SSH provides a secure method for connecting to remote systems over unsecured networks. It establishes a secure channel between the client and server, ensuring confidentiality, integrity, and authentication of data.
Utilizing cryptographic methods, SSH guarantees encrypted communication between the user and the remote server. This protocol offers authentication for remote users, facilitates the transmission of client inputs to the host, and sends the corresponding outputs back to the client in a secure manner.
Here's an overview of how SSH communication works, including the role of ciphers and algorithms:
During the above tasks, both client and server will share the algorithms to be used for each operation. Once they find a mutually supported algorithm, an SSH connection will be established.
To access the SSH Connection Settings, go to Settings → Performance Polling → SSH Connection Settings. Upon initialization, the system will automatically choose all accessible ciphers, ensuring their utilization for SSH communication.
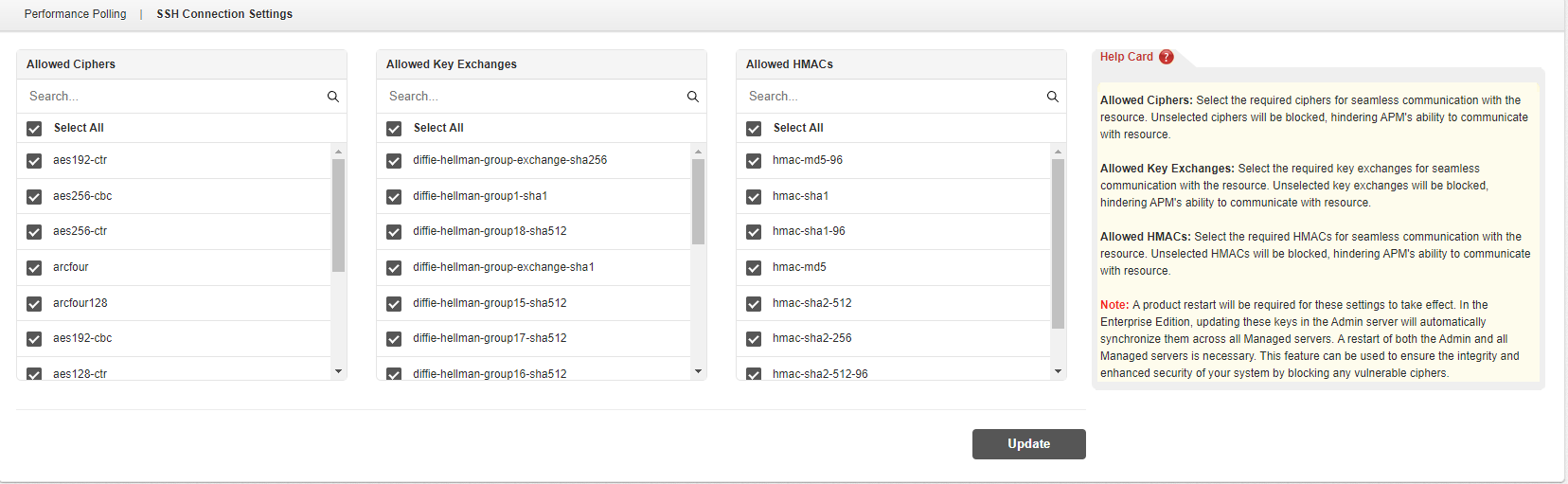
Guarantee the security and integrity of your system by preventing the use of vulnerable ciphers. Disable any weak ciphers by deselecting SSH ciphers, key exchanges, and HMACs following the outlined steps below:
Thank you for your feedback!