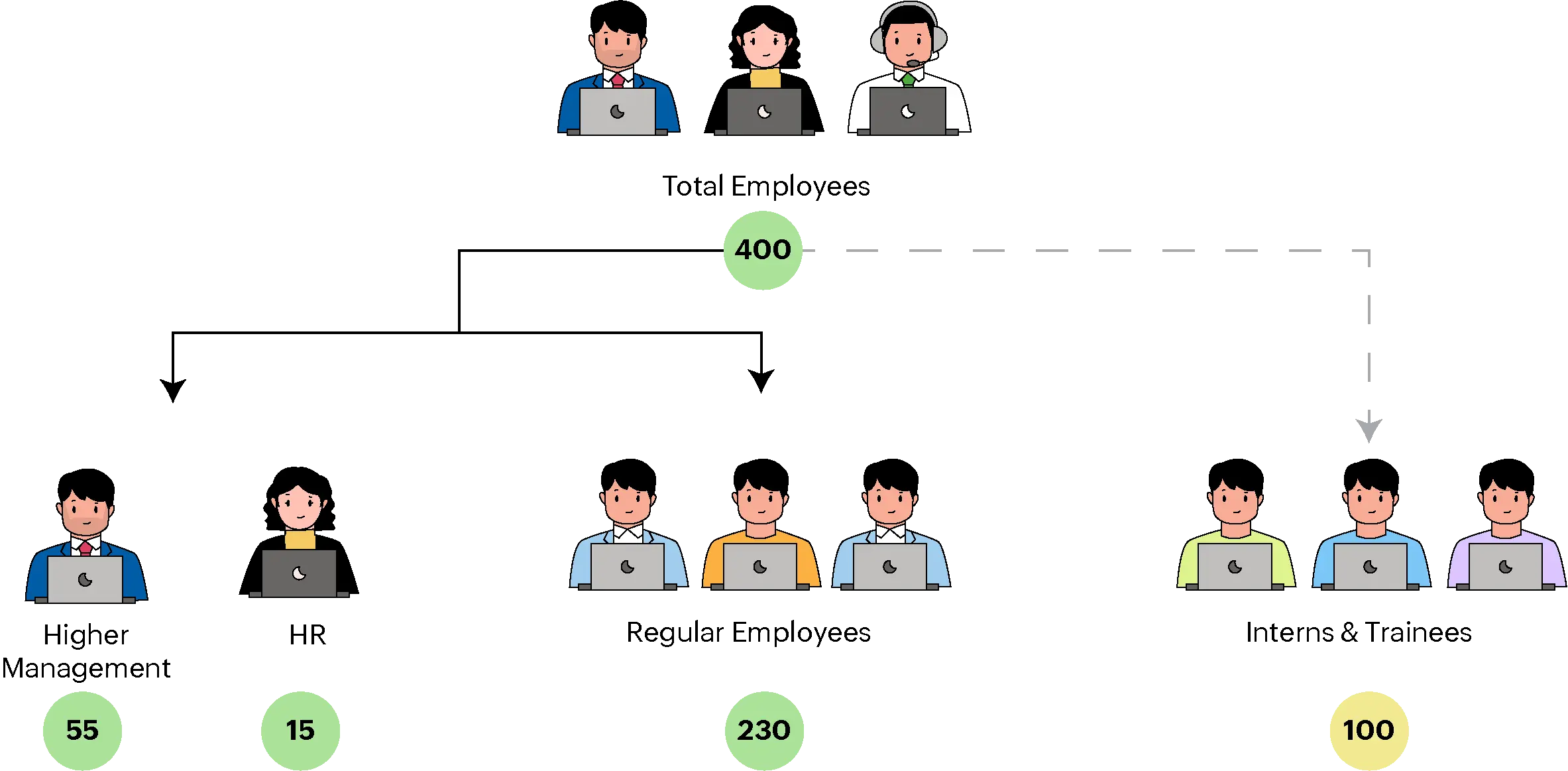
- People from Higher Management and the HR are grouped in the user group - Privileged Users.
- Regular Employees are grouped into the user group - Regular Employees.
- Interns and Trainees are grouped in a user group - Interns and Trainees.
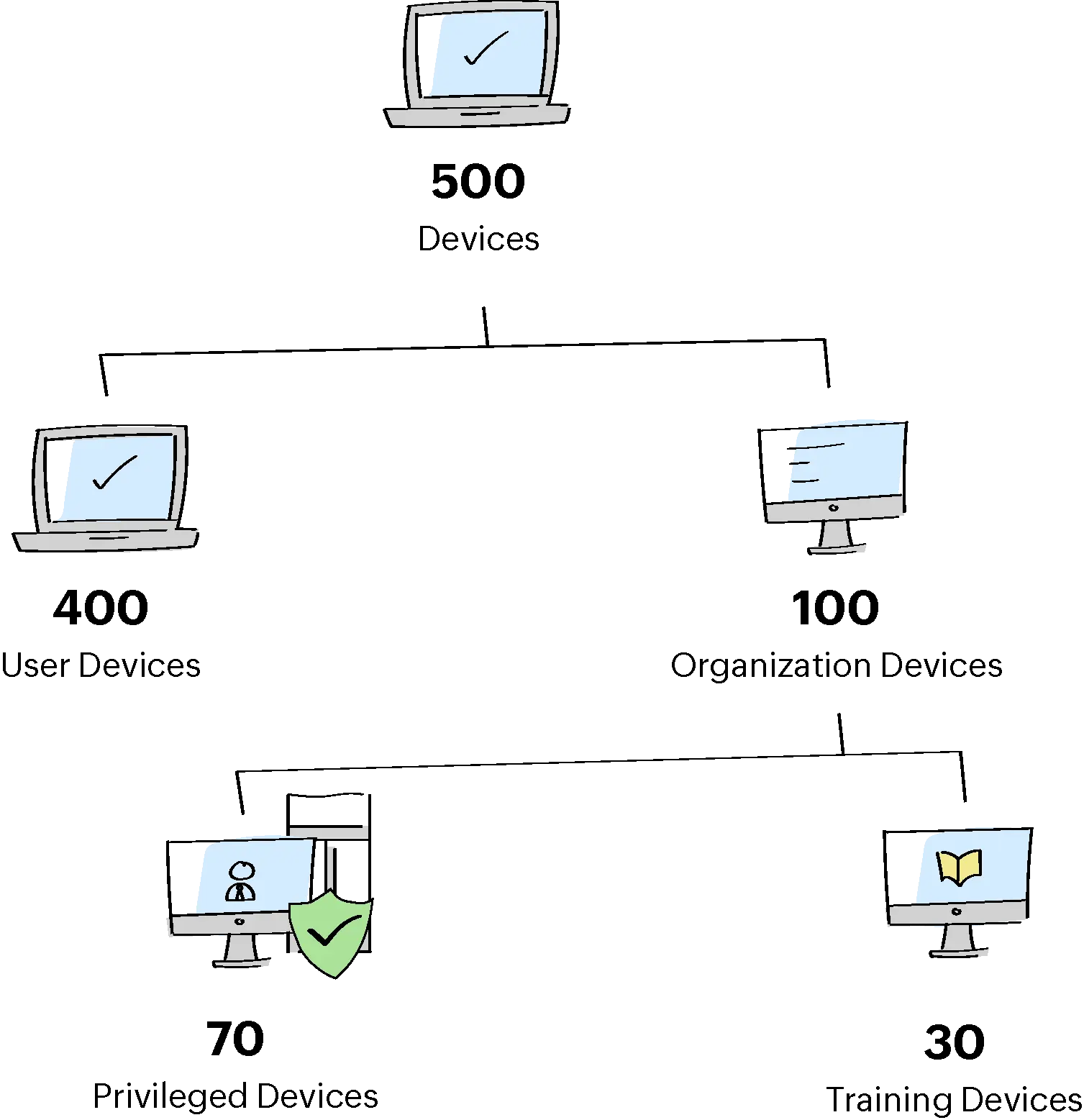
- Organization Devices include Privileged Devices and Training Devices.
- Privileged Devices are grouped in the resource group - Privileged Devices.
- Training Devices are grouped in the resource group - Training Devices.
John - The IT administrator of the above organization is struggling to manage and grant access privileges to many individuals, including regular employees, interns, trainees, and higher management and human resources personnel. Additionally, he faces challenges in managing user and privileged devices, protecting against threats from sophisticated attackers and algorithms, restricting access to non-compliant devices, and monitoring user activity and access to privileged devices.
Without an approach like Zero Trust, these difficulties can lead to security vulnerabilities and unauthorized access to sensitive information. Hence John plans to enforce the policy-based access privilege (Zero Trust approach) via PAM360.
Organization Requirements
- Regular employees should have access to all the privileged devices with prerequisite conditions except the training devices.
- Interns and trainees should have a strict access policy for accessing the training devices for training and validation purposes.
- People from higher management and HR should always have access to all the devices in the organization with certain access conditions.
- All devices that include highly privileged accounts should be checked continuously for security.
- Regular employees, interns, and trainees should be given access to their respective allocated devices based on the user activities and device/resource state.
- Granting access to organization resources should be automated in a high-end workflow with enhanced security criteria.
Step 1 - Installing Zero Trust Agent
To validate the user device and resource credibility using the user device and resource state, some certain parameters from them should be fetched for validation. To fetch those details for validation to policy-based access privilege, John will:
- Install the PAM360 agent of Usage type - User Device in the user devices.
- Install the PAM360 agent of Usage type - Resources in the organization resources Zero Trust Module.
Step 2 - Configuring Trust Score Parameters
John will then navigate to the Admin >> Zero Trust >> Configuration page to define conditional parameters for the user authentication, user device, and resources for calculating trust scores based on the organization's requirements and standards. John defines the following conditional parameters that follow:
Caution
The conditional parameters set here are only for reference. To know more about configuring parameters in detail, refer to this help section.
User Score Parameters
| Authentication | |
|---|---|
| Invalid Sign-In Attempts | 5 attempts in 7 days |
| Non-Office Hour Sign-In | 09:00 to 18:00 |
| Access from Allowed IPs | 172.24.2XX.X to 172.24.2YY.Y |
| Access from Allowed Devices | 192:YY:YYY:YY pam-2k694 |
| User Belongs to Privileged Group | Privileged Users |
| Device | |
|---|---|
| Allowed OS Version | 10.0.22621 |
| Open Ports | 135 445 623 3306 4567 5040 7680 8020 8027 8028 8383 8443 9292 9293 9295 16992 49664 49665 49666 49667 4567 7680 8028 8443 9292 9293 9295 16992 49664 49665 49666 49667 49668 49669 49673 49670 69 123 5050 61856 137 138 1900 56744 69 123 60504 63906 1900 49667 56743 57457 1900 56742 |
| Allowed Browser Plugins/Addons | bdgkacbeblomgnaoildjnppjkamgoogc cnlefmmeadmemmdciolhbnfeacpdfbkd pictureinpicture@mozilla.org firefox-compact-light@mozilla.org |
| Allowed Applications/Packages | 7-Zip 22.01 (x64) Mozilla Firefox (x64 en-US) Notepad++ (64-bit x64) Microsoft Office Standard 2016 Sublime Text Intel(R) Wireless Manageability Driver Microsoft .NET Runtime - 6.0.9 (x64) Dell Power Manager Service FortiClient VPN Microsoft Office Standard 2016 |
| Allowed Processes/Services | smss.exe csrss.exe wininit.exe services.exe lsass.exe WUDFHost.exe fontdrvhost.exe svchost.exe NetworkManager |
Resource Score Parameters
| Resource | |
|---|---|
| Allowed OS Version | 10.0.22621 |
| Open Ports | 7272 45623 5355 8282 51444 63906 6565 9292 |
| Allowed Browser Plugins/Addons | firefox-compact-dark@mozilla.org expressionist-balanced-colorway@mozilla.org nmmhkkegccagdldgiimedpiccmgmieda |
| Allowed Applications/Packages | Mozilla Firefox (x64 en-US) Microsoft Visual C++ 2013 x64 Additional Runtime - 12.0.40664 Intel(R) Wireless Manageability Driver Microsoft .NET Runtime - 6.0.9 (x64) Java 8 Update 361 (64-bit) Microsoft Visual C++ 2022 X64 Additional Runtime - 14.32.31326 |
| Allowed Processes/Services | WUDFHost.exe winlogon.exe fontdrvhost.exe svchost.exe svchost.exe svchost.exe svchost.exe svchost.exe svchost.exe svchost.exe svchost.exe IntelCpHDCPSvc.exe |
| Device Belongs to Privileged Group | Privileged Devices |
Step 3 - Configuring Trust Score Weightage
Now, John navigates to Admin >> Zero Trust >> Trust Score page to set the weightage value (0-10) for the conditional and the predefined parameters (fetched from the user device and resource via installed agents) for the trust score calculation. For the user trust score and the resource trust score calculation, John sets the below weightage based on the organization's importance.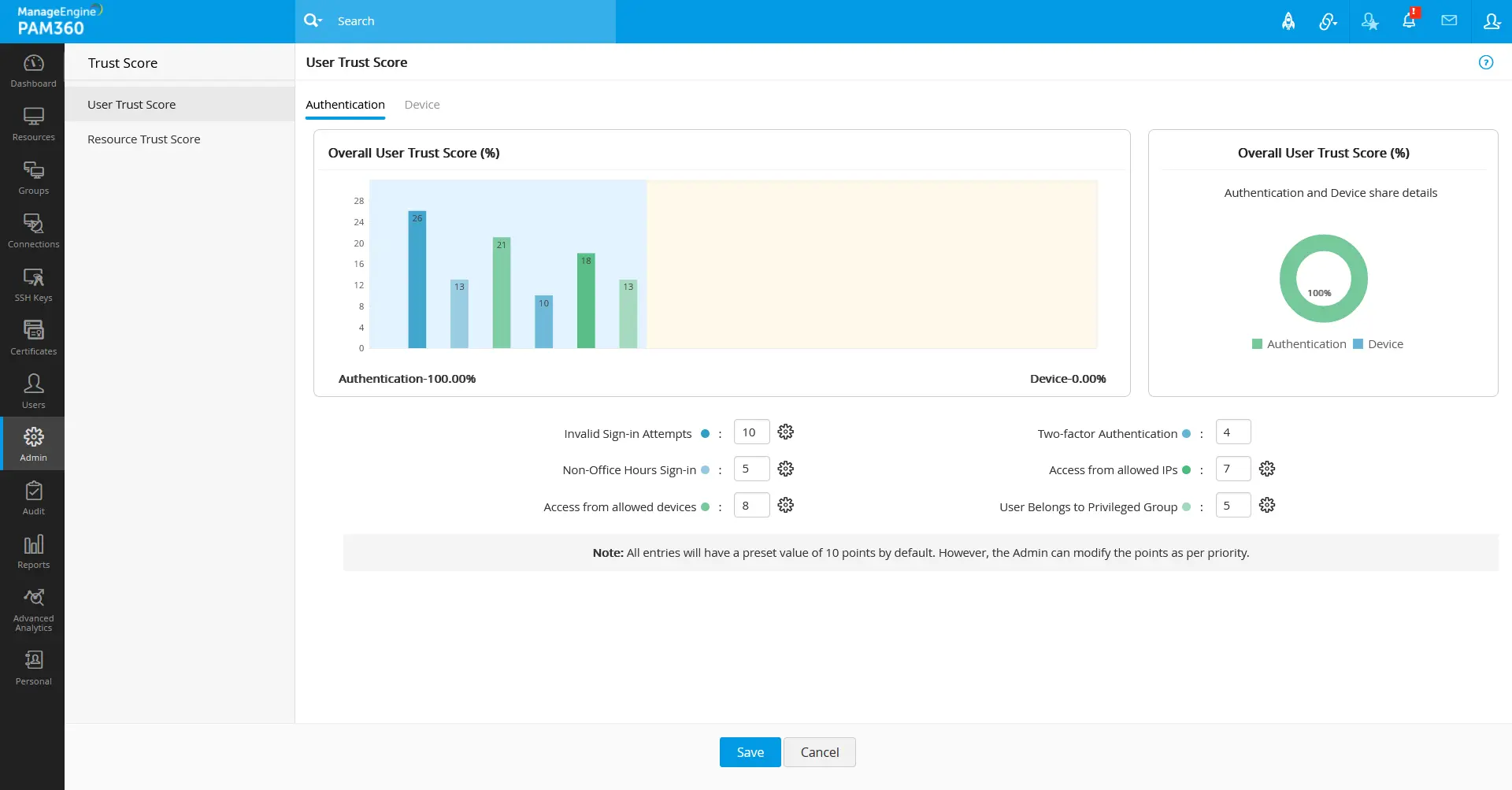
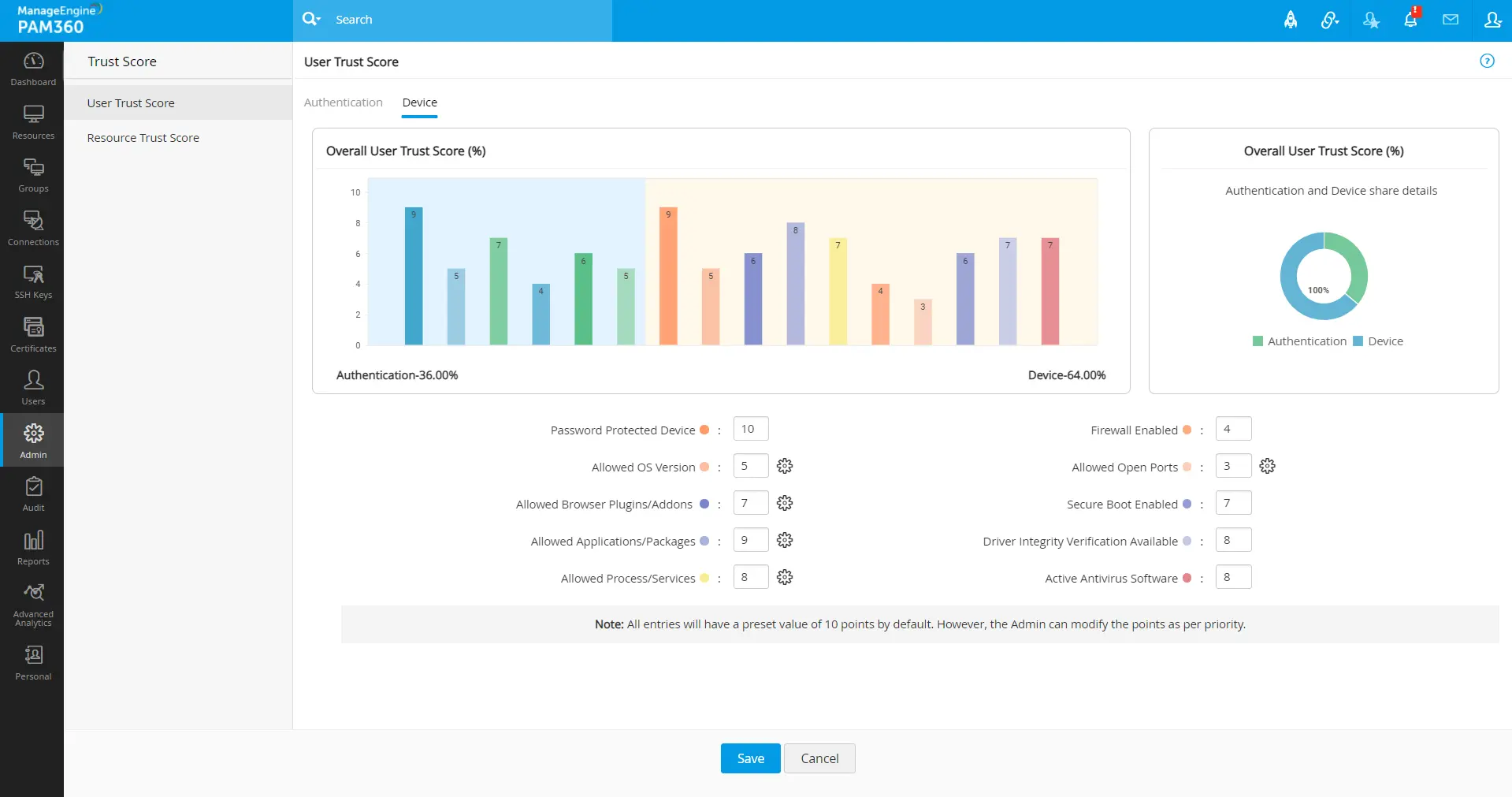
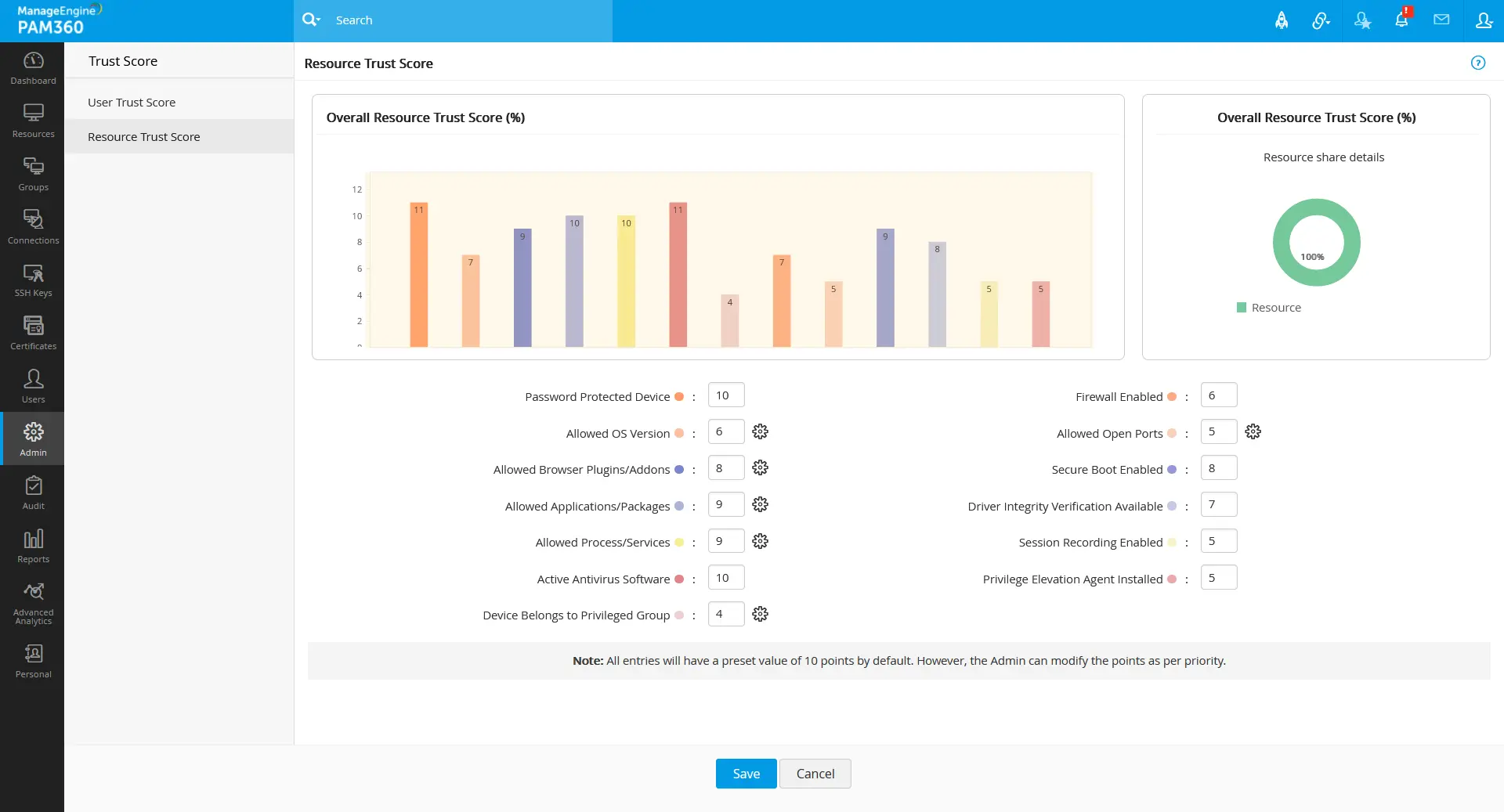
Based on the fixed weightage values in the respective fields, the bar charts will show the points for each parameter. The parameter points will be consolidated and calculated out of 100 as per the value of assigned weightage in the respective fields.
For example, if the user configured under a policy-based access privilege method logged in during non-predefined working hours, as shown in the bar chart, 5 points will be reduced from the user trust score. Similarly, if a privileged device configured under a policy-based access privilege method is not installed with antivirus, as shown in the bar chart, 11 points will be reduced from the resource trust score.
On the Users and Resources tab, the final trust scores for users and resources will be displayed based on all parameters' validation.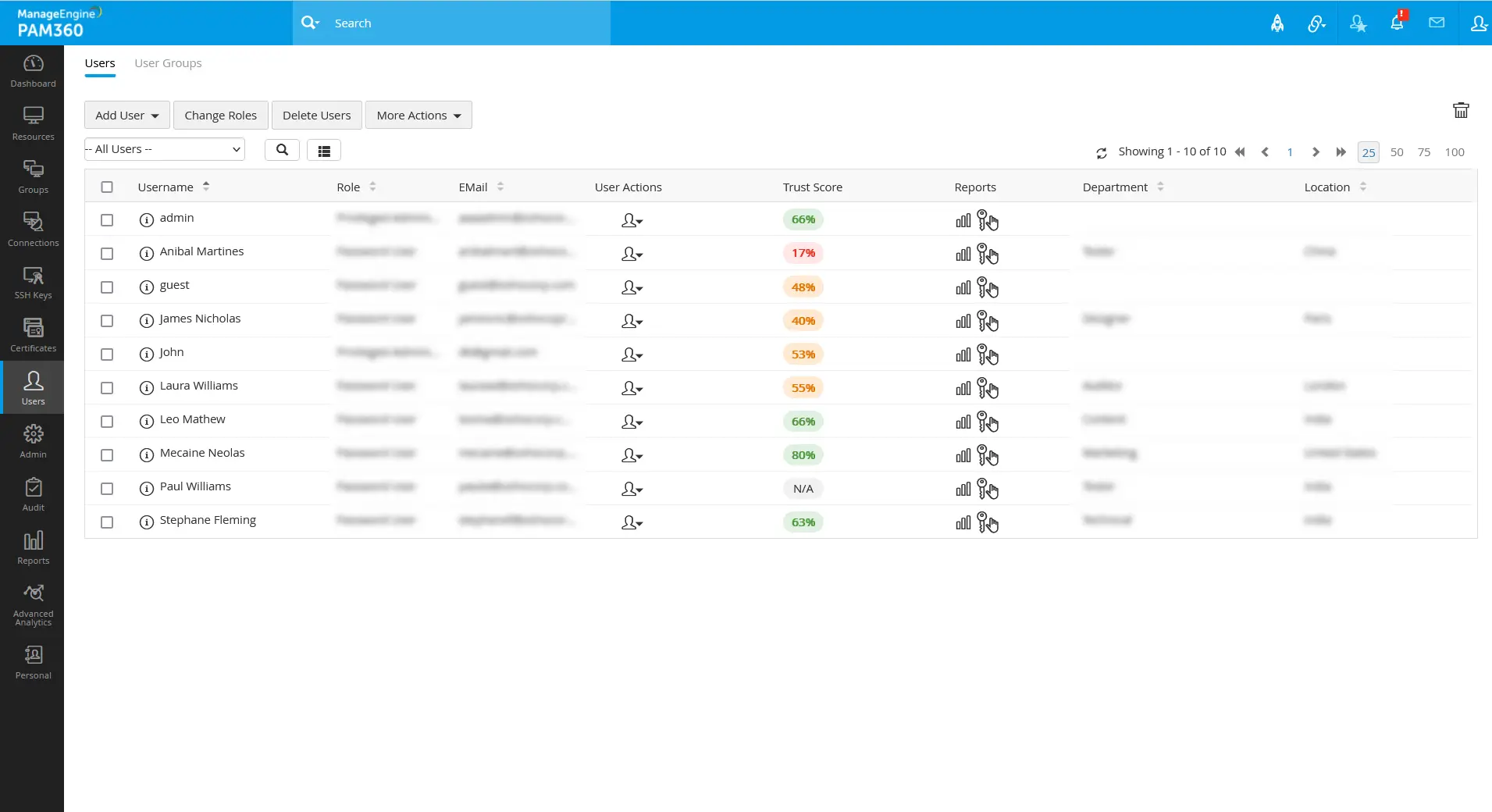
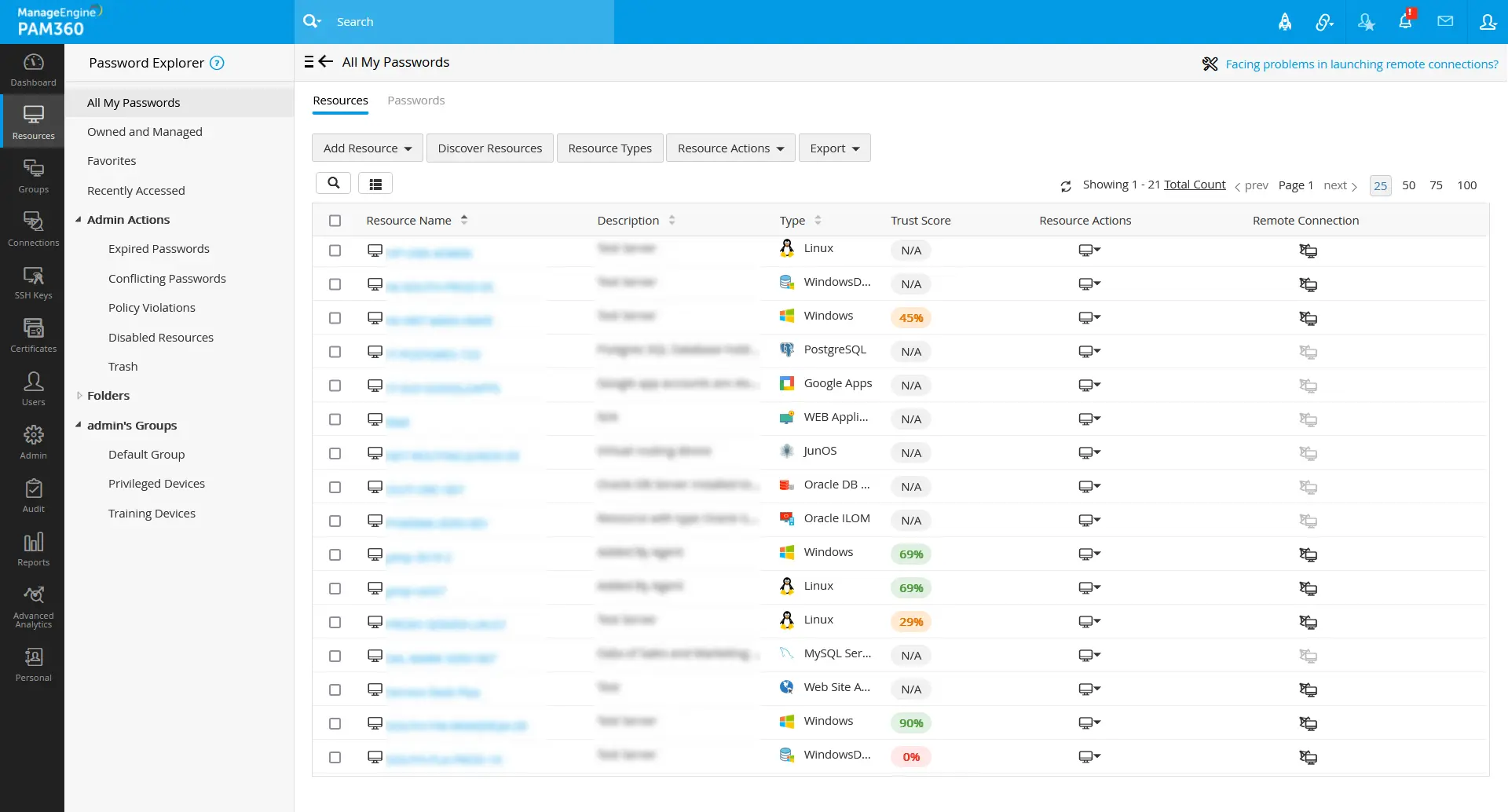
By clicking on the respective trust score value, John can see the parameter that is met or not met by the users as configured by him.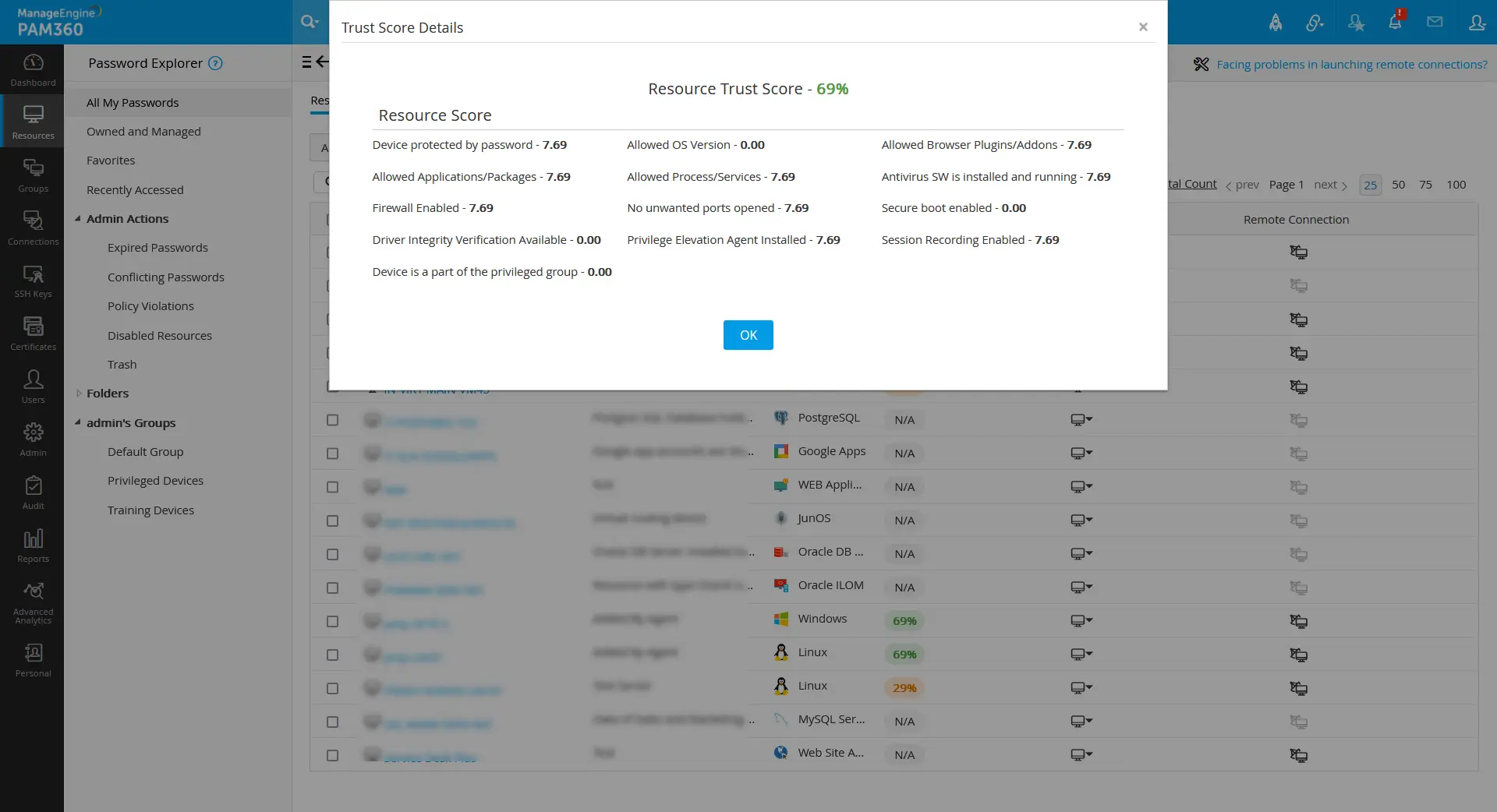
Step 4 - Configuring Zero Trust Access Policies
John now creates the two access policies with multiple conditions based on his organization's requirements. To do so, John navigates to Admin >> Zero Trust >> Access Policy >> Add and adds the below access policies.
1. Privileged Device Policy
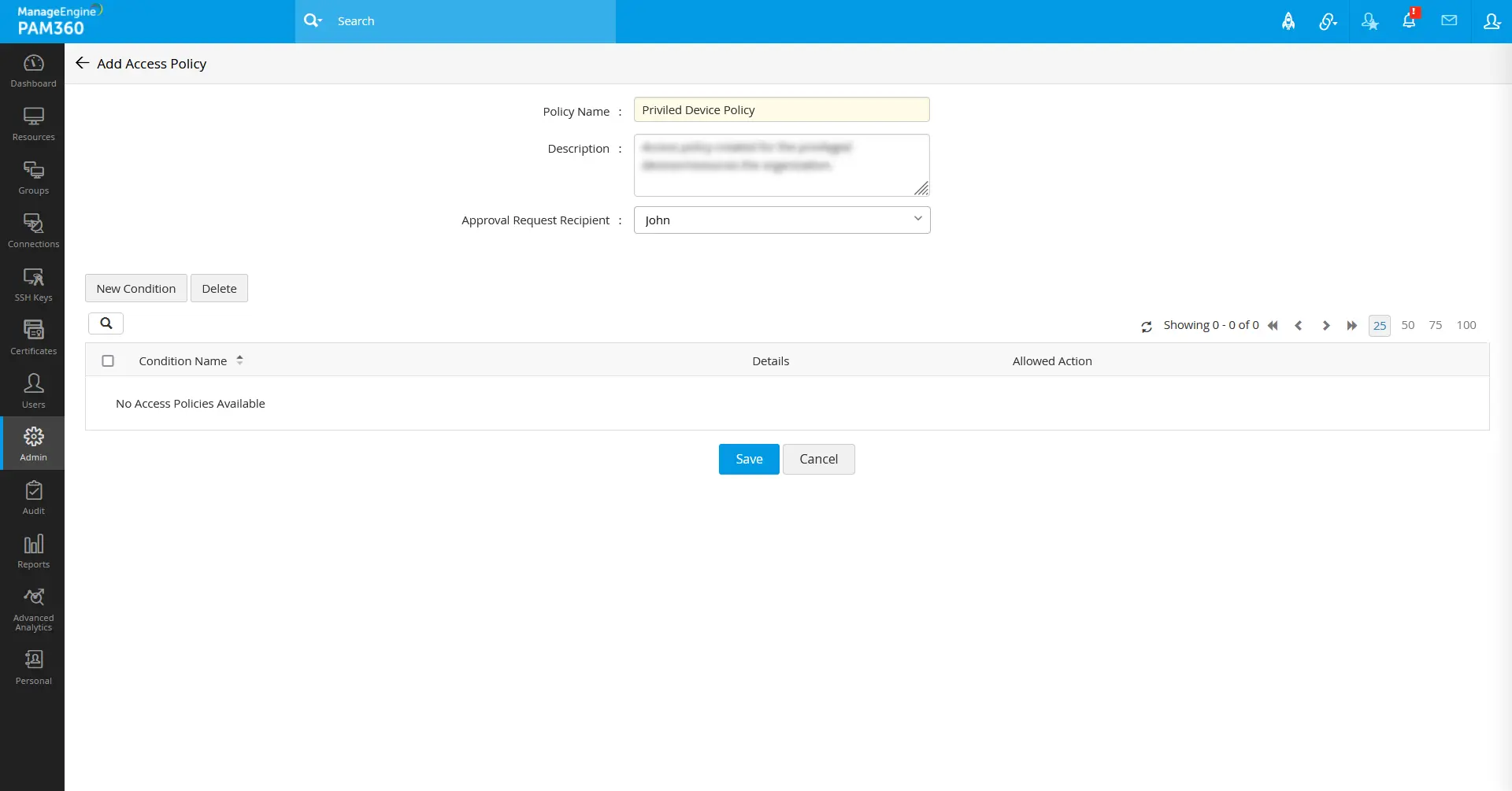
Condition I:
For the users from the Privileged Users user group, if the user trust score is above 60 and the resource trust score is above 75, provide RDP, SSH, SQL, landing server, remote app, password reset, and privilege elevation access. Else, Request a reason and allow access.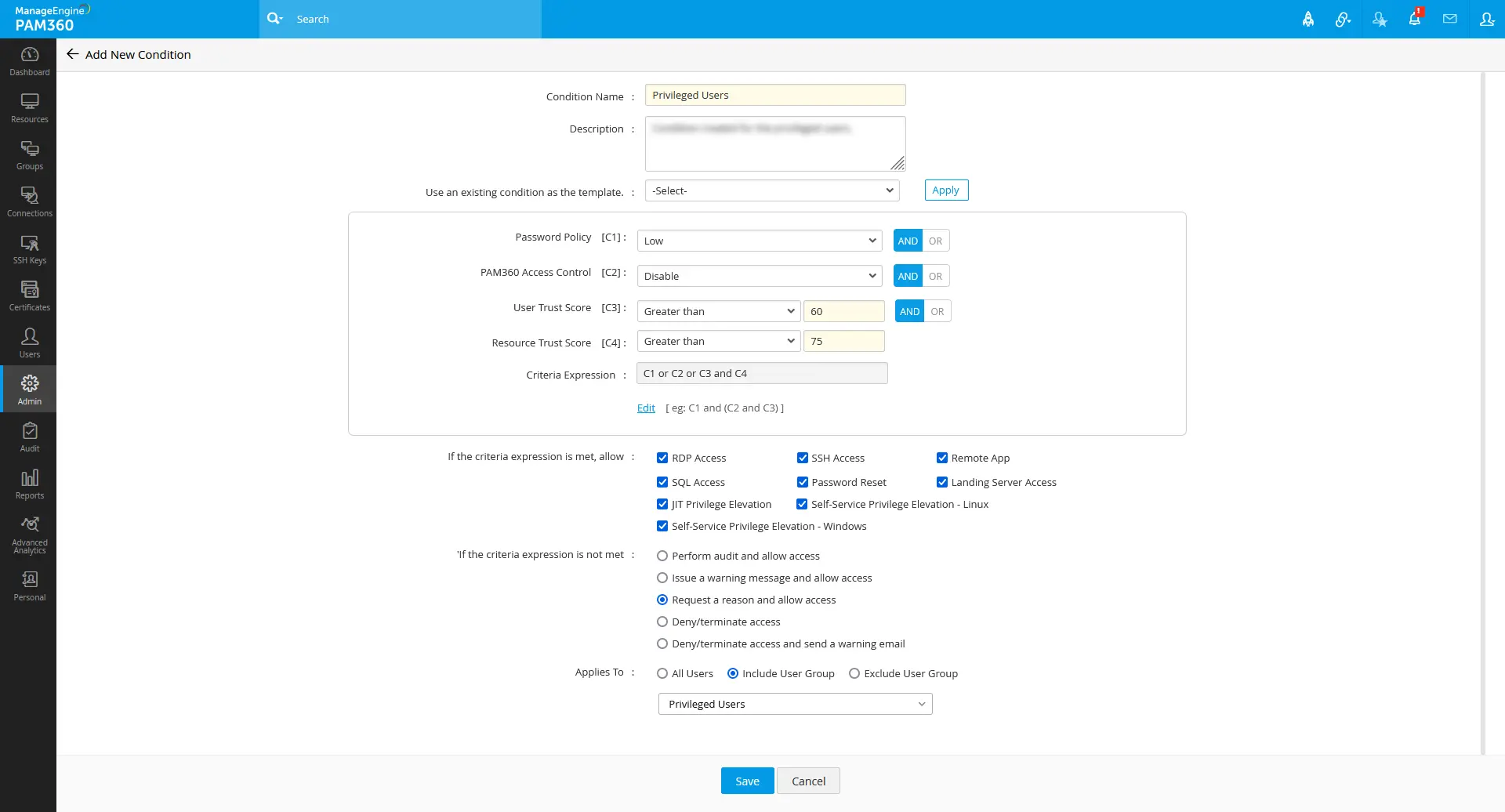
Condition II:
For the users from the Regular Employees user group, if the user trust score is above 75 and the resource trust score is above 85, provide RDP, SSH, SQL, landing server, remote app, and privilege elevation access. Else, Deny /terminate access and send a warning email.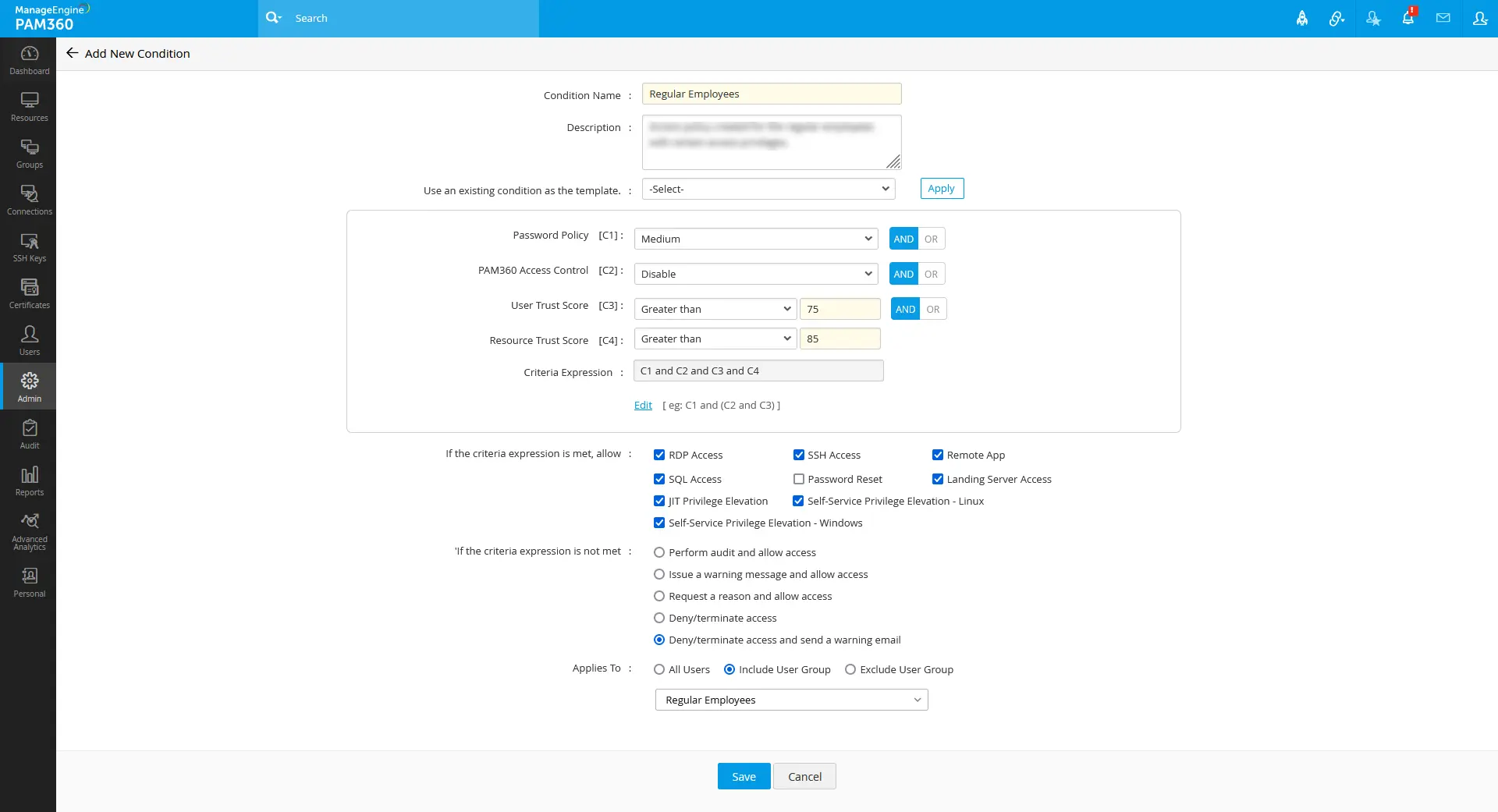
After adding upon the conditions, John selects an approval recipient (another user with the administrator privilege) and saves this access policy for the further approval process.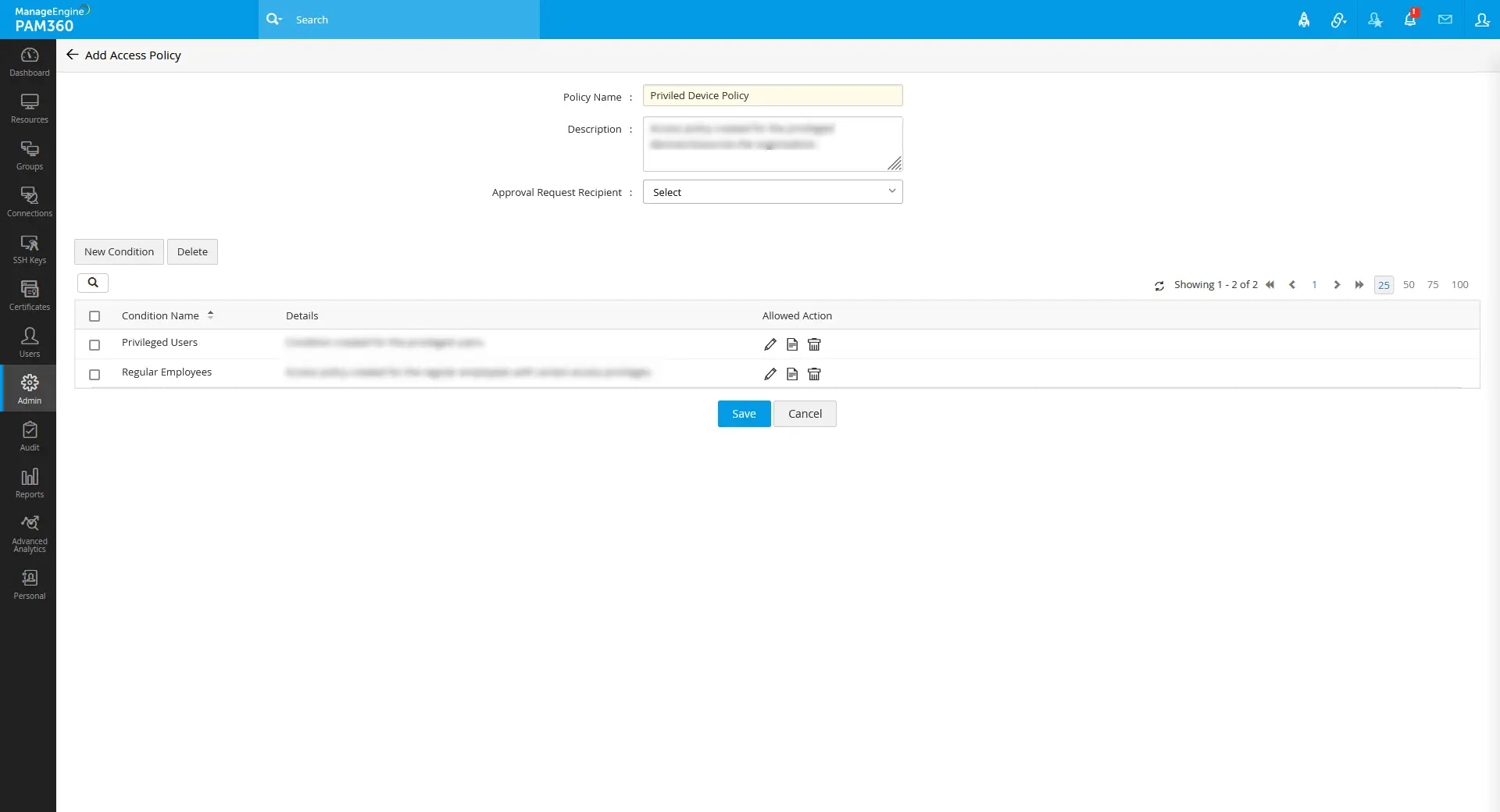
2. Training Policy
Condition I:
For the users from the Privileged Users user group, if the user and resource trust scores are above 50, provide RDP, SSH, SQL, landing server, remote app, password reset, and privilege elevation access. Else, Perform audit and allow access.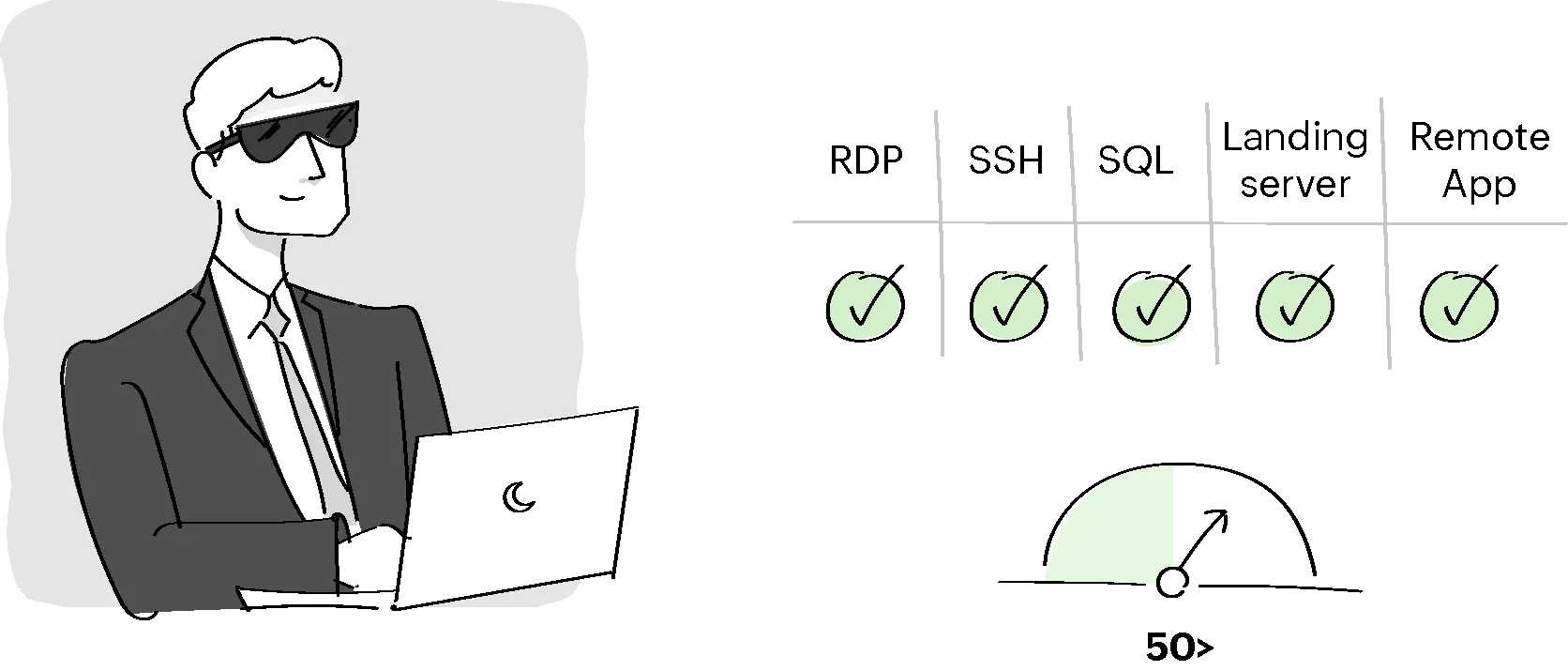
Condition II:
For the users from the Regular Employees user group, if the user and resource trust scores are between 75 and 100, provide RDP, SSH, SQL, landing server, remote app, password reset, and privilege elevation access. Else, Issue a warning message and provide access.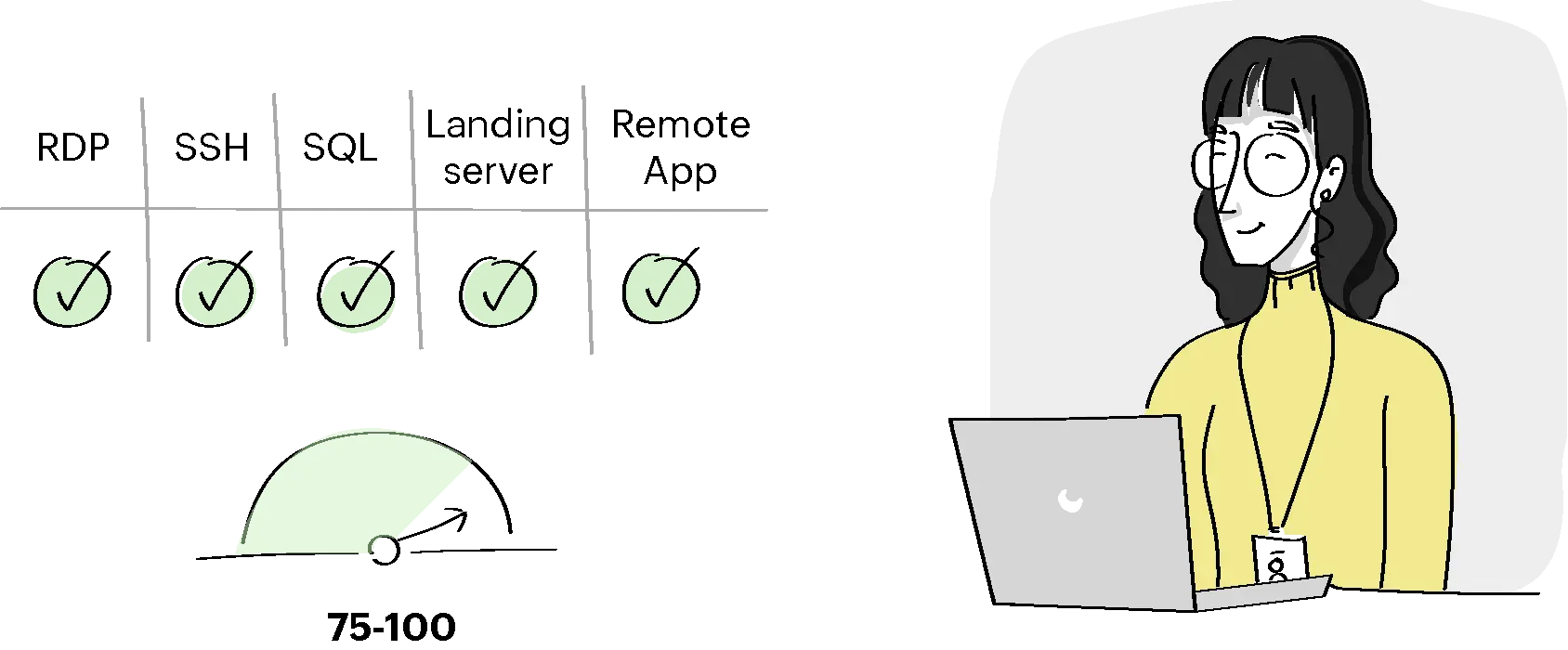
Condition III:
For the users from the Interns and Trainees user group, user and resource trust scores are between 80 and 90, provide RDP, SSH, and SQL access. Else, Deny / Terminate access and send a warning email.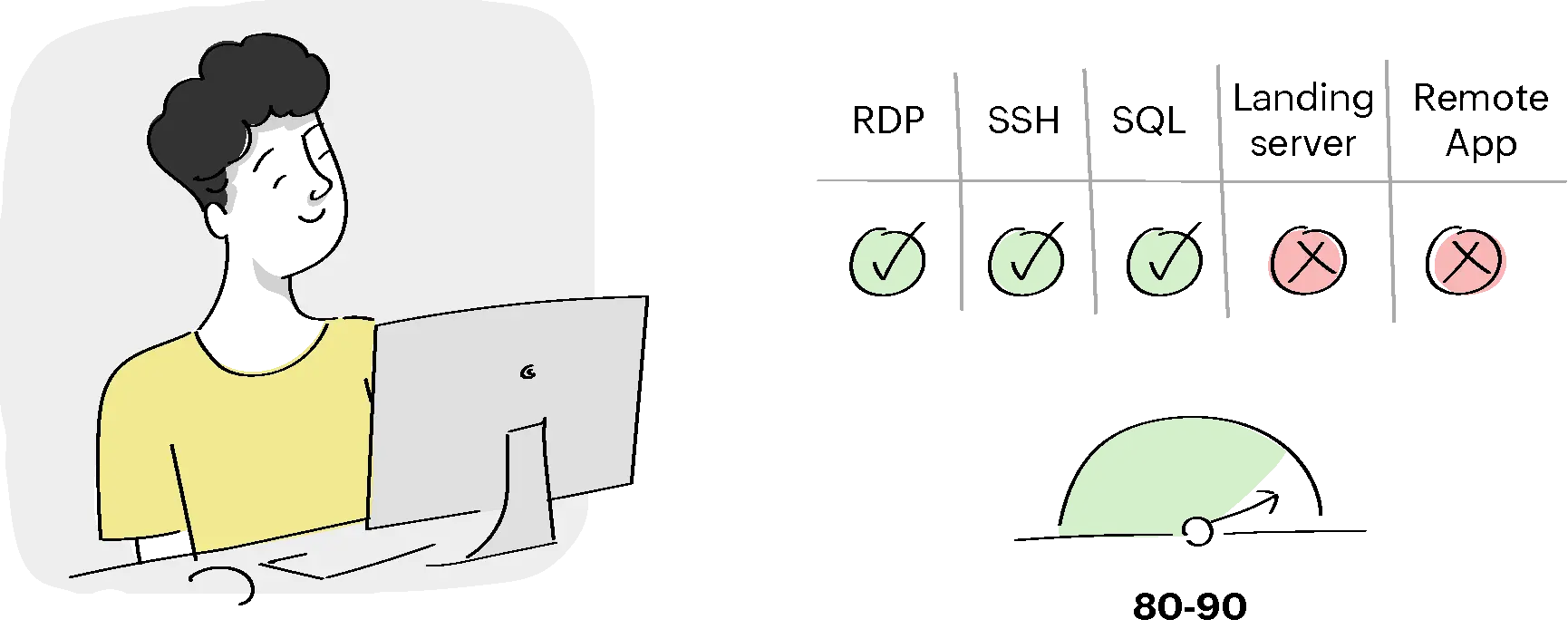
John adds the above conditions for the training devices and saves the access policy with the approver detail. Once the selected approvers of each access policy approve the access policies, John can further proceed with associating the access policies to the respective static resource groups.
Step 5 - Associating Access Policies with Static Resource Groups
John now navigates to the Groups tab and associates the configured Zero Trust access policies with the respective resources via static resource groups. John will associate the access policy Privileged Device Policy with the resource group Privileged Devices and the access policy Training Policy with the resource group Training Devices based on the prerequisites.
Upon completing the above steps, the policy-based access privilege method will be active for the organization via PAM360 using the Zero Trust approach.
Step 6 - Resolving Conflicts between Access Policies
In some scenarios, the few resources are grouped in multiple static resource groups with diverse access policies. In such cases, resources grouped in more than one resource group may result in conflict if their access policies are different.
Consider a case where another administrator in the organization creates a new static resource group with a new access policy of multiple conditions that includes five of the 70 privileged devices of the organization. The access policy for those five devices will automatically be changed to the newly applied access policy via a different resource group and displayed in the Conflict Resolver.
Now, John or the other administrator navigates to Admin >> Zero Trust >> Conflict Resolver and changes the access policy at the resource level from the Actions option beside the respective resource based on their final decision over the respective access policy.
2. How Policy-Based Access Privilege Benefits an Organization - Use Cases
Scenario 1
Detail - Consider an organization with an Offshore Development Center (ODC) for product maintenance and management purpose. According to the organization's ODC policies, the users are allowed only to work in their respective time zones and network with their assigned resources and are restricted from using external devices for project purposes.
Case - The administrator has configured the policy-based access with the predefined parameters based on the ODC policies. A user of the organization has forgotten to complete a few application processes and tries to access it outside the network with an external machine on an open network, which might result in external intrusions and affect the project design and data.
Zero Trust Action - Through the policy-based access privilege method, the parameters such as - Non-Office Hour Sign-in, Accessing from allowed IPs, etc., fail to meet the predefined conditions, thus decreasing the user trust score values, thus further resulting in restricting the user to access the privileged devices in the organization.
Scenario 2
Detail - Imagine an organization with enormous privileged resources with more than one account in each. All those resources are shared with the organization users for internal project requirements and purposes via the PAM360 Zero Trust approach.
Case - Consider a resource 'pam-demo-machine' shared with different users for performing privileged actions. A user with access to the resource installs an application and starts the application process that was block-listed by the administrator. The installed application has malware and is ready to be moved into the organization's network by disabling the antivirus and other device defenders.
Zero Trust Action - The application installed by the user deviates from the configured Zero Trust policy-based access by failing to meet the predefined parameters such as - Allowed Applications/Packages, Allowed Processes/Services, Antivirus Antivirus Software is installed and running, Firewall Enabled, etc. This results in reduced device score values, thus resulting in live session termination and also restricting other shared users from using that particular resource to avoid further data breaches and cyber-attacks.