Configuring Single Sign-On using SAML 2.0 for Okta
ManageEngine PAM360 integrates seamlessly with Okta to provide robust and secure Single Sign-On (SSO) capabilities. Organizations can centralize user authentication and streamline access management by configuring PAM360 as a Service Provider (SP) and Okta as an Identity Provider (IdP). This integration involves supplying details about SP to IdP and vice-versa. This integration enhances security by leveraging Okta's advanced authentication mechanisms. It simplifies the user experience by allowing users to log in once via Okta and gain access to PAM360 without re-authentication. Additionally, the integration supports Single Logout (SLO), ensuring that when users log out from one application, they are automatically logged out from all connected applications, thereby maintaining secure and efficient user session management. This document covers the following topics in detail:
- Prerequisites
- Adding PAM360 as an Application on the Okta Dashboard
- Assigning PAM360 Application to Users
- Downloading Okta IdP Metadata File
Follow these steps to seamlessly integrate PAM360 with Okta, enabling a smooth and secure SSO and SLO experience.
1. Prerequisites
To configure PAM360 as an SP on the Okta dashboard, you need SP details displayed in step 1 during theIdP configuration in PAM360. These details are necessary for setting up PAM360 as an SP on the Okta dashboard, ensuring a seamless integration between PAM360 and Okta.
2. Adding PAM360 as an Application on the Okta Dashboard
Follow these steps to add PAM360 as an application on the Okta dashboard and configure the SAML settings.
- Log in to the Okta Admin Console with administrator credentials.
- Select Applications from the left pane and click the Create App Integration button on the Applications page.
- In the Create a new app integration window that opens, select SAML 2.0 and click Next. You will see the Create SAML Integration page.
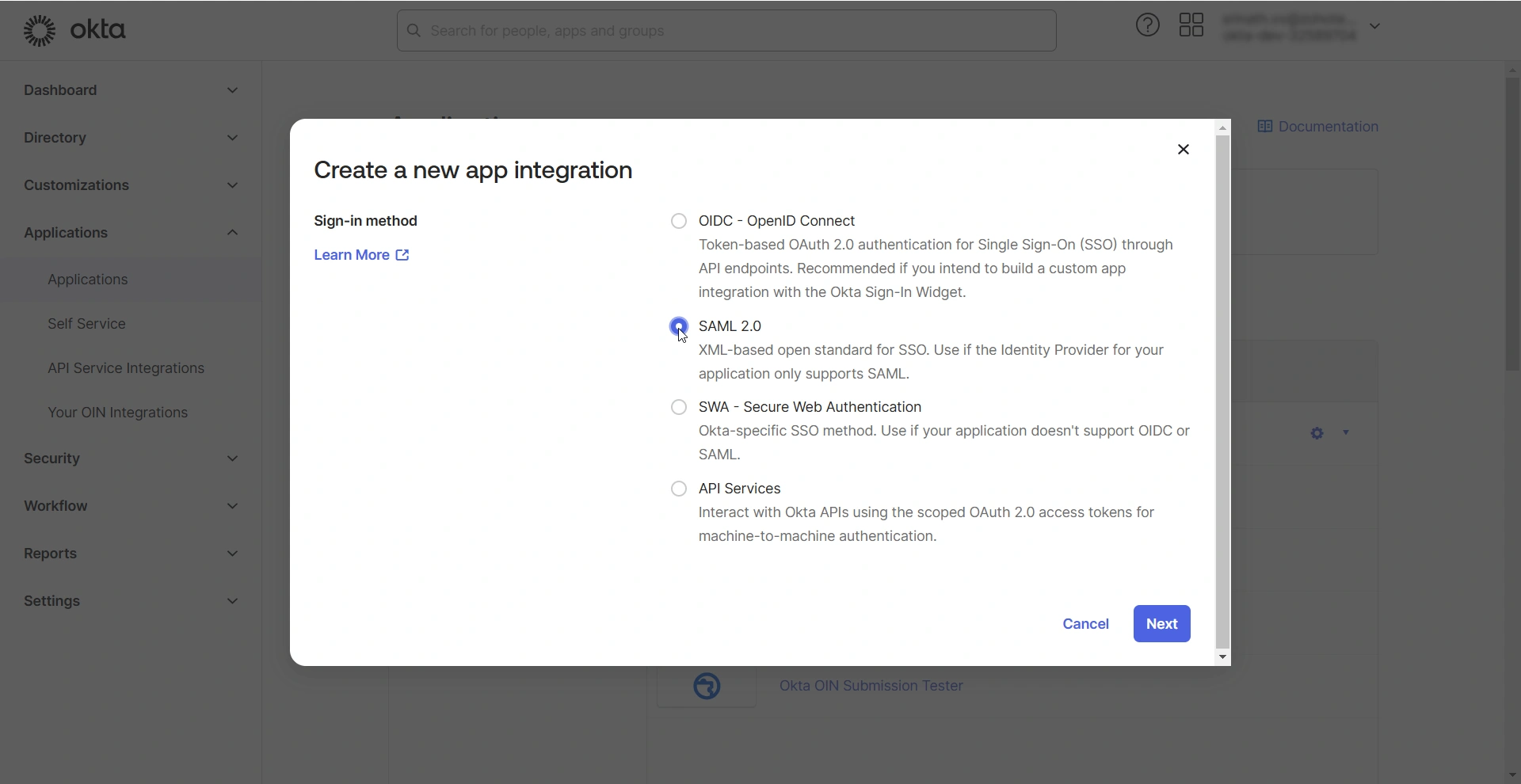
On the Create SAML Integration page, you should complete the following configurations: General Settings and Configure SAML.
2.1 General Settings
On the Create SAML Integration page, under General Settings, you should provide essential information about the application you are adding. Follow these steps to complete this section:
- Enter a name of your choice in the App name field. This name will serve as a unique identifier for PAM360 on the Okta dashboard.
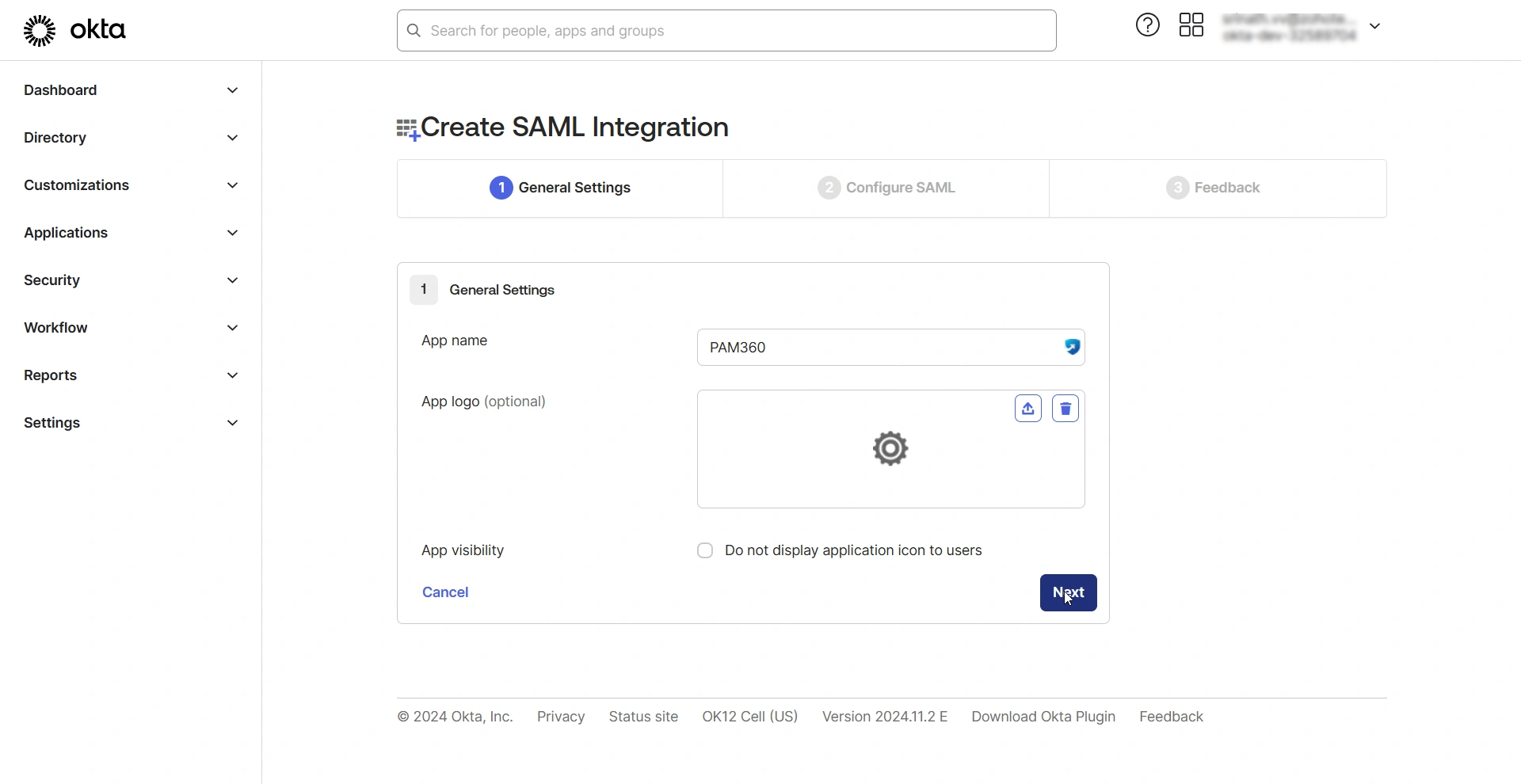
- If you wish to upload a logo for the application, click the Upload new icon beside the App logo field, click Browse files, choose an image from your machine, and click Apply.
- Enable the App visibility checkbox if you do not wish to display the application icon to users.
- Click Next to continue to the next step.
2.2 Configure SAML
On the Configure SAML window, under SAML Settings, enter the following details.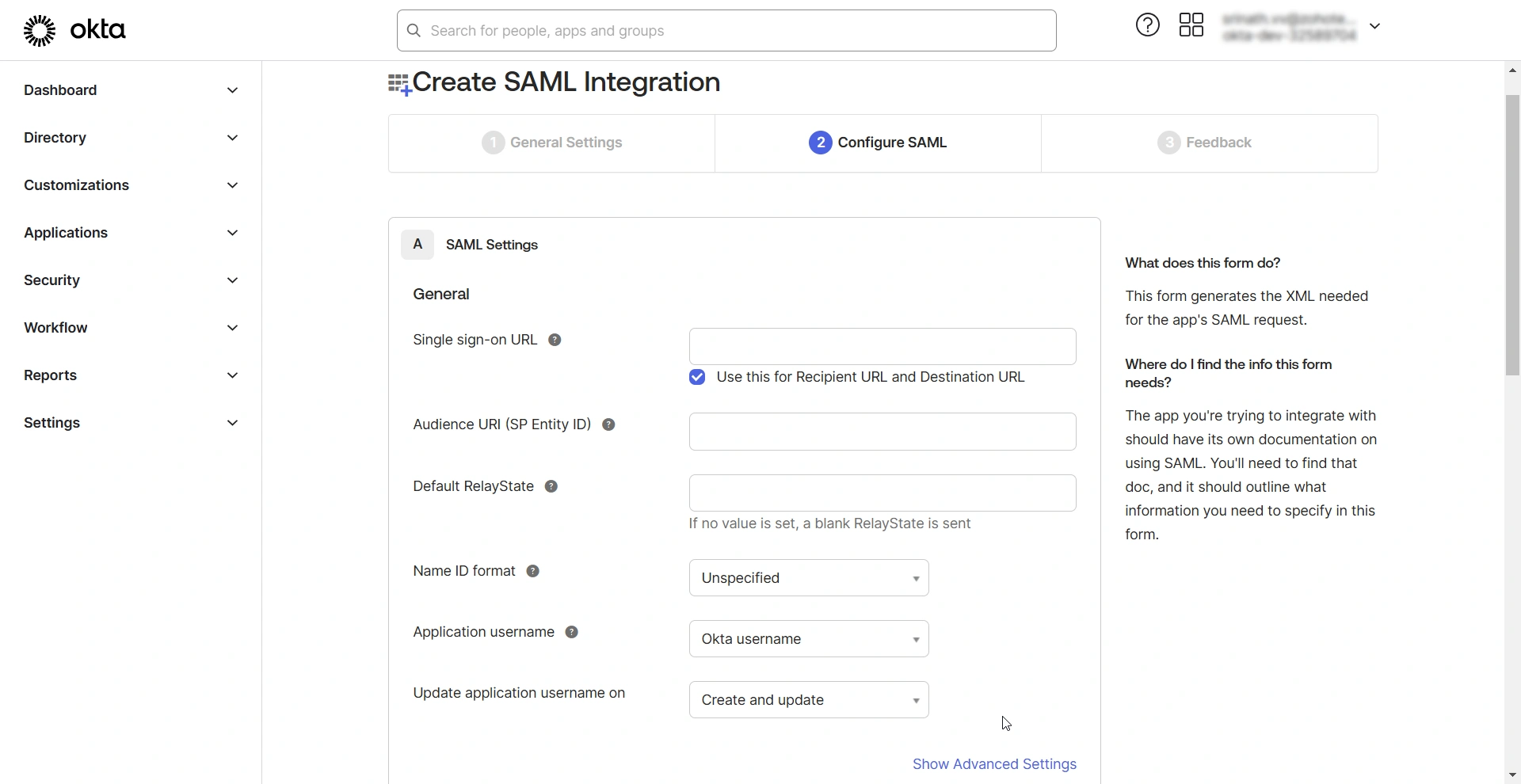
- Single sign-on URL - Enter PAM360's Assertion Consumer Service (ACS) URL in this field.
- For MSP, enter the ACS URL in the https://<pam-access-url>/saml2 format, and tick the Use this for Recipient URL and Destination URL checkbox.
- For client organizations, enter the ACS URL in the https://<pam-access-url>/saml2?ORGN_NAME=<org_name> format and enter the recipient and destination URLs as follows:
- Recipient URL - https://<pam-access-url>/saml2
- Destination URL - https://<pam-access-url>/saml2
- Audience URI (SP Entity ID) - Enter the PAM360's entity ID in this field.
- Default RelayState - Leave this field blank.
- Name ID format - Select Unspecified from the drop-down field.
- Application username - Select None from the given options.
- Click the Show Advanced Settings button to reveal advanced SAML properties.
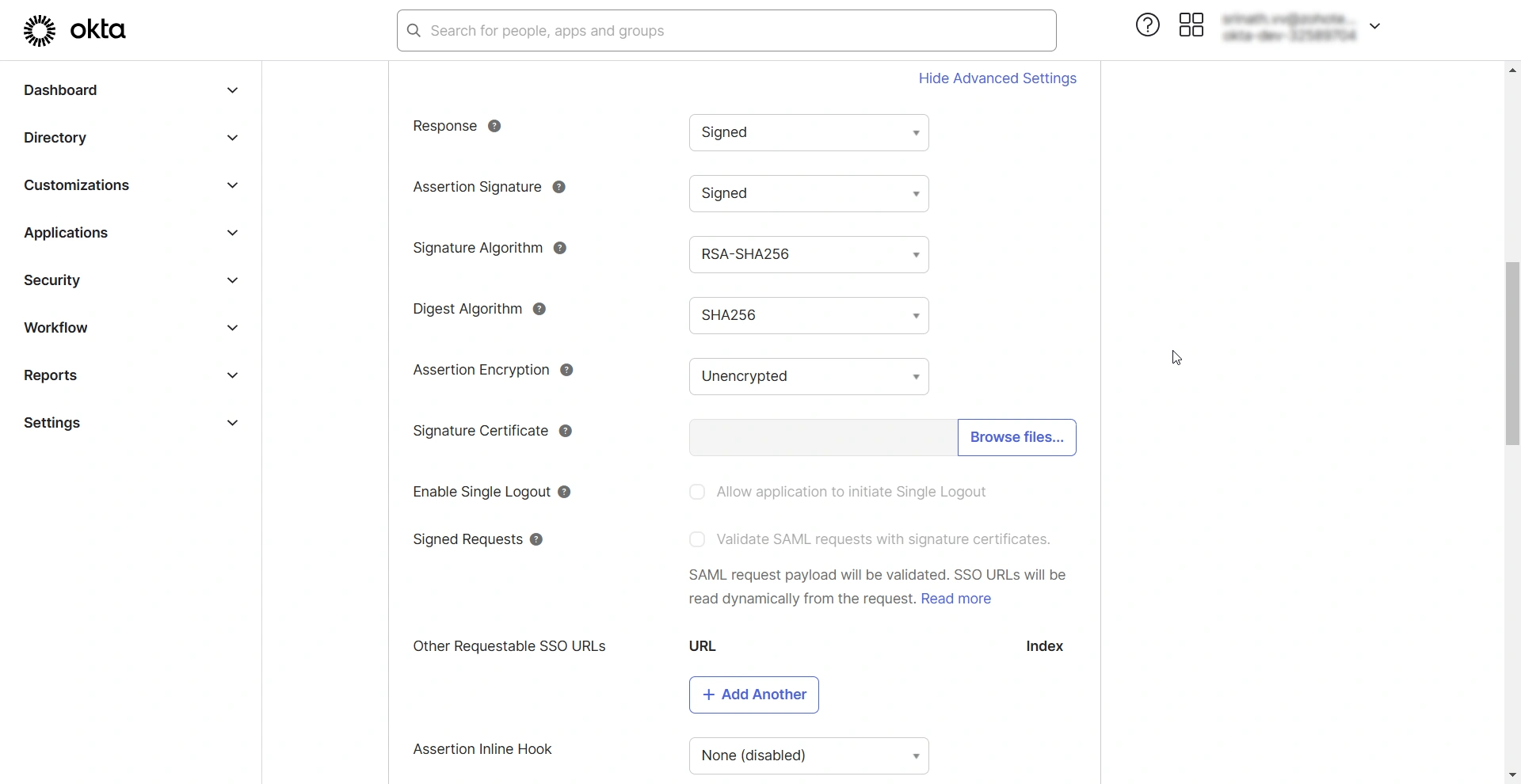
- Response - Choose Signed or Unsigned from the drop-down field. If you choose Signed, the IdP will sign the SAML responses sent to PAM360.
- Assertion Signature - Choose Signed or Unsigned from the drop-down field. If you choose Signed, the IdP will sign the SAML assertions sent to PAM360.
- Signature Algorithm - Select the digital algorithm to sign the SAML assertion and response.
- Digest Algorithm - Select the digest algorithm to sign the SAML assertion and response.
- Assertion Encryption - Choose whether the SAML assertion sent by the IdP should be encrypted. If you choose Encrypted, select the appropriate Encryption Algorithm and Key Transport Algorithm from the respective drop-down fields.
- Signature Certificate - Upload the PAM360 certificate in this field.
- Enable Single Logout - Tick this checkbox to allow PAM360 to send single logout requests. When Single Logout is enabled, users can log out of PAM360, terminating all active sessions established with SSO.
- Single Logout URL - Enter the PAM360's Single Logout Service URL in this field.
- SP Issuer - Enter the PAM360's entity ID in this field.
- Signed Requests - Enable this checkbox to validate the SAML requests received from PAM360.
- Authentication context class - Select the desired authentication class from the drop-down field.
Caution
Ensure the Authentication Context Class selected during SAML SSO configuration is consistent across the IdP and the SP. Any mismatch in the selected options can result in authentication failures or unpredictable behavior.
- Honor Force Authentication - Select Yes if you wish to re-authenticate users when they access PAM360, even if they have an active session with Okta (IdP).
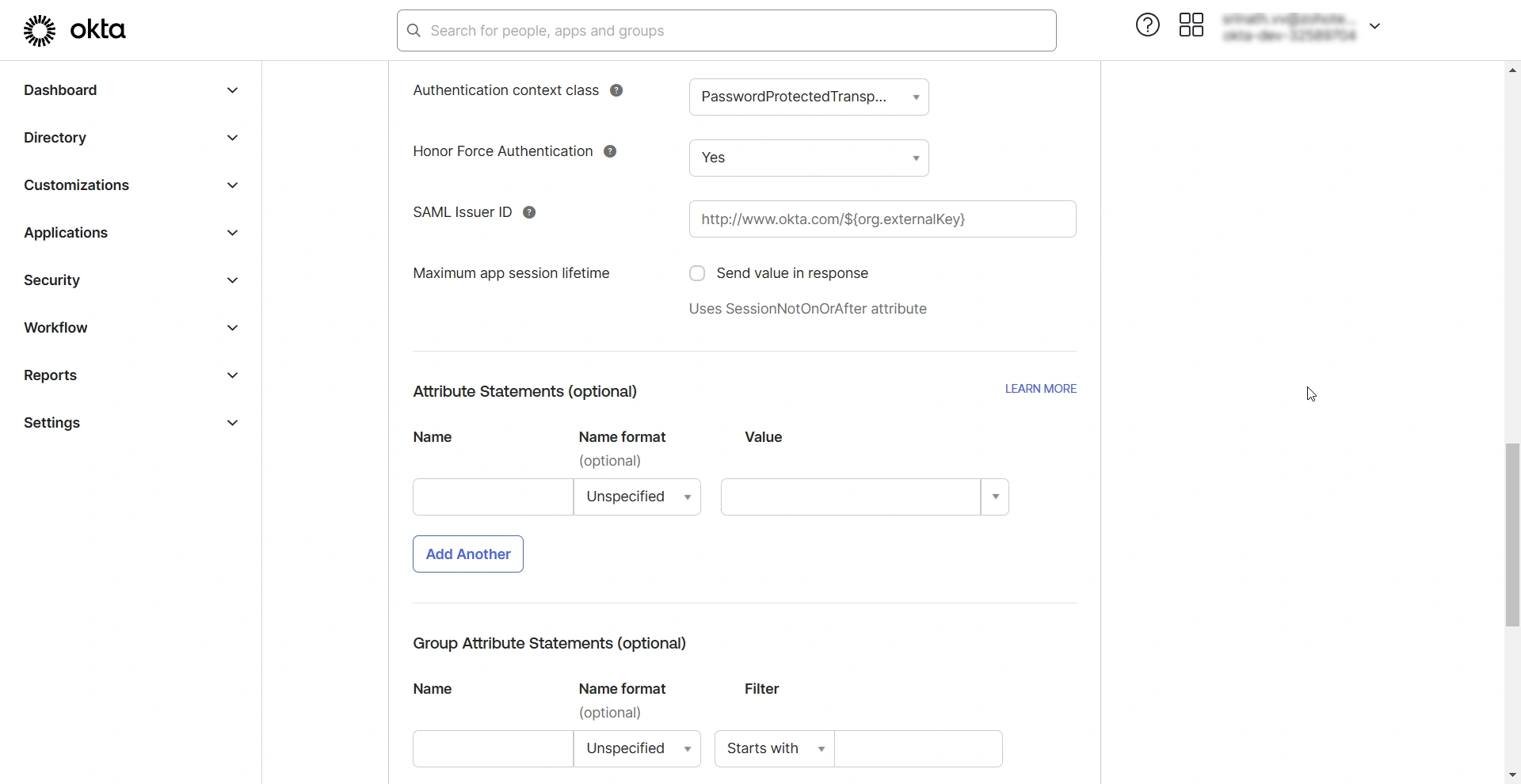
After configuring the SAML properties, specify the Attribute Statements. The attribute statement is a crucial part of the SAML assertions that provides information about the authenticated user. PAM360 identifies the user by cross-referencing the attribute within the attribute statement with its username before granting access to the user. As the usernames in Okta and PAM360 could be different, you must specify the format. There are two possible scenarios:
- If you have users imported from AD in your PAM360 environment, their username will be in the format Domain\Username (Email ID prefix). In Okta GUI, under Attribute Statements, specify the following details:
- Name: Enter a name for the attribute statement, e.g., AD users.
- Name Format: Choose Unspecified from the available options.
- Value: toUpperCase(substringBefore(substringAfter(user.email, "@"), ".")) + "\" + substringBefore( user.email, "@")
- If you do not have an AD integration, enter the value as substringBefore(user.email, "@") because, in Okta, user profiling is done in the format username@domain.com. But, in PAM360, user names are depicted only as usernames (Email ID prefix).
Caution
The name of the custom NameID attribute created on the Okta console should be entered in the NameID Attribute field under Step 3: Configure SAML Properties while configuring Okta as a trusted IdP in PAM360.
After configuring the required parameters, click the Preview the SAML Assertion option to review a sample of the SAML assertion that will be sent by the IdP to PAM360. Then, click Next to proceed to the next step. Complete the feedback questionnaire and click Finish to finalize the SP configuration and SAML parameters on the Okta dashboard.
3. Assigning PAM360 Application to Users
After setting up the newly added application integration (PAM360), you must assign it to the users in your Okta directory.
- Access the Applications page from the left pane and click the Assign Users to App button.
- In the Assign Applications page, under the Assign Apps to People tab, select the PAM360 application under the Applications section and select the desired users for whom you wish to provide access to the PAM360 integration under the People section.
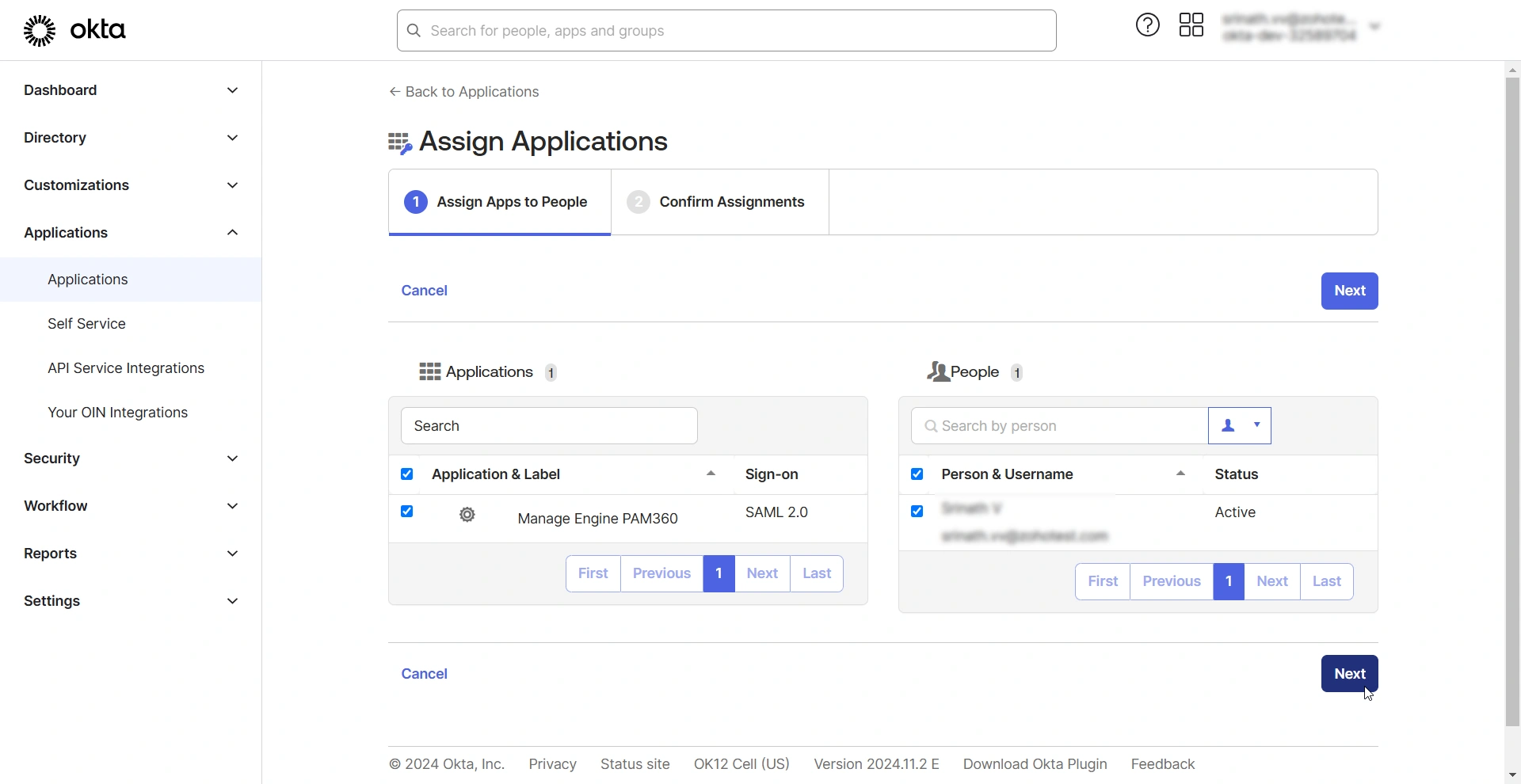
- After selecting the users, click Next to continue.
- In the Confirm Assignments tab, review the application and the assigned users.
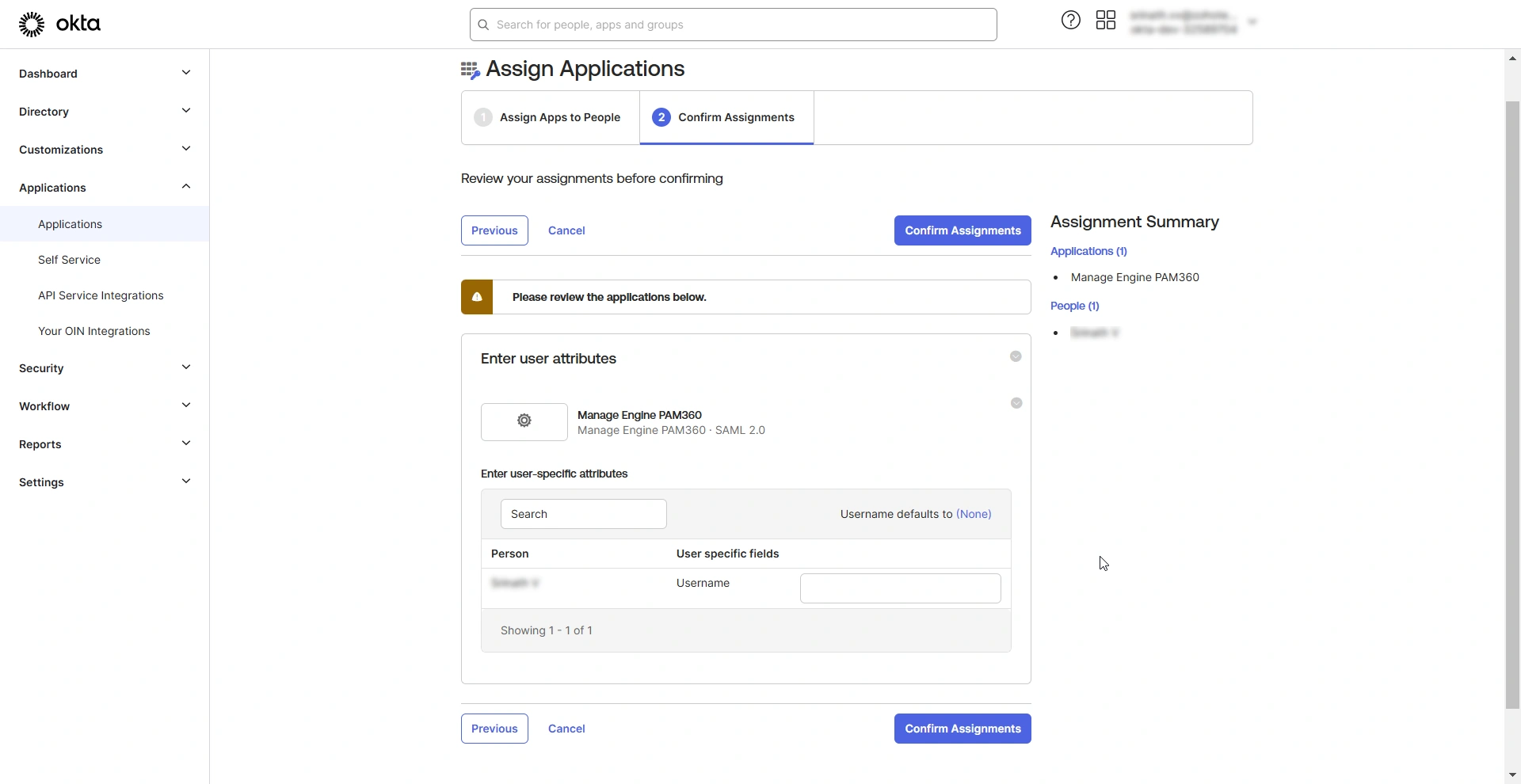
- Click the Confirm Assignments button to assign the selected users to the PAM360 application integration.
After configuring PAM360 as an SP in Okta, you must configure Okta as an IdP in PAM360 to establish it as a trusted entity. Access the PAM360 browser window and proceed with the IdP configuration starting from Step 2 - Configure Identity Provider Details. Explore this link for the detailed IdP configuration steps. Based on the provided steps, configure Okta as an IdP and define the SAML properties on the PAM360 interface.
4. Downloading Okta IdP Metadata File
Follow these steps to download the IdP details as a metadata.xml file after configuring PAM360 as an SP.
- Access PAM360 integration from the Applications page.
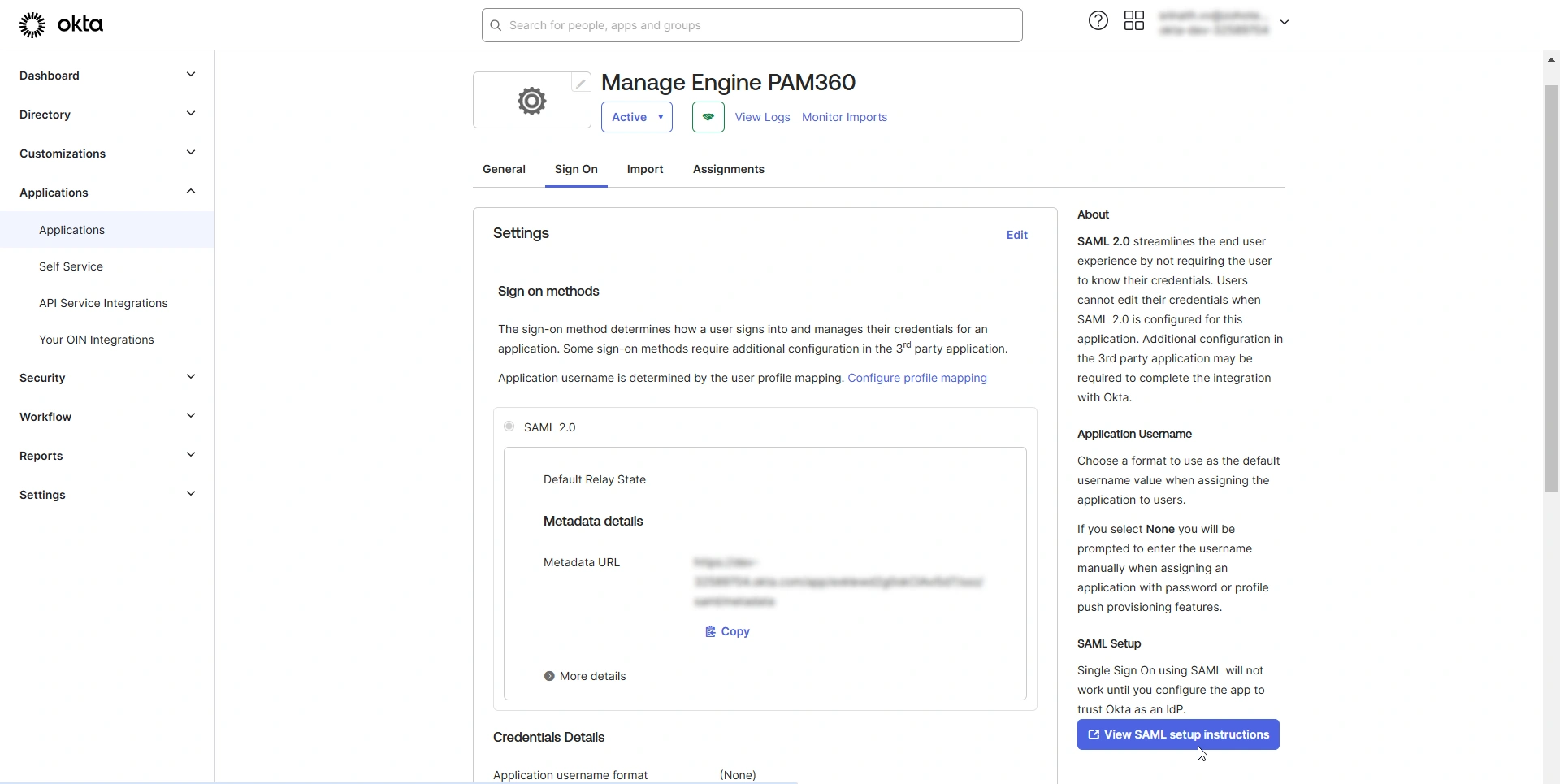
- On the PAM360 integration page, switch to the Sign On tab and click the View SAML setup instructions option. In the SAML setup instructions page, you will find all the necessary details to configure Okta as an IdP on the PAM360 interface.
- Scroll down to the end of the page and find the Optional field. Copy the metadata provided in this field and save it as an XML file.
- Now, you can upload this XML file while configuring the IdP details on the PAM360 interface, eliminating the need to enter all the IdP information manually.